After analyzing an active offense where many source systems were observed connecting to a specific destination via local-to-local LDAP traffic, an ^lyst discovered that the targeted system is a legitimate LDAP server within the organization.
x avoid confusion in future analyses, how can this type of traffic to the target system be flagged as expected and be excluded from further offense ation?
Which QRadar component provides the user interface that delivers real-time flow views?
Which IBM X-Force Exchange feature could be used to query QRadar to see if any of the lOCs were detected for COVID-19 activities?
Which parameter should be used if a security analyst needs to filter events based on the time when they occurred on the endpoints?
What is the name of the data collection set used in QRadar that can be populated with lOCs or other external data?
An analyst wants to implement an AQL search in QRadar. Which two (2) tabs can be used to accomplish this implementation?
Which two (2) options are at the top level when an analyst right-clicks on the Source IP or Destination IP that is associated with an offense at the Offense Summary?
Many offenses are generated and an analyst confirms that they match some kind of vulnerability scanning.
Which building block group needs to be updated to include the source IP of the vulnerability assessment (VA) scanner to reduce the number of offenses that are being generated?
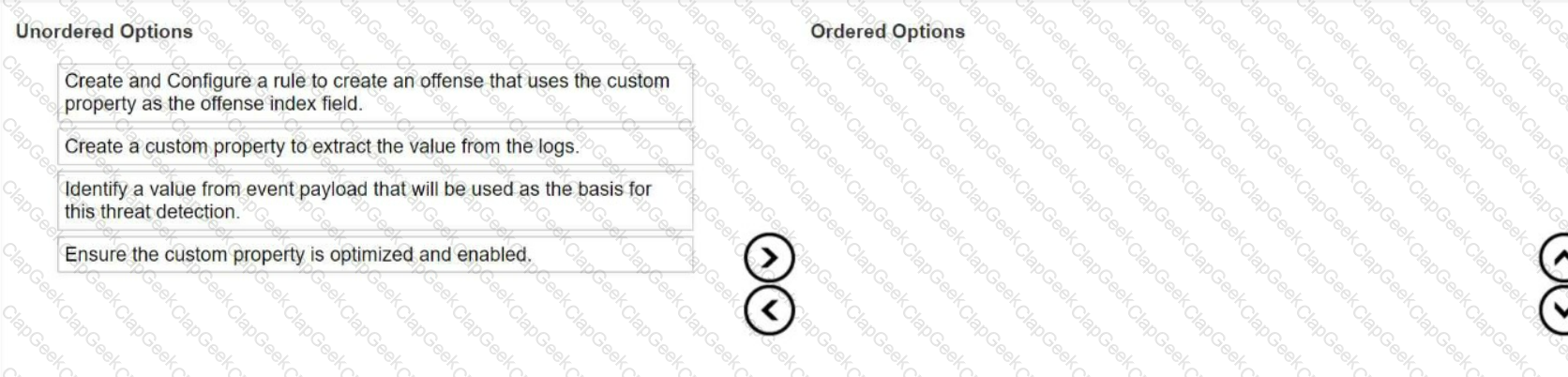
A new log source was configured to send events to QRadar to help detect a malware outbreak. A security analyst has to create an offense based on properties from this payload but not all the information is parsed correctly.
What is the sequence of steps to ensure that the correct information is pulled from the payload to use in a rule?
On the Log Activity tab in QRadar. what are the options available when right-clicking an IP address of an event to access more event filter information?
What type of custom property should be used when an analyst wants to combine extraction-based URLs, virus names, and secondary user names into a single property?
What does the Next Run Time column display when a report is queued for generation in QRadar?
For a rule containing the test "and when the source is located in this geographic location" to work properly, what must a QRadar analyst configure?
Create a list that stores Username as the first key. Source IP as the second key with an assigned cidr data type, and Source Port as the value.
The example above refers to what kind of reference data collections?
A QRadar analyst develops an advanced search on the Log Activity tab and presses the shortcut "Ctrl + Space" in the search field. What information is displayed?
A QRadar analyst wants to limit the time period for which an AOL query is evaluated. Which functions and clauses could be used for this?
What is the benefit of using default indexed properties for searching in QRadar?
Which types of information does QRadar analyze to create an offense from the rule?
What are two (2) Y-axis types that are available in the scatter chart type in the Pulse app?
Which two (2) values are valid for the Offense Type field when a search is performed in the My Offenses or All Offenses tabs?
What does an analyst need to do before configuring the QRadar Use Case Manager app?
On the Dashboard tab in QRadar. dashboards update real-time data at what interval?
What is the default number of notifications that the System Notification dashboard can display?
What type of building blocks would you use to categorize assets and server types into CIDR/IP ranges to exclude or include entire asset categories in rule tests?
From the Offense Summary window, how is the list of rules that contributed to a chained offense identified?
When searching for all events related to "Login Failure", which parameter should a security analyst use to filter the events?
After how much time will QRadar mark an Event offense dormant if no new events or flows occur?
The magnitude rating of an offense in QRadar is calculated based on which values?
A task is set up to identify events that were missed by the Custom Rule Engine. Which two (2) types of events does an analyst look for?


