If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ______ layer(s) of the TCP/IP model and up to and including the ______ layer.
An administrator can use section titles to more easily navigate between large rule bases. Which of these statements is FALSE?
Which of the following is NOT supported by Bridge Mode on the Check Point Security Gateway?
John is using Management HA. Which Smartcenter should be connected to for making changes?
When an Admin logs into SmartConsole and sees a lock icon on a gateway object and cannot edit that object, what does that indicate?
In a Distributed deployment, the Security Gateway and the Security Management software are installed on what platforms?
To view statistics on detected threats, which Threat Tool would an administrator use?
The default shell of the Gaia CLI is cli.sh. How do you change from the cli.sh shell to the advanced shell to run Linux commands?
Which one of the following is the preferred licensing model? Select the BEST answer
Which Security Blade needs to be enabled in order to sanitize and remove potentially malicious content from files, before those files enter the network?
Which method below is NOT one of the ways to communicate using the Management API’s?
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
Fill in the blank: The_____is used to obtain identification and security information about network users.
Which of the following is an authentication method used for Identity Awareness?
Most Check Point deployments use Gaia but which product deployment utilizes special Check Point code (with unification in R81.10)?
For Automatic Hide NAT rules created by the administrator what is a TRUE statement?
Which Check Point software blade monitors Check Point devices and provides a picture of network and security performance?
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
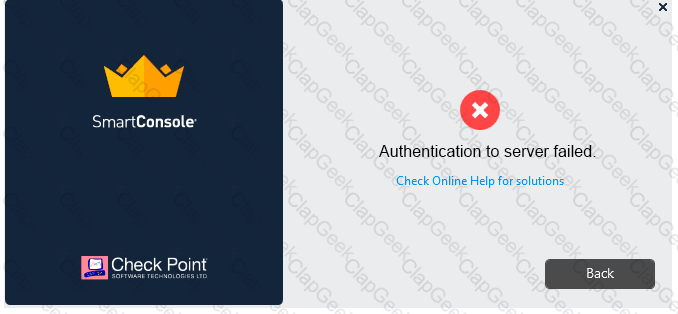
What is the most likely reason?
Gaia has two default user accounts that cannot be deleted. What are those user accounts?
What are two basic rules Check Point recommending for building an effective security policy?
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the:
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
Which of the following statements about Site-to-Site VPN Domain-based is NOT true?
Route-based— The Security Gateways will have a Virtual Tunnel Interface (VTI) for each VPN Tunnel with a peer VPN Gateway. The Routing Table can have routes to forward traffic to these VTls. Any traffic routed through a VTI is automatically identified as VPN Traffic and is passed through the VPN Tunnel associated with the VTI.
You want to verify if there are unsaved changes in GAiA that will be lost with a reboot. What command can be used?
When a gateway requires user information for authentication, what order does it query servers for user information?
In R80 Management, apart from using SmartConsole, objects or rules can also be modified using:
Fill in the blank Once a license is activated, a___________should be installed.
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
Fill in the blank: An identity server uses a ___________ for user authentication.
Fill in the blank: It is Best Practice to have a _____ rule at the end of each policy layer.
There are four policy types available for each policy package. What are those policy types?
Which software blade enables Access Control policies to accept, drop, or limit web site access based on user, group, and/or machine?
In which deployment is the security management server and Security Gateway installed on the same appliance?
The competition between stateful inspection and proxies was based on performance, protocol support, and security. Considering stateful Inspections and Proxies, which statement is correct?
Tom has connected to the Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made?
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
Which of the following Windows Security Events will NOT map a username to an IP address in Identity Awareness?
Which is a suitable command to check whether Drop Templates are activated or not?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
Which backup utility captures the most information and tends to create the largest archives?
URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain Why does it not detect the windows domain?
To quickly review when Threat Prevention signatures were last updated, which Threat Tool would an administrator use?
Which one of the following is a way that the objects can be manipulated using the new API integration in R80 Management?
In which scenario is it a valid option to transfer a license from one hardware device to another?
Which of the following log queries would show only dropped packets with source address of 192.168.1.1 and destination address of 172.26.1.1?
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
Session unique identifiers are passed to the web api using which http header option?
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server (SMS). While configuring the VPN community to specify the pre-shared secret, the administrator did not find a box to input the pre-shared secret. Why does it not allow him to specify the pre-shared secret?
The Online Activation method is available for Check Point manufactured appliances. How does the administrator use the Online Activation method?
Which application is used for the central management and deployment of licenses and packages?
The Gateway Status view in SmartConsole shows the overall status of Security Gateways and Software Blades. What does the Status Attention mean?
Fill in the blank: Once a certificate is revoked from the Security GateWay by the Security Management Server, the certificate information is _______.
Which Threat Prevention Software Blade provides comprehensive protection against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
If there is an Accept Implied Policy set to "First", what is the reason Jorge cannot see any logs?
After the initial installation on Check Point appliance, you notice that the Management interface and default gateway are incorrect. Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
You want to store the GAiA configuration in a file for later reference. What command should you use?
To provide updated malicious data signatures to all Threat Prevention blades, the Threat Prevention gateway does what with the data?
What type of NAT is a one-to-one relationship where each host is translated to a unique address?
Identity Awareness lets an administrator easily configure network access and auditing based on three items Choose the correct statement.
Your internal networks 10.1.1.0/24, 10.2.2.0/24 and 192.168.0.0/16 are behind the Internet Security Gateway. Considering that Layer 2 and Layer 3 setup is correct, what are the steps you will need to do in SmartConsole in order to get the connection working?
Which Check Point software blade provides Application Security and identity control?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
Fill in the blank: SmartConsole, SmartEvent GUI client, and ___________ allow viewing of billions of consolidated logs and shows them as prioritized security events.
Which of the following is NOT supported by Bridge Mode Check Point Security Gateway
Which tool allows for the automatic updating of the Gaia OS and Check Point products installed on the Gaia OS?


