Your network contains an Active Directory Domain Services (AD DS) domain.
You need to implement a solution that meets the following requirements:
Ensures that the members of the Domain Admins group are allowed to sign in only to domain controllers
Ensures that the lifetime of Kerberos Ticket Granting Ticket (TGT) for the members of the Domain Admins group is limited to one hour
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection.
Does this meet the goal?
You have an on-premises server named Server1 and Microsoft Sentinel instance.
You plan to collect windows Defender Firewall events from Sever1 and analyze the event data by using Microsoft Sentinel.
What should you install on Server1, and which information should you provide during the instance? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
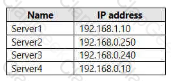
Your on-premises network contains two subnets. The subnets contain servers that run Windows Server as shown in the following table.
Server4 has the following IP configurations:
Ethernet adapter Ethernet:
Connection-specific DNS Suffix.:
IPv4 Address . . . . . . . . . . . : 192.168.0.10
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.0.1
From Server4, you can ping Server1 and Server2 successfully. When you ping Server3, you get a Request timed out response.
From Server2, you can ping Server1 and Server3 successfully.
The misconfiguration of which component on Server3 can cause the Request timed out response?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
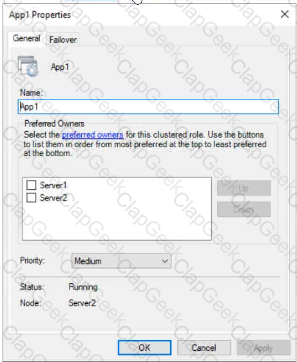
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
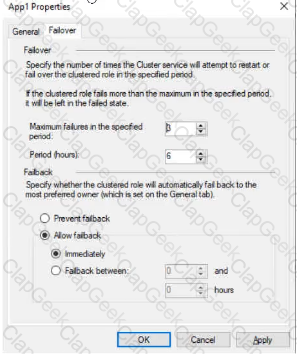
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the Failover settings, you select Prevent failback.
Does this meet the goal?
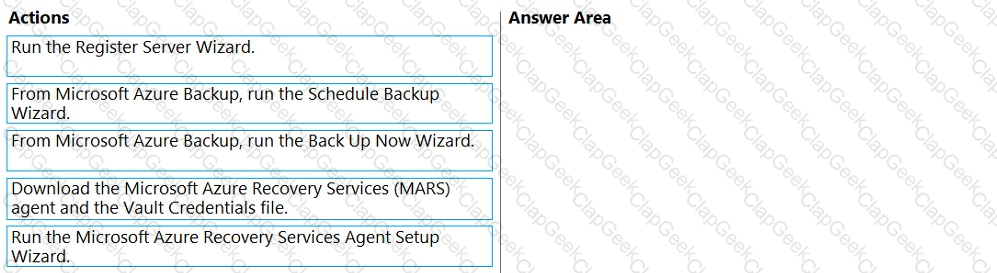
You have a server that runs Windows Server.
You plan to back up the server to an Azure Recovery Services vault once per week starting on the next Saturday.
You need to schedule the weekly backup and perform the initial backup as soon as possible.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer are and arrange them in the correct order.
You have a Site-to-Site VPN between an on-premises network and an Azure VPN gateway. BGP is disabled for the Site-to-Site VPN.
You have an Azure virtual network named Vnet1 that contains a subnet named Subnet1. Subnet1 contains a virtual machine named Server1.
You can connect to Server1 from the on-premises network.
You extend the address space of Vnet1. You add a subnet named Subnet2 to Vnet1. Subnet2 uses the extended address space. You deploy an Azure virtual machine named Server2 to Subnet2.
You cannot connect to Server2 from the on-premises network. Server1 can connect to Server2.
You need to ensure that you can connect to Subnet2 from the on-premises network.
What should you do?
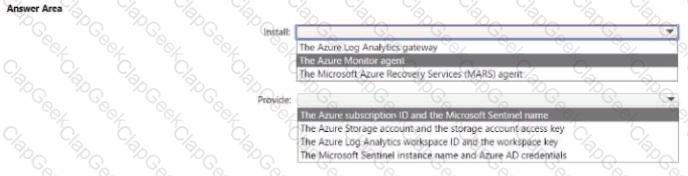
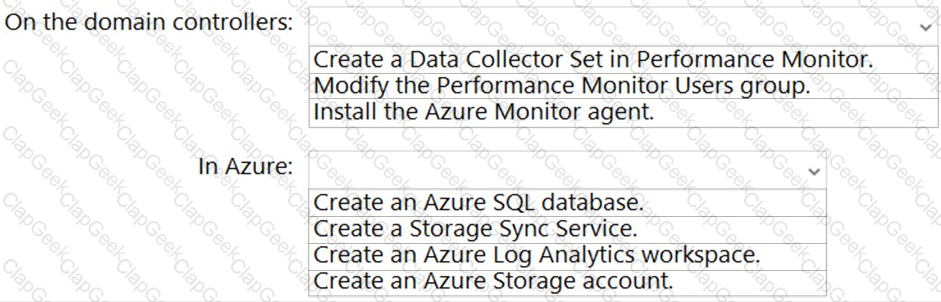
You need to implement alerts for the domain controllers. The solution must meet the technical requirements.
What should you do on the domain controllers, and what should you create on Azure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to back up Server 4 to meet the technical requirements.
What should you do first?
You need to meet the technical requirements for Cluster3.
What should you include in the solution?
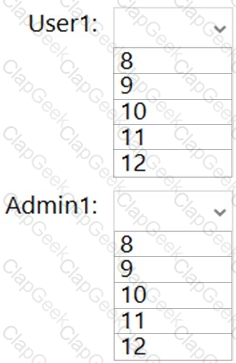
What is the effective minimum password length for User1 and Admin1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
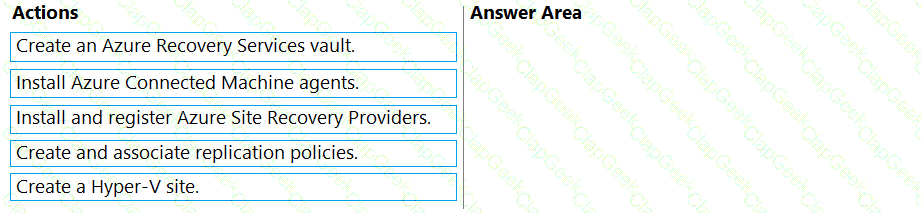
You need to meet the technical requirements for Cluster2.
Which four actions should you perform in sequence before you can enable replication? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You are planning the data share migration to support the on-premises migration plan.
What should you use to perform the migration?
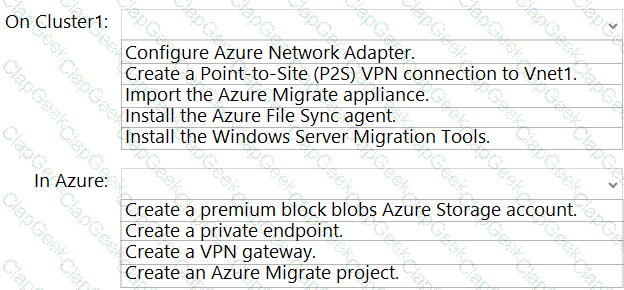
You are planning the migration of APP3 and APP4 to support the Azure migration plan.
What should you do on Cluster1 and in Azure before you perform the migration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
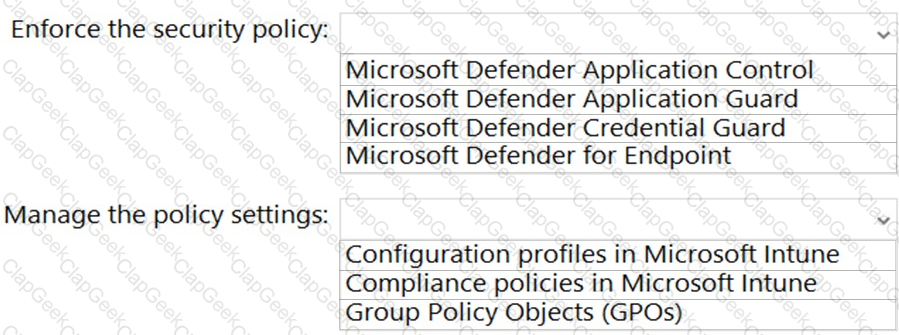
You need to implement a security policy solution to authorize the applications. The solution must meet the security requirements.
Which service should you use to enforce the security policy, and what should you use to manage the policy settings? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You are planning the migration of Archive1 to support the on-premises migration plan.
What is the minimum number of IP addresses required for the node and cluster roles on Cluster3?
You are remediating the firewall security risks to meet the security requirements.
What should you configure to reduce the risks?
You are planning the implementation of Cluster2 to support the on-premises migration plan.
You need to ensure that the disks on Cluster2 meet the security requirements.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
You are planning the DHCP1 migration to support the DHCP migration plan.
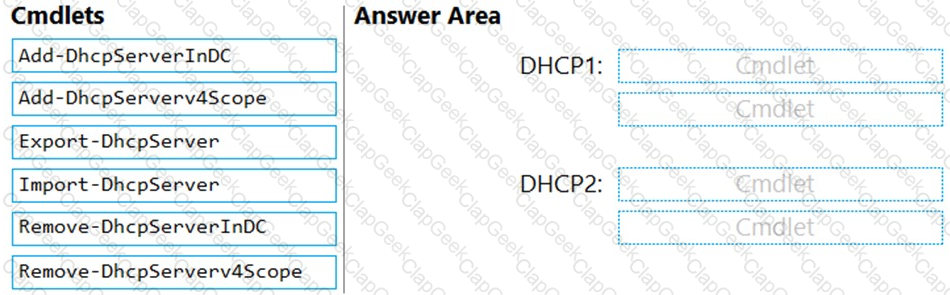
Which two PowerShell cmdlets should you run on DHCP1, and which two PowerShell cmdlets should you run on DHCP2? To answer, drag the appropriate cmdlets to the correct servers. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
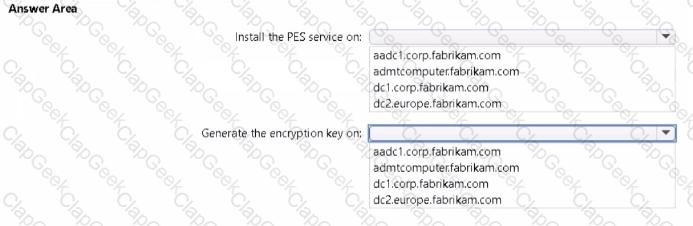
You are planning the europe.fabrikam.com migration to support the on-premises migration plan-Where should you install the Password Export Server (PES) service, where should you generate the encryption key? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You are planning the deployment of Microsoft Sentinel.
Which type of Microsoft Sentinel data connector should you use to meet the security requirements?
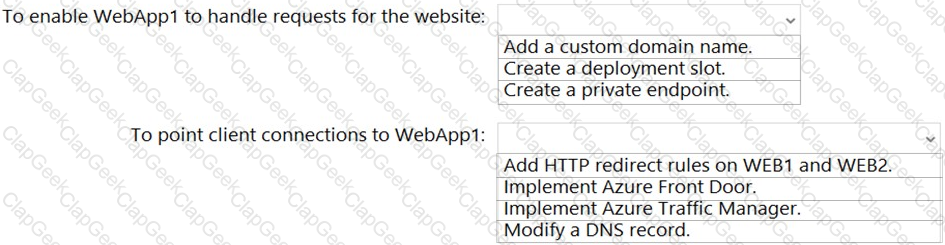
You are planning the www.fabrikam.com website migration to support the Azure migration plan.
How should you configure WebApp1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises server named Server1 that runs Windows Server.
You have a Microsoft Sentinel instance.
You add the Windows Firewall data connector in Microsoft Sentinel.
You need to ensure that Microsoft Sentinel can collect Windows Firewall logs from Server1.
Solution; You enable event subscription on Server1.
Does this meet the goal?
You have an Azure subscription. The subscription contains a virtual machine named VM1 that runs Windows Server and uses Azure Disk Encryption.
You need to identify which Azure key vault stores the encryption keys for VM1. The solution must minimize administrative effort.
Which PowerShell cmdlet should you run?
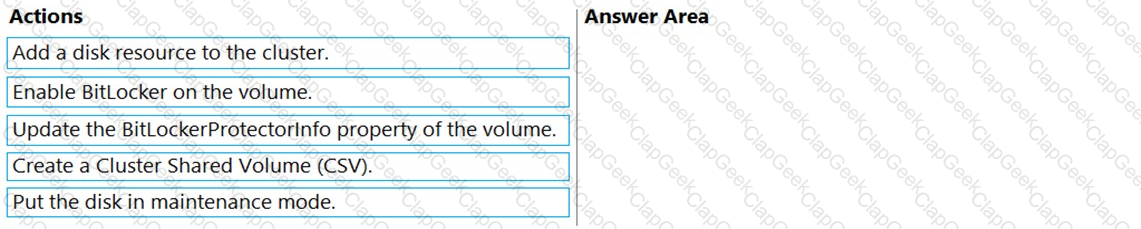
You have a Windows Server 2022 failover cluster named Cluster1 that contains the Cluster Shared Volumes (CSV) shown in the following table.
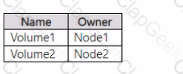
All the nodes in Cluster1 have BitLocker Drive Encryption (BitLocker) installed.
You need to use PowerShell to enable BitLocker on Volume1.
In which order should you run the commands? To answer, drag the appropriate commands to the correct order. You may need to drag the split bar between panes or scroll to view content.
NOTE Each correct selection is worth one point.
You have 10 servers that run Windows Server in a workgroup.
You need to configure the servers to encrypt all the network traffic between the servers. The solution must be as secure as possible.
Which authentication method should you configure in a connection security rule?
You have a failover cluster named Cluster1 that contains three nodes.
You plan to add two file server cluster roles named File1 and File2 to Cluster1. File1 will use the File Server for general use role. File2 will use the Scale-Out File Server for application data role.
What is the maximum number of nodes for File1 and File2 that can concurrently serve client connections? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have the servers shown in the following table.
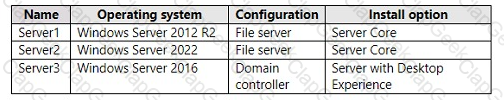
You plan to migrate file shares from Server1 to Server2.