An office is experiencing constant connection attempts to the corporate Wi-Fi. Which of the following should be disabled to mitigate connection attempts?
SSID
A computer technician is investigating a computer that is not booting. The user reports that the computer was working prior to shutting it down last night. The technician notices a removable USB device is inserted, and the user explains the device is a prize the user received in the mail yesterday. Which of the following types of attacks does this describe?
Which of the following is the best reason for sandbox testing in change management?
To evaluate the change before deployment
Which of the following operating systems would most likely be used to run the inventory management system at a factory?
A Windows computer is experiencing slow performance when the user tries to open programs and files. The user recently installed a new software program from an external website.
Various websites are being redirected to an unauthorized site, and Task Manager shows the CPU usage is consistently at 100%. Which of the following should the technician do first?
Which of the following file extensions should a technician use for a PowerShell script?
A user is having phone issues after installing a new application that claims to optimize performance. The user downloaded the application directly from the vendor's website and is now experiencing high network utilization and is receiving repeated security warnings. Which of the following should the technician perform FIRST to mitigate the issue?
A technician is configuring a new Windows laptop Corporate policy requires that mobile devices make use of full disk encryption at all limes Which of the following encryption solutions should the technician choose?
A systems administrator is setting up a Windows computer for a new user Corporate policy requires a least privilege environment. The user will need to access advanced features and configuration settings for several applications. Which of the following BEST describes the account access level the user will need?
A technician successfully removed malicious software from an infected computer after running updates and scheduled scans to mitigate future risks. Which of the following should the technician do next?
Which of the following combinations meets the requirements for mobile device multifactor authentication?
A technician is moving a Windows workstation from the accounting department to the sales department and needs to update the IP and gateway settings. Which of the following Control Panel utilities should the technician use?
A technician wants to enable BitLocker on a Windows 10 laptop and is unable to find the BitLocker Drive Encryption menu item in Control Panel. Which of the following explains why the technician unable to find this menu item?
A Chief Executive Officer has learned that an exploit has been identified on the web server software, and a patch is not available yet. Which of the following attacks MOST likely occurred?
A user corrects a laptop that is running Windows 10 to a docking station with external monitors when working at a desk. The user would like to close the laptop when it is docked, but the user reports it goes to sleep when it is closed. Which of the following is the BEST solution to prevent the laptop from going to sleep when it is closed and on the docking station?
A technician needs to format a USB drive to transfer 20GB of data from a Linux computer to a Windows computer. Which of the following filesystems will the technician MOST likely use?
An organization is centralizing support functions and requires the ability to support a remote user's desktop. Which of the following technologies will allow a technician to see the issue along with the user?
A technician needs to document who had possession of evidence at every step of the process. Which of the following does this process describe?
Someone who is fraudulently claiming to be from a reputable bank calls a company employee. Which of the following describes this incident?
A technician needs to recommend the best backup method that will mitigate ransomware attacks. Only a few files are regularly modified, however, storage space is a concern. Which of the following backup methods would BEST address these concerns?
A company is Issuing smartphones to employees and needs to ensure data is secure if the devices are lost or stolen. Which of the following provides the BEST solution?
A technician is working with a company to determine the best way to transfer sensitive personal information between offices when conducting business. The company currently uses USB drives and is resistant to change. The company's compliance officer states that all media at rest must be encrypted. Which of the following would be the BEST way to secure the current workflow?
An administrator has submitted a change request for an upcoming server deployment. Which of the following must be completed before the change can be approved?
A user requested that the file permissions on a Linux device be changed to only allow access to a certain group of users. Which of the following commands should be used to complete the user's request?
A user's application is unresponsive. Which of the following Task Manager tabs will allow the user to address the situation?
Which of the following environments allows for the testing of critical systems without the risk of them being negatively impacted by changes?
A technician has been tasked with installing a workstation that will be used tor point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
Which of the following must be maintained throughout the forensic evidence life cycle when dealing with a piece of evidence?
The network was breached over the weekend System logs indicate that a single user's account was successfully breached after 500 attempts with a dictionary attack. Which of the following would BEST mitigate this threat?
A user reports that an air-gapped computer may have been infected with a virus after the user transferred files from a USB drive. The technician runs a computer scan with Windows Defender but does not find an infection. Which of the following actions should the technician take next? (Select two).
A technician is unable to join a Windows 10 laptop to a domain Which of the following is the MOST likely reason?
A user is unable to log in to the domain with a desktop PC, but a laptop PC is working properly on the same network. A technician logs in lo the desktop PC with a local account but is unable to browse to the secure intranet site to get troubleshooting tools. Which of the following is the MOST likely cause of the issue?
A user has a license for an application that is in use on a personal home laptop. The user approaches a systems administrator about using the same license on
multiple computers on the corporate network. Which of the following BEST describes what the systems administrator should tell the user?
A user reports that the hard drive activity light on a Windows 10 desktop computer has been steadily lit for more than an hour, and performance is severely degraded. Which of the following tabs in Task Manager would contain the information a technician would use to identify the cause of this issue?
A department has the following technical requirements for a new application:

The company plans to upgrade from a 32-bit Windows OS to a 64-bit OS. Which of the following will the company be able to fully take advantage of after the upgrade?
A user reports a computer is running slow. Which of the following tools will help a technician identity the issued
A user reports that a PC seems to be running more slowly than usual. A technician checks system resources, but disk, CPU, and memory usage seem to be fine. The technician sees that GPU temperature is extremely high. Which of the following types of malware is MOST likely to blame?
A technician suspects a rootkit has been installed and needs to be removed. Which of the following would BEST resolve the issue?
A customer calls desktop support and begins yelling at a technician. The customer claims to have submitted a support ticket two hours ago and complains that the issue still has not been resolved. Which of the following describes how the technician should respond?
Place the customer on hold until the customer calms down.
A systems administrator received a request to limit the amount of cellular data a user's Windows 10 tablet can utilize when traveling. Which of the following can the administrator do to best solve the user's issue?
A Linux technician needs a filesystem type that meets the following requirements:
. All changes are tracked.
. The possibility of file corruption is reduced.
· Data recovery is easy.
Which of the following filesystem types best meets these requirements?
ext3
A company-owned mobile device is displaying a high number of ads, receiving data-usage limit notifications, and experiencing slow response. After checking the device, a technician notices the device has been jailbroken. Which of the following should the technician do next?
Run an antivirus and enable encryption.
The calendar application on an employee's smartphone is experiencing frequent crashes, and the smartphone has become unresponsive. Which of the following should a technician do first to resolve the issue?
Which of the following languages is used for scripting the creation of Active Directory accounts?
Which of the following is command options is used to display hidden files and directories?
A user's company phone was stolen. Which of the following should a technician do next?
A technician cannot uninstall a system driver because the driver is currently in use. Which of the following tools should the technician use to help uninstall the driver?
A technician was assigned a help desk ticket and resolved the issue. Which of the following should the technician update to assist other technicians in resolving similar issues?
Antivirus software indicates that a workstation is infected with ransomware that cannot be quarantined. Which of the following should be performed first to prevent further damage to the host and other systems?
Turn off the machine.
A technician is modifying the default home page of all the workstations in a company. Which of the following will help to implement this change?
A user reports a hardware issue to the help desk. Which of the following should the help desk technician do first when responding to the user?
A technician installed a new application on a workstation. For the program to function properly, it needs to be listed in the Path Environment Variable. Which of the following Control Panel utilities should the technician use?
A laptop that was in the evidence room of a police station is missing. Which of the following is the best reason to refer to chain of custody documentation?
A technician is installing a program from an ISO file. Which of the following steps should the technician take?
A user lost a company tablet that was used for customer intake at a doctor's office. Which of the following actions would BEST protect against unauthorized access of the data?
A technician is finalizing a new workstation for a user. The user's PC will be connected to the internet but will not require the same private address each time. Which of the following protocols will the technician MOST likely utilize?
All the desktop icons on a user's newly issued PC are very large. The user reports that the PC was working fine until a recent software patch was deployed. Which of the following would BEST resolve the issue?
After a failed update, an application no longer launches and generates the following error message: Application needs to be repaired. Which of the following Windows 10 utilities should a technician use to address this concern?
A homeowner recently moved and requires a new router for the new ISP to function correctly. The internet service has been installed and has been confirmed as functional. Which of the following is the FIRST step the homeowner should take after installation of all relevant cabling and hardware?
A user notices a small USB drive is attached to the user's computer after a new vendor visited the office. The technician notices two files named grabber.exe and output.txt. Which of the following attacks is MOST likely occurring?
A SOHO client is having trouble navigating to a corporate website. Which of the following should a technician do to allow access?
A technician is troubleshooting boot times for a user. The technician attempts to use MSConfig to see which programs are starting with the OS but receives a message that it can no longer be used to view startup items. Which of the following programs can the technician use to view startup items?
A Windows user recently replaced a computer The user can access the public internet on the computer; however, an internal site at https7/companyintranet.com:8888 is no longer loading. Which of the following should a technician adjust to resolve the issue?
Which of the following filesystem formats would be the BEST choice to ensure read and write compatibility of USB flash drives across several generations of Microsoft operating systems?
A technician is editing the hosts file on a few PCs in order to block certain domains. Which of the following would the technician need to execute after editing the hosts file?
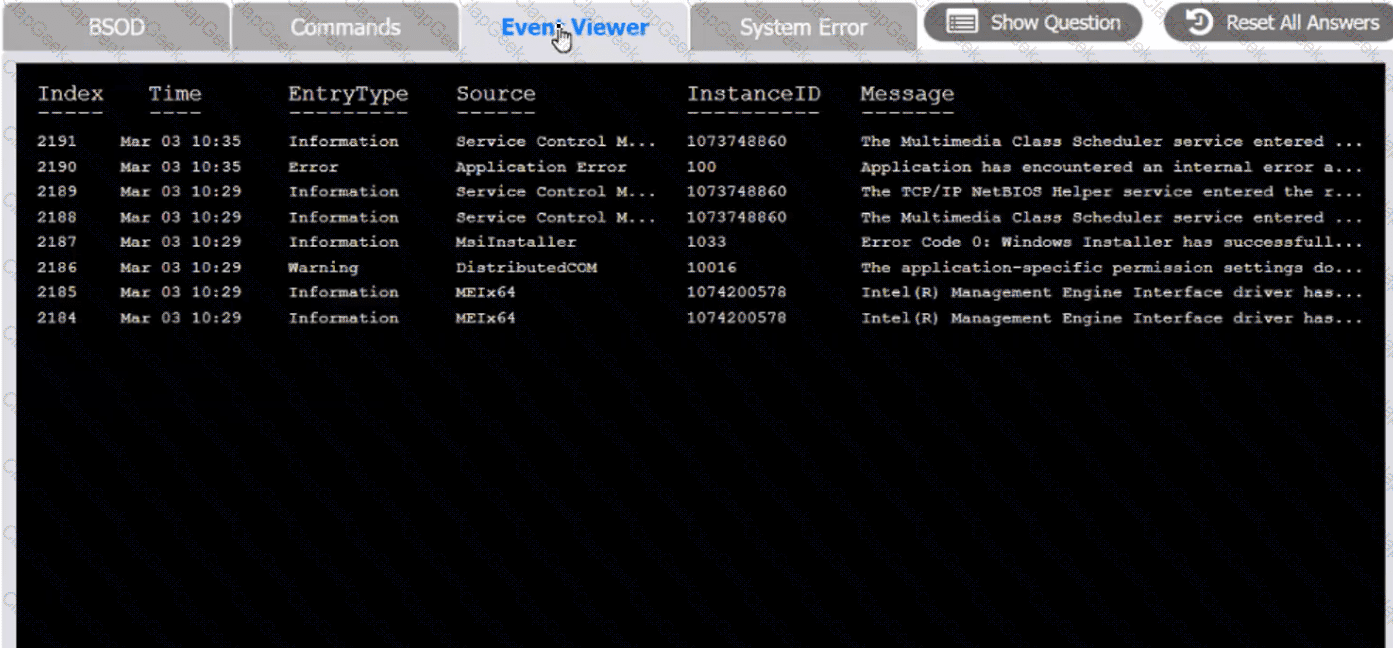
A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program.
However, other employees can successfully use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the:
Index number of the Event Viewer issue
First command to resolve the issue
Second command to resolve the issue
BSOD
Commands:
Event Viewer:
System Error:
A technician needs to remotely connect to a Linux desktop to assist a user with troubleshooting. The technician needs to make use of a tool natively designed for Linux. Which of the following tools will the technician MOST likely use?
A technician needs to access a Windows 10 desktop on the network in a SOHO using RDP. Although the connection is unsuccessful, the technician is able to ping the computer successfully. Which of the following is MOST likely preventing the connection?
A technician receives a call (rom a user who is having issues with an application. To best understand the issue, the technician simultaneously views the user's screen with the user. Which of the following would BEST accomplish this task?
Which of the following would MOST likely be used to change the security settings on a user's device in a domain environment?
Which of the following would MOST likely be deployed to enhance physical security for a building? (Select TWO).
Which of the following is used to explain issues that may occur during a change implementation?
Which of the following features allows a technician to configure policies in a Windows 10 Professional desktop?
A new employee was hired recently. Which of the following documents will the new employee need to sign before being granted login access to the network?
A technician is working on a way to register all employee badges and associated computer IDs. Which of the following options should the technician use in order to achieve this objective?
A user added a second monitor and wants to extend the display to it. In which of the following Windows settings will the user MOST likely be able to make this change?
Which of the following is MOST likely used to run .vbs files on Windows devices?
A technician downloads a validated security tool and notes the vendor hash of a58e87a2. When the download is complete, the technician again validates the hash, but the value returns as 2a876a7d3. Which of the following is the MOST likely cause of the issue?
A user's corporate phone was stolen, and the device contains company trade secrets. Which of the following technologies should be implemented to mitigate this risk? (Select TWO).
While staying at a hotel, a user attempts to connect to the hotel Wi-Fi but notices that multiple SSIDs have very similar names. Which of the following social-engineering attacks is being attempted?
An IT security team is implementing a new Group Policy that will return a computer to the login after three minutes. Which of the following BEST describes the change in policy?
Which of the following editions of Windows 10 requires reactivation every 180 days?
A manager called the help desk to ask for assistance with creating a more secure environment for the finance department- which resides in a non-domain environment. Which of the following would be the BEST method to protect against unauthorized use?
Which of the following default system tools can be used in macOS to allow the technician to view the screen simultaneously with the user?
Which of the following script types is used with the Python language by default?
A user tries to access commonly used web pages but is redirected to unexpected websites. Clearing the web browser cache does not resolve the issue. Which of the following should a technician investigate NEXT to resolve the issue?
A large company is selecting a new Windows operating system and needs to ensure it has built-in encryption and endpoint protection. Which of the following Windows versions will MOST likely be selected?
A technician is troubleshooting application crashes on a Windows workstation. Each time the workstation user tries to open a website in a browser, the following message is displayed:
crypt32.d11 is missing not found
Which of the following should the technician attempt FIRST?
A technician is installing a new copy of Windows on all computers in the enterprise Given the following requirements:
• The install phase must be scripted to run over the network • Each computer requires a new SSD as the system drive, • The existing HDD should remain as a backup drive.
Which of the following command-line tools should the technician use to install the drive and transfer the installation files from the network share? (Select three).
A user is trying to limit the amount of time their children spend on the internet. Which of the following Windows 10 settings should be enabled to accomplish this objective?
A user rotates a cell phone horizontally to read emails, but the display remains vertical, even though the settings indicate autorotate is on. VT1ich of the following will MOST likely resolve the issue?
A company was recently attacked by ransomware. The IT department has remediated the threat and determined that the attack method used was email. Which of the following is the most effective way to prevent this issue from reoccurring?
A user reports being unable to access a sports team's website on an office computer. The administrator tells the user this blocked access is intentional and based on company guidelines. Which of the following is the administrator referring to?
A technician receives a high-priority ticket about sensitive information collected from an end user’s workstation. Which of the following steps should a technician take to preserve the chain of custody for a forensic investigation?
Which of the following languages is used for scripting the creation of Active Directory accounts?
A user is experiencing the following issues with Bluetooth on a smartphone:
•The user cannot hear any sound from a speaker paired with the smartphone.
•The user is having issues synchronizing data from their smart watch, which is also connected via Bluetooth.
A technician checked the Bluetooth settings, confirmed it is successfully paired with a speaker, and adjusted the volume levels, but still could not hear anything. Which of the following steps should the technician take next to troubleshoot the Bluetooth issues?
Which of the following operating systems was the app file type designed to run under as an application file bundle?
A customer who uses a Linux OS called the help desk to request assistance in locating a missing file. The customer does not know the exact name of the file but can provide a partial file name. Which of the following tools should the technician use? (Select two).
A user's computer is running slower than usual and takes a long time to start up. Which of the following tools should the technician use first to investigate the issue?
A customer, whose smartphone's screen was recently repaired, reports that the device has no internet access through Wi-Fi. The device shows that it is connected to Wi-Fi, has an address of 192.168.1.42. and has no subnet mask. Which of the following should the technician check next?
A technician is troubleshooting a smartphone that is unable to download and install the latest OS update. The technician notices the device operates more slowly than expected, even after rebooting and closing all applications. Which of the following should the technician check next?
A user is unable to start a computer following a failed Windows 10 update. When trying to start the computer, the user sees a blue screen of death. Which of the following steps should a technician take to diagnose the issue?
A technician is doing a bare-metal installation of the Windows 10 operating system. Which of the following prerequisites must be in place before the technician can start the installation process?
A company installed WAPs and deployed new laptops and docking stations to all employees. The docking stations are connected via LAN cables. Users are now reporting degraded network service. The IT department has determined that the WAP mesh network is experiencing a higher than anticipated amount of traffic. Which of the following would be the most efficient way to ensure the wireless network can support the expected number of wireless users?
An administrator needs to back up the following components of a single workstation:
•The installation of the operating system
•Applications
•User profiles
•System settings
Which of the following backup methods can the administrator use to ensure the workstation is properly backed up?
A technician needs to update the software on several hundred Mac laptops. Which of the following is the best method to complete the task?
A technician downloaded an OS installation file but is unable to run it. When the technician tries to open the file, a message indicates no software is installed to run this file. Which of the following should the technician do next to attempt to access the OS file?
A company wants to take advantage of modern technology and transition away from face-to-face meetings. Which of the following types of software would benefit the company the most? (Select two).
A technician wants to harden Windows workstations after a recent security audit indicated the company is vulnerable to brute-force attacks. Which of the following features should the technician implement to mitigate such attacks?
An employee using an Apple MacBook is receiving frequent, random pop-up requests from other Apple devices wanting to share photos and videos and asking whether the user would like to accept the request Which of the following configurations should the technician advise the user to change first"?
A technician needs to troubleshoot a user's computer while the user is connected to the system. The technician must also connect to the user's system using remote access tools built in to Windows Which of the following is the best option to troubleshoot the user's computer?
A user accidentally installed the incorrect word processing application on an iMac. Which of the following would allow the user to uninstall the incorrect application?
A technician is troubleshooting a Windows system that is having issues with the OS loading at startup. Which of the following should the technician do to diagnose the issue?
A technician wants to improve password security after several users admitted to using very simple passwords. Which of the following is the best way to resolve this issue?
A user submits a request to have a graphics application installed on a desktop When the technician attempts to install the application, the installation fails and the error message "Not compatible with OS' is displayed. Which of the following is the most likely reason for this error message?
Which of the following features can a technician use to ensure users are following password length requirements?
A technician is upgrading the Microsoft Windows 10 OS. Which of the following are required for the technician to safely upgrade the OS? (Select two).
When a user attempts to open an email using a company-issued smartphone, the user receives a message stating the email is encrypted and cannot be opened. The user forwards the email to a personal account and receives the same message. The user then contacts the IT department for assistance. The technician instructs the user to contact the sender to exchange information in order to decode the message. Which of the following will the user receive from the sender?
A technician is setting up a printer on a Linux workstation. Which of the following commands should the technician use to set the default printer?
An organization wants to deploy a customizable operating system. Which of the following should the organization choose?
Which of the following features can be used to ensure a user can access multiple versions of files?
A technician wants to securely dispose of storage drives. Which of the following is the best way to eliminate data on SSDs?
A technician is troubleshooting a user’s PC that is running slowly and displaying frequent pop-ups. The technician thinks malware may be causing the issues, but before the issues began the user installed anti-malware software in response to a pop-up window Which of the following is the most likely cause of these issues'?
A user clicked a link in an email, and now the cursor is moving around on its own. A technician notices that File Explorer is open and data is being copied from the local drive to an unknown cloud storage location. Which of the following should the technician do first?
A technician is troubleshooting a PC that is unable to perform DNS lookups. Utilizing the following firewall output:
Protocol/PortActionDirection
1 AllowOut
445 BlockOut
53 BlockOut
123 BlockOut
80 BlockOut
Which of the following ports should be opened to allow for DNS recursion?
The findings from a security audit indicate the risk of data loss from lost or stolen laptops is high. The company wants to reduce this risk with minimal impact to users who want to use their laptops when not on the network. Which of the following would BEST reduce this risk for Windows laptop users?
After a company installed a new SOHO router customers were unable to access the company-hosted public website. Which of the following will MOST likely allow customers to access the website?
A technician is attempting to mitigate micro power outages, which occur frequently within the area of operation. The outages are usually short, with the longest occurrence lasting five minutes. Which of the following should the technician use to mitigate this issue?
A network administrator is deploying a client certificate to be used for Wi-Fi access for all devices in an organization. The certificate will be used in conjunction with the user's existing username and password. Which of the following BEST describes the security benefits realized after this deployment?
A technician just completed a Windows 10 installation on a PC that has a total of 16GB of RAM. The technician notices the Windows OS has only 4GB of RAM available for use. Which of the following explains why the OS can only access 46B of RAM?
A technician is working to resolve a Wi-Fi network issue at a doctor's office that is located next to an apartment complex. The technician discovers that employees and patients are not the only people on the network. Which of the following should the technician do to BEST minimize this issue?
A user calls the help desk and reports a workstation is infected with malicious software. Which of the following tools should the help desk technician use to remove the malicious software? (Select TWO).
An administrator has received approval for a change request for an upcoming server deployment. Which of the following steps should be completed NEXT?
A help desk team lead contacts a systems administrator because the technicians are unable to log in to a Linux server that is used to access tools. When the administrator tries to use remote desktop to log in to the server, the administrator sees the GUI is crashing. Which of the following methods can the administrator use to troubleshoot the server effectively?
A company has just refreshed several desktop PCs. The hard drives contain PII. Which of the following is the BEST method to dispose of the drives?
A call center handles inquiries into billing issues for multiple medical facilities. A security analyst notices that call center agents often walk away from their workstations, leaving patient data visible for anyone to see. Which of the following should a network administrator do to BEST prevent data theft within the call center?
Antivirus software indicates that a workstation is infected with ransomware that cannot be quarantined. Which of the following should be performed FIRST to prevent further damage to the host and other systems?
A technician receives a call from a user who is on vacation. The user provides the necessary credentials and asks the technician to log in to the
users account and read a critical email that the user has been expecting. The technician refuses because this is a violation of the:
A manager reports that staff members often forget the passwords to their mobile devices and applications. Which of the following should the systems administrator do to reduce the number of help desk tickets submitted?
A new service desk is having a difficult time managing the volume of requests. Which of the following is the BEST solution for the department?
A small business owner wants to install newly purchased software on all networked PCs. The network is not configured as a domain, and the owner wants to use the easiest method possible. Which of the following is the MOST deficient way lor the owner to install the application?
The web browsing speed on a customer's mobile phone slows down every few weeks and then returns to normal after three or four days. Restarting the device does not usually restore performance. Which of the following should a technician check FIRST to troubleshoot this issue?
A technician is troubleshooting a computer with a suspected short in the power supply. Which of the following is the FIRST step the technician should take?
A desktop support technician is tasked with migrating several PCs from Windows 7 Pro to Windows 10 Pro, The technician must ensure files and user preferences are retained, must perform the operation locally, and should migrate one station at a time. Which of the following methods would be MOST efficient?
A bank would like to enhance building security in order to prevent vehicles from driving into the building while also maintaining easy access for customers. Which of the following BEST addresses this need?
A technician is reimaging a desktop PC. The technician connects the PC to the network and powers it on. The technician attempts to boot the computer via the NIC to image the computer, but this method does not work. Which of the following is the MOST likely reason the computer is unable to boot into the imaging system via the network?
A technician is troubleshooting an issue that requires a user profile to be rebuilt. The technician is unable to locate Local Users and Groups in the Mtv1C console. Which of the following is the NEXT step the technician should take to resolve the issue?
Security software was accidentally uninstalled from all servers in the environment. After requesting the same version of the software be reinstalled, the security analyst learns that a change request will need to be filled out. Which of the following is the BEST reason to follow the change management process in this scenario?
A junior administrator is responsible for deploying software to a large group of computers in an organization. The administrator finds a script on a popular coding website to automate this distribution but does not understand the scripting language. Which of the following BEST describes the risks in running this script?
A macOS user needs to create another virtual desktop space. Which of the following applications will allow the user to accomplish this task?
A technician is setting up a new laptop. The company's security policy states that users cannot install virtual machines. Which of the following should the technician implement to prevent users from enabling virtual technology on their laptops?
A customer recently experienced a power outage at a SOHO. The customer does not think the components are connected properly. A print job continued running for several minutes after the power failed, but the customer was not able to interact with the computer. Once the UPS stopped beeping, all functioning devices also turned off. In case of a future power failure, the customer wants to have the most time available to save cloud documents and shut down the computer without losing any data.
A user received the following error upon visiting a banking website:
The security presented by website was issued a different website' s address .
A technician should instruct the user to:
A user receives a notification indicating the data plan on the user's corporate phone has reached its limit. The user has also noted the performance of the phone is abnormally slow. A technician discovers a third-party GPS application was installed on the phone. Which of the following is the MOST likely cause?
A technician is setting up a new laptop for an employee who travels. Which of the following is the BEST security practice for this scenario?
While browsing a website, a staff member received a message that the website could not be trusted. Shortly afterward, several other colleagues reported the same issue across numerous other websites. Remote users who were not connected to corporate resources did not have any issues. Which of the following is MOST likely the cause of this issue?
A macOS user reports seeing a spinning round cursor on a program that appears to be frozen. Which of the following methods does the technician use to force the program to close in macOS?
Which of the following Is used to identify potential issues with a proposed change poor lo implementation?
During a network outage, a technician discovers a new network switch that was not listed in the support documentation. The switch was installed during a recent change window when a new office was added to the environment. Which of the following would most likely prevent this type of mismatch after next month's change window?
Users access files in the department share. When a user creates a new subfolder, only that user can access the folder and Its files. Which of the following will MOST likely allow all users to access the new folders?
A technician needs to establish a remote access session with a user who has a Windows workstation. The session must allow for simultaneous viewing of the workstation by both the user and technician. Which of the following remote access technologies should be used?
A large university wants to equip all classrooms with high-definition IP videoconferencing equipment. Which of the following would most likely be impacted in this situation?
The courts determined that a cybercrimes case could no longer be prosecuted due to the agency's handling of evidence. Which of the following was MOST likely violated during the investigation?
A company recently outsourced its night-shift cleaning service. A technician is concerned about having unsupervised contractors in the building. Which of the following security measures can be used to prevent the computers from being accessed? (Select two).
An administrator responded to an incident where an employee copied financial data to a portable hard drive and then left the company with the data. The administrator documented the movement of the evidence. Which of the following concepts did the administrator demonstrate?
A company is experiencing a ODDS attack. Several internal workstations are the source of the traffic Which of the following types of infections are the workstations most likely experiencing? (Select two)
A user called the help desk lo report an Issue with the internet connection speed on a laptop. The technician thinks that background services may be using extra bandwidth. Which of the following tools should the technician use to investigate connections on the laptop?
A remote user is having issues accessing an online share. Which of the following tools would MOST likely be used to troubleshoot the Issue?
Which of the following common security vulnerabilities can be mitigated by using input validation?
A technician discovers user input has been captured by a malicious actor. Which of the following malware types is MOST likely being used?
A user opened a ticket regarding a corporate-managed mobile device. The assigned technician notices the OS Is several versions out of date. The user Is unaware the OS version is not current because auto-update is turned on. Which of the following is MOST likely the cause of the Issue?
A systems administrator is monitoring an unusual amount of network traffic from a kiosk machine and needs to Investigate to determine the source of the traffic. Which of the following tools can the administrator use to view which processes on the kiosk machine are connecting to the internet?
A user installed a new computer game. Upon starting the game, the user notices the frame rates are low. Which of the following should the user upgrade to resolve the issue?
A customer is accessing a public kiosk in a company's lobby. Which of the following should be enforced to mitigate the risk of customer data being accidentally saved to the kiosk?
A technician removed a virus from a user's device. The user returned the device a week later with the same virus on it. Which of the following should the technician do to prevent future infections?
A user is unable to access a web-based application. A technician verifies the computer cannot access any web pages at all. The computer obtains an IP address from the DHCP server. Then, the technician verifies the user can ping localhost. the gateway, and known IP addresses on the interne! and receive a response. Which of the following Is the MOST likely reason tor the Issue?
Which of the following macOS features can help a user close an application that has stopped responding?
A corporation purchased new computers for a school. The computers are the same make and model and need to have the standard image loaded. Which of the following orchestration tools should a desktop administrator use tor wide-scale deployment?
A desktop technician has received reports that a user's PC is slow to load programs and saved files. The technician investigates and discovers an older HDD with adequate free space. Which of the following should the technician use to alleviate the issue first?
Which of the following protects a mobile device against unwanted access when it is left unattended?
A help desk technician determines a motherboard has failed. Which of the following is the most logical next step in the remediation process?
An administrator is designing and implementing a server backup system that minimizes the capacity of storage used. Which of the following is the BEST backup approach to use in conjunction with synthetic full backups?
A company's assets are scanned annually. Which of the following will most likely help the company gain a holistic view of asset cost?
A Windows user wants a filesystem that protects confidential data from attackers who have physical access to the system. Which of the following should the user choose?
A user is unable to log in to a workstation. The user reports an error message about the date being incorrect. A technician reviews the date and verifies it is correct, but the system clock is an hour behind. The technician also determines this workstation is the only one affected. Which of the following is the most likely issue?
A user reports that a new, personally owned tablet will not connect to the corporate Wi-Fi network. The user is able to connect to the Wi-Fi network with other devices, and the tablet is running the latest software. Which of the following is the most likely cause of the issue?
A technician is performing hardware maintenance on a desktop PC. Which of the following is the most important safety precaution the technician should take?
A client recently upgraded their Windows 10 machine to Windows 11. The client reports the following message displays when turning the computer on: "Error loading operating system." Which of the following should a technician do first to troubleshoot this issue?
Employees at comptia.org are reporting getting an usual amount of emails from a coworker. A technician discovers the emails were sent from the following address:
john@cOmptia.org
Which of the following social engineering attacks is this an example of?
A technician needs to open a port on a firewall in order to connect to a Linux server via a terminal interface. Which of the following ports should the technician open?
Which of the following provides disk encryption on computers running a Windows OS?
Which of the following is the most secure method of preventing someone from accessing a cell phone?
A user's smartphone screen is not rotating. The technician confirms the rotation lock is deactivated. Which of the following steps should the technician perform next?
After a user upgraded the Windows operating system to the latest feature release, the user notices that one of the legacy applications that was running correctly before the upgrade does not open some windows and is only partially functional. Which of the following actions should the user take to troubleshoot the issue?
A hard drive that previously contained PII needs to be repurposed for a public access workstation. Which of the following data destruction methods should a technician use to ensure data is completely removed from the hard drive?
A user's workstation was infected with a newly discovered virus that the AV system detected. After a full virus scan and a workstation reboot, the virus is still present in the OS. Which of the following actions should the user take to remove the virus?
A technician, who is completing hardware upgrades at a company, is approached by a user who submitted a computer upgrade request. After checking the list of offices to upgrade, the technician finds that the user's office is not listed for an upgrade. Which of the following actions should the technician take next?
Which of the following script file types is typically used to install Windows packages?
A technician wants to update the local security policies on a Windows machine but is unable to launch the expected snap-in. Which of the following is the most likely reason?
Which of the following commands should a technician use to change user permissions?
h company uses shared drives as part of a workforce collaboration process. To ensure the correct access permissions, inheritance at the top-level folder is assigned to each department. A manager's team is working on confidential material and wants to ensure only the immediate team can view a specific folder and its subsequent files and subfolders. Which of the following actions should the technician most likely take?
Which of the following commands should a technician use to change user permissions?
When a user is browsing a website on a smartphone, a pop-up appears. The pop-up states that the system has been breached and directs the user to an application to resolve the breach. Which of the following should the user do?
A technician needs to create a security and compliance policy for backup requirements. The backups are required to:
Have the least possible impact on users.
Minimize additional expenses.Which of the following are the best options for the technician to include? (Select two).
A technician is installing an operating system on a new computer. Which of the following is the first step of the process?
A user is unable to see transaction details on a website, and nothing happens when the user clicks the details button. Which of the following should the user do to fix this issue?
Which of the following can be used for multifactor authentication when logging in to a computer system? (Select two).
A technician assigns the equivalent of root-level permissions to a user to perform a task. Which of the following user roles within the Windows OS should the technician choose?
A technician needs to override DNS and map IP addresses and URLs to different locations. Which of the following should the technician do?
A technician thinks that a computer on the network has been infected with malware. The technician attempts several times to use a malware removal tool, but the issue persists. Which of the following should the technician do next?
A systems administrator needs to access a hypervisor that went offline. After doing a port scan, the administrator notices that company policy is blocking the RDP default port. Which of the following ports should the administrator use to access the machine?
Which of the following types of malware is designed to enable administrative access to a computer?
An Internet cafe has several computers available for public use. Recently, users have reported the computers are much slower than they were the previous week. A technician finds the CPU is at 100% utilization, and antivirus scans report no current infection. Which of the following is MOST likely causing the issue?
Following the latest Windows update PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
Which of the following is the MOST cost-effective version of Windows 10 that allows remote access through Remote Desktop?
A company wants to remove information from past users' hard drives in order to reuse the hard drives Witch of the following is the MOST secure method
A user has requested help setting up the fingerprint reader on a Windows 10 laptop. The laptop is equipped with a fingerprint reader and is joined to a domain Group Policy enables Windows Hello on all computers in the environment. Which of the following options describes how to set up Windows Hello Fingerprint for the user?
A technician installed a known-good, compatible motherboard on a new laptop. However, the motherboard is not working on the laptop. Which of the following should the technician MOST likely have done to prevent damage?
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
Upon downloading a new ISO, an administrator is presented with the following string:
59d15a16ce90cBcc97fa7c211b767aB
Which of the following BEST describes the purpose of this string?
A workstation is displaying a message indicating that a user must exchange cryptocurrency for a decryption key. Which of the following is the best way for a technician to return the device to service safely?
A network administrator is deploying a client certificate lo be used for Wi-Fi access for all devices m an organization The certificate will be used in conjunction with the user's existing username and password Which of the following BEST describes the security benefits realized after this deployment?
A technician is setting up a desktop computer in a small office. The user will need to access files on a drive shared from another desktop on the network. Which of the following configurations should the technician employ to achieve this goal?
Which of the following is the MOST important environmental concern inside a data center?
A technician needs to interconnect two offices to the main branch while complying with good practices and security standards. Which of the following should the technician implement?
A technician sees a file that is requesting payment to a cryptocurrency address. Which of the following should the technician do first?
A user is unable to access files on a work PC after opening a text document. The text document was labeled "URGENT PLEASE READ.txt - In active folder, .txt file titled urgent please read". Which of the following should a support technician do FIRST?
Which of the following macOS utilities uses AES-128 to encrypt the startup disk?
Which of the following physical security controls can prevent laptops from being stolen?
Which of the following would cause a corporate-owned iOS device to have an Activation Lock issue?
A user wants to back up a Windows 10 device. Which of the following should the user select?
A Windows administrator is creating user profiles that will include home directories and network printers for several new users. Which of the following is the most efficient way for the technician to complete this task?
A technician is unable to access the internet or named network resources. The technician receives a valid IP address from the DHCP server and can ping the default gateway. Which of the following should the technician check next to resolve the issue?
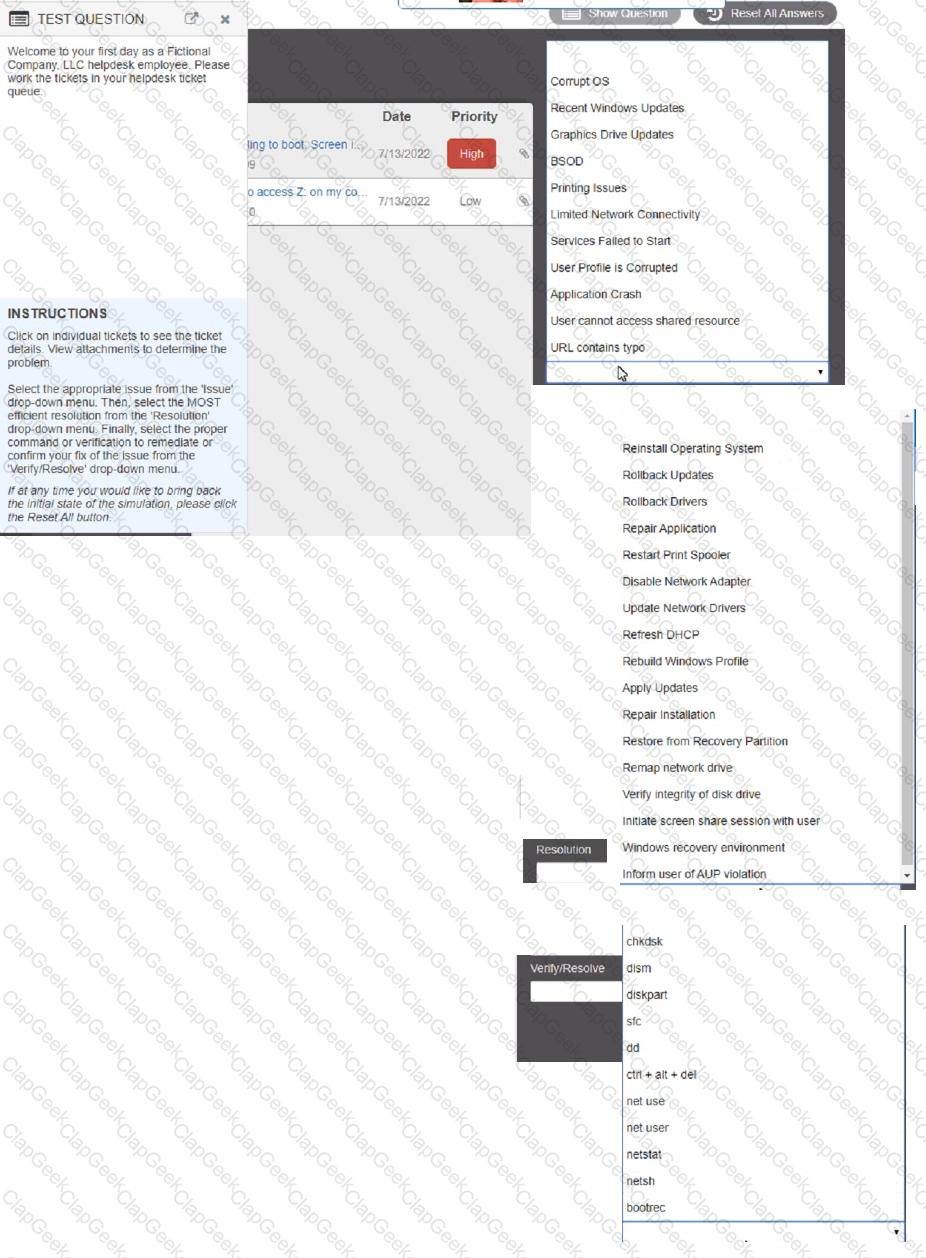
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
A technician recently installed a new router for a small business. Afterwards, the technician completed an external port scan and generated the following information:
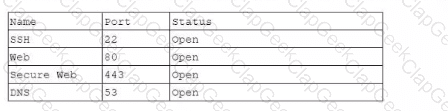
Which of the following should the technician perform next in order to follow best practices?
An organization has a goal to perform daily backups of a particular workstation and save them locally to the NAS. The organization needs to ensure these backup jobs are successful. Which of the following should the IT department do?
Which of the following security threats requires a phone call to launch the attack?
Which of the following are common commands that are used when installing applications in Linux? (Select two).
A user with a disability needs to be able to press the Ctrl+Alt+Del keyboard sequence one key at a time. Which of the following turns on this Ease of Access feature?
Two users share a computer and logins. User A visits a personal email and banking site and wants to ensure that User B is not able to view the browser history or passwords associated with those sites. Which of the following is a way for User A to protect this Information?
A technician wants to mitigate unauthorized data access if a computer is lost or stolen. Which of the following features should the technician enable?


