When a high number of approved exceptions are observed during a review of a control procedure, an organization should FIRST initiate a review of the:
Implementing which of the following controls would BEST reduce the impact of a vulnerability that has been exploited?
When a risk practitioner is building a key risk indicator (KRI) from aggregated data, it is CRITICAL that the data is derived from:
Which of the following would BEST help to ensure that identified risk is efficiently managed?
Which of the following is MOST helpful to management when determining the resources needed to mitigate a risk?
A risk practitioner has been asked to propose a risk acceptance framework for an organization. Which of the following is the MOST important consideration for the risk practitioner to address in the framework?
In the three lines of defense model, a PRIMARY objective of the second line is to:
Which of the following would provide the MOST useful information for communicating an organization’s risk level to senior management?
Which of the following is MOST important when conducting a post-implementation review as part of the system development life cycle (SDLC)?
Which of the following would be a risk practitioner's MOST important action upon learning that an IT control has failed?
Which of the following is the BEST way to determine the ongoing efficiency of control processes?
A risk practitioner has become aware of production data being used in a test environment. Which of the following should be the practitioner's PRIMARY concern?
The BEST key performance indicator (KPI) for monitoring adherence to an organization's user accounts provisioning practices is the percentage of:
An organization is implementing Zero Trust architecture to improve its security posture. Which of the following is the MOST important input to develop the architecture?
Which of the following is the MOST important information to cover a business continuity awareness Ira nine, program for all employees of the organization?
A company has located its computer center on a moderate earthquake fault. Which of the following is the MOST important consideration when establishing a contingency plan and an alternate processing site?
A trusted third-party service provider has determined that the risk of a client's systems being hacked is low. Which of the following would be the client's BEST course of action?
An organization is planning to acquire a new financial system. Which of the following stakeholders would provide the MOST relevant information for analyzing the risk associated with the new IT solution?
Which of the following provides the MOST useful information to assess the magnitude of identified deficiencies in the IT control environment?
A new risk practitioner finds that decisions for implementing risk response plans are not being made. Which of the following would MOST likely explain this situation?
Which of the following is the MOST important consideration when determining whether to accept residual risk after security controls have been implemented on a critical system?
A newly incorporated enterprise needs to secure its information assets From a governance perspective which of the following should be done FIRST?
An organization recently configured a new business division Which of the following is MOST likely to be affected?
A payroll manager discovers that fields in certain payroll reports have been modified without authorization. Which of the following control weaknesses could have contributed MOST to this problem?
Which of the following is the BEST way to determine the value of information assets for risk management purposes?
Which of the following should a risk practitioner do FIRST to support the implementation of governance around organizational assets within an enterprise risk management (ERM) program?
What is the PRIMARY role of the application owner when changes are being introduced into an existing environment?
Which of the following tasks should be completed prior to creating a disaster recovery plan (DRP)?
A risk practitioner has observed that there is an increasing trend of users sending sensitive information by email without using encryption. Which of the following would be the MOST effective approach to mitigate the risk associated with data loss?
Which of the following is the GREATEST concern associated with the transmission of healthcare data across the internet?
A technology company is developing a strategic artificial intelligence (Al)-driven application that has high potential business value. At what point should the enterprise risk profile be updated?
Which of the following is a risk practitioner's BEST course of action upon learning that regulatory authorities have concerns with an emerging technology the organization is considering?
An organization recently experienced a cyber attack that resulted in the loss of confidential customer data. Which of the following is the risk practitioner's BEST recommendation after recovery steps have been completed?
An organization has asked an IT risk practitioner to conduct an operational risk assessment on an initiative to outsource the organization's customer service operations overseas. Which of the following would MOST significantly impact management's decision?
A large organization is replacing its enterprise resource planning (ERP) system and has decided not to deploy the payroll module of the new system. Instead, the current payroll system will continue to be
used. Of the following, who should own the risk if the ERP and payroll system fail to operate as expected?
A large organization needs to report risk at all levels for a new centralized visualization project to reduce cost and improve performance. Which of the following would MOST effectively represent the overall risk of the project to senior management?
Which of the following actions should a risk practitioner do NEXT when an increased industry trend of external cyber attacks is identified?
During implementation of an intrusion detection system (IDS) to monitor network traffic, a high number of alerts is reported. The risk practitioner should recommend to:
An organization has just started accepting credit card payments from customers via the corporate website. Which of the following is MOST likely to increase as a result of this new initiative?
it was determined that replication of a critical database used by two business units failed. Which of the following should be of GREATEST concern1?
When documenting a risk response, which of the following provides the STRONGEST evidence to support the decision?
Which of the following is the BEST way to address IT regulatory compliance risk?
Which of the following risk register updates is MOST important for senior management to review?
What would be MOST helpful to ensuring the effective implementation of a new cybersecurity program?
Which of the following is the MOST important characteristic of an effective risk management program?
An organization recently invested in an identity and access management (IAM) solution to manage user activities across corporate mobile devices. Which of the following is MOST important to update in the risk register?
Which of the following is the BEST criterion to determine whether higher residual risk ratings in the risk register should be accepted?
Which of the following would be MOST helpful to a risk owner when making risk-aware decisions?
A web-based service provider with a low risk appetite for system outages is reviewing its current risk profile for online security. Which of the following observations would be MOST relevant to escalate to senior management?
Malware has recently affected an organization. The MOST effective way to resolve this situation and define a comprehensive risk treatment plan would be to perform:
An organization has initiated a project to implement an IT risk management program for the first time. The BEST time for the risk practitioner to start populating the risk register is when:
Which of the following would BEST facilitate the implementation of data classification requirements?
A risk practitioner finds that data has been misclassified. Which of the following is the GREATEST concern?
Which of the following is the MOST important consideration when determining the appropriate data retention period throughout the data management life cycle?
Who is BEST suited to provide objective input when updating residual risk to reflect the results of control effectiveness?
An organization uses an automated vulnerability scanner to identify potential vulnerabilities on various enterprise systems. Who is accountable for ensuring the vulnerabilities are mitigated?
It is MOST appropriate for changes to be promoted to production after they are:
When creating a separate IT risk register for a large organization, which of the following is MOST important to consider with regard to the existing corporate risk 'register?
A global organization is considering the acquisition of a competitor. Senior management has requested a review of the overall risk profile from the targeted organization. Which of the following components of this review would provide the MOST useful information?
Which of the following BEST helps to identify significant events that could impact an organization?
Several vulnerabilities have been identified in an organization’s core financial systems. Which of the following would be the risk practitioner’s BEST course of action?
A risk assessment has identified increased losses associated with an IT risk scenario. It is MOST important for the risk practitioner to:
Which of the following indicates an organization follows IT risk management best practice?
Which of the following is a responsibility of the second line in the three lines model?
An organization is planning to move its application infrastructure from on-premises to the cloud. Which of the following is the BEST course of the actin to address the risk associated with data transfer if the relationship is terminated with the vendor?
Which of the following is the BEST way to validate privileged access to database accounts?
The implementation of a risk treatment plan will exceed the resources originally allocated for the risk response. Which of the following should be the risk owner's NEXT action?
Which of the following provides the BEST protection for Internet of Things (loT) devices that are accessed within an organization?
During an IT risk scenario review session, business executives question why they have been assigned ownership of IT-related risk scenarios. They feel IT risk is technical in nature and therefore should be owned by IT. Which of the following is the BEST way for the risk practitioner to address these concerns?
Which of the following is MOST helpful when prioritizing action plans for identified risk?
A cloud service provider has completed upgrades to its cloud infrastructure to enhance service availability. Which of the following is the MOST important key risk indicator (KRI) for management to monitor?
Which of the following should a risk practitioner recommend be done prior to disposal of server hardware containing confidential data?
A risk practitioner has been notified of a social engineering attack using artificial intelligence (Al) technology to impersonate senior management personnel. Which of the following would BEST mitigate the impact of such attacks?
Which of the following presents the GREATEST risk to change control in business application development over the complete life cycle?
When developing a risk awareness training program, which of the following training topics would BEST facilitate a thorough understanding of risk scenarios?
Who is accountable for authorizing application access in a cloud Software as a Service (SaaS) solution?
Which of the following is the MOST important consideration when selecting digital signature software?
Which of the following is the BEST way to mitigate the risk associated with fraudulent use of an enterprise's brand on Internet sites?
An organization requires a third party for processing customer personal data. Which of the following is the BEST approach when sharing data over a public network?
Which of the following is the MOST important component in a risk treatment plan?
Which of the following BEST facilities the alignment of IT risk management with enterprise risk management (ERM)?
The PRIMARY benefit of maintaining an up-to-date risk register is that it helps to:
Which of the following will MOST likely change as a result of the decrease in risk appetite due to a new privacy regulation?
Which of the following is the MOST important success factor when introducing risk management in an organization?
A risk practitioner is involved in a comprehensive overhaul of the organizational risk management program. Which of the following should be reviewed FIRST to help identify relevant IT risk scenarios?
An organization's chief information officer (CIO) has proposed investing in a new. untested technology to take advantage of being first to market Senior management has concerns about the success of the project and has set a limit for expenditures before final approval. This conditional approval indicates the organization's risk:
The MOST important reason to aggregate results from multiple risk assessments on interdependent information systems is to:
Which of the following would offer the MOST insight with regard to an organization's risk culture?
Which of the following is the MOST valuable data source to support the optimization of an existing key risk indicator (KRI)?
In response to the threat of ransomware, an organization has implemented cybersecurity awareness activities. The risk practitioner's BEST recommendation to further reduce the impact of ransomware attacks would be to implement:
Which of the following analyses is MOST useful for prioritizing risk scenarios associated with loss of IT assets?
Which of the following is the BEST indication of the effectiveness of a business continuity program?
Which of the following is MOST important to consider when assessing the likelihood that a recently discovered software vulnerability will be exploited?
Which of the following should be the PRIMARY concern when changes to firewall rules do not follow change management requirements?
Which of the following is the GREATEST concern when establishing key risk indicators (KRIs)?
Which of the following BEST indicates the risk appetite and tolerance level (or the risk associated with business interruption caused by IT system failures?
When reporting risk assessment results to senior management, which of the following is MOST important to include to enable risk-based decision making?
When determining the accuracy of a key risk indicator (KRI), it is MOST important that the indicator:
Which of the following activities is PRIMARILY the responsibility of senior management?
The BEST metric to monitor the risk associated with changes deployed to production is the percentage of:
A zero-day vulnerability has been discovered in a globally used brand of hardware server that allows hackers to gain
access to affected IT systems. Which of the following is MOST likely to change as a result of this situation?
Which of the following is the MOST important enabler of effective risk management?
Risk acceptance of an exception to a security control would MOST likely be justified when:
The objective of aligning mitigating controls to risk appetite is to ensure that:
When evaluating a number of potential controls for treating risk, it is MOST important to consider:
Which of the following is the PRIMARY purpose of analyzing control effectiveness during risk analysis?
Which of the following is the GREATEST benefit of identifying appropriate risk owners?
The risk associated with an asset before controls are applied can be expressed as:
An organization is measuring the effectiveness of its change management program to reduce the number of unplanned production changes. Which of the following would be the BEST metric to determine if the program is performing as expected?
Which of the following is the BEST way to validate whether controls to reduce user device vulnerabilities have been implemented according to management's action plan?
Senior management has requested more information regarding the risk associated with introducing a new application into the environment. Which of the following should be done FIRST?
A multinational organization is considering implementing standard background checks to' all new employees A KEY concern regarding this approach
Which of the following BEST facilitates the identification of appropriate key performance indicators (KPIs) for a risk management program?
Which of the following potential scenarios associated with the implementation of a new database technology presents the GREATEST risk to an organization?
The MOST effective way to increase the likelihood that risk responses will be implemented is to:
Who should be responsible for determining which stakeholders need to be involved in the development of a risk scenario?
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?
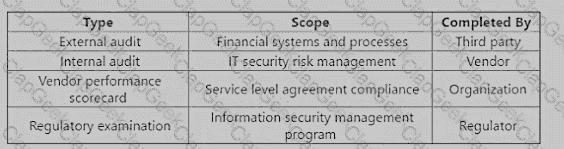
when developing IT risk scenarios associated with a new line of business, which of the following would be MOST helpful to review?
Which of the following is the BEST control to prevent unauthorized access to an organization's critical assets?
Which of the following provides the MOST useful information to senior management about risk mitigation status?
An organization has used generic risk scenarios to populate its risk register. Which of the following presents the GREATEST challenge to assigning of the associated risk entries?
The GREATEST benefit of introducing continuous monitoring to an IT control environment is that it:
Which of the following is the BEST course of action when an organization wants to reduce likelihood in order to reduce a risk level?
Which of the following is the MOST effective way lo ensure professional ethics are maintained as a core organizational value and adhered to by employees?
Which of the following is MOST effective in continuous risk management process improvement?
A recent audit identified high-risk issues in a business unit though a previous control self-assessment (CSA) had good results. Which of the following is the MOST likely reason for the difference?
In an organization where each division manages risk independently, which of the following would BEST enable management of risk at the enterprise level?
An organization becomes aware that IT security failed to detect a coordinated
cyber attack on its data center. Which of the following is the BEST course of
action?
An organization has implemented a policy requiring staff members to take a minimum of five consecutive days' leave per year to mitigate the risk of malicious insider activities. Which of the following is the BEST key performance indicator (KPI) of the effectiveness of this policy?
An organization has initiated a project to launch an IT-based service to customers and take advantage of being the first to market. Which of the following should be of GREATEST concern to senior management?
Which of the following roles is BEST suited to help a risk practitioner understand the impact of IT-related events on business objectives?
A risk practitioner is defining metrics for security threats that were not identified by antivirus software. Which type of metric is being developed?
Which of the following is MOST useful when performing a quantitative risk assessment?
What should a risk practitioner do FIRST when vulnerability assessment results identify a weakness in an application?
A risk practitioner shares the results of a vulnerability assessment for a critical business application with the business manager. Which of the following is the NEXT step?
While reviewing an organization's monthly change management metrics, a risk practitioner notes that the number of emergency changes has increased substantially Which of the following would be the BEST approach for the risk practitioner to take?
Which of the following should be the PRIMARY consideration when assessing the risk of using Internet of Things (loT) devices to collect and process personally identifiable information (PII)?
Which of the following is the BEST key control indicator (KCI) for risk related to IT infrastructure failure?
Senior management has asked a risk practitioner to develop technical risk scenarios related to a recently developed enterprise resource planning (ERP) system. These scenarios will be owned by the system manager. Which of the following would be the BEST method to use when developing the scenarios?
Analyzing trends in key control indicators (KCIs) BEST enables a risk practitioner to proactively identify impacts on an organization's:
Concerned about system load capabilities during the month-end close process, management requires monitoring of the average time to complete tasks and monthly reporting of the findings. What type of measure has been established?
Which of the following is the MOST important requirement for monitoring key risk indicators (KRls) using log analysis?
Which of the following changes would be reflected in an organization's risk profile after the failure of a critical patch implementation?
Which of the following should be considered FIRST when creating a comprehensive IT risk register?
Which of the following practices would be MOST effective in protecting personality identifiable information (Ptl) from unauthorized access m a cloud environment?
Which of the following is MOST important for a risk practitioner to consider when evaluating plans for changes to IT services?
Which of the following is the PRIMARY purpose of periodically reviewing an organization's risk profile?
Which of the following is the BEST way to determine the potential organizational impact of emerging privacy regulations?
Which of The following should be of GREATEST concern for an organization considering the adoption of a bring your own device (BYOD) initiative?
Which of the following is the PRIMARY objective of aggregating the impact of IT risk scenarios and reflecting the results in the enterprise risk register?
Which of the following factors will have the GREATEST impact on the implementation of a risk mitigation strategy for an organization?
Which of the following is the FIRST step when identifying risk items related to a new IT project?
Who is MOST important lo include in the assessment of existing IT risk scenarios?
A risk owner has identified a risk with high impact and very low likelihood. The potential loss is covered by insurance. Which of the following should the risk practitioner do NEXT?
A vendor's planned maintenance schedule will cause a critical application to temporarily lose failover capabilities. Of the following, who should approve this proposed schedule?
Which of the following should be the PRIMARY consideration when implementing controls for monitoring user activity logs?
An organization recently implemented a machine learning-based solution to monitor IT usage and analyze user behavior in an effort to detect internal fraud. Which of the following is MOST likely to be reassessed as a result of this initiative?
A recent risk workshop has identified risk owners and responses for newly identified risk scenarios. Which of the following should be the risk practitioner's NEXT step?
When testing the security of an IT system, il is MOST important to ensure that;
Which of the following is a risk practitioner's BEST course of action upon learning that a control under internal review may no longer be necessary?
Which of the following is MOST important for a risk practitioner to ensure once a risk action plan has been completed?
What should be the PRIMARY objective of updating a risk awareness program in response to a steady rise in cybersecurity threats across the industry?
Which of the following is an IT business owner's BEST course of action following an unexpected increase in emergency changes?
An IT department originally planned to outsource the hosting of its data center at an overseas location to reduce operational expenses. After a risk assessment, the department has decided to keep the data center in-house. How should the risk treatment response be reflected in the risk register?
Which of the following is MOST helpful to ensure effective security controls for a cloud service provider?
Which of the following BEST enables an organization to increase the likelihood of identifying risk associated with unethical employee behavior?
The BEST metric to demonstrate that servers are configured securely is the total number of servers:
A business impact analysis (BIA) has documented the duration of maximum allowable outage for each of an organization's applications. Which of the following MUST be aligned with the maximum allowable outage?
A risk practitioner is advising management on how to update the IT policy framework to account for the organization s cloud usage. Which of the following should be the FIRST step in this process?
A data privacy regulation has been revised to incorporate more stringent requirements for personal data protection. Which of the following provides the MOST important input to help ensure compliance with the revised regulation?
Which of the following is the FIRST step when conducting a business impact analysis (BIA)?
Which of the following should be the PRIMARY consideration when assessing the risk of using Internet of Things (loT) devices to collect and process personally identifiable information (Pll)?
The PRIMARY reason for periodically monitoring key risk indicators (KRIs) is to:
Which strategy employed by risk management would BEST help to prevent internal fraud?
An organization operates in an environment where reduced time-to-market for new software products is a top business priority. Which of the following should be the risk practitioner's GREATEST concern?
Which of the following BEST indicates effective information security incident management?
Which of the following provides the BEST evidence of the effectiveness of an organization's account provisioning process?
An organization's IT team has proposed the adoption of cloud computing as a cost-saving measure for the business. Which of the following should be of GREATEST concern to the risk practitioner?
A risk practitioner wants to identify potential risk events that affect the continuity of a critical business process. Which of the following should the risk practitioner do FIRST?
To define the risk management strategy which of the following MUST be set by the board of directors?
When reviewing a business continuity plan (BCP). which of the following would be the MOST significant deficiency?
A business unit has implemented robotic process automation (RPA) for its
repetitive back-office tasks. Which of the following should be the risk
practitioner's GREATEST concern?
After identifying new risk events during a project, the project manager s NEXT step should be to:
It is MOST important that entries in an organization’s risk register be updated:
Which of the following is the PRIMARY advantage of having a single integrated business continuity plan (BCP) rather than each business unit developing its own BCP?
Which of the following roles would be MOST helpful in providing a high-level view of risk related to customer data loss?
Which of the following would BEST help secure online financial transactions from improper users?
Which of the following BEST enables a risk practitioner to plan a vulnerability assessment that aligns to detailed organizational requirements?
A chief information officer (CIO) has identified risk associated with shadow systems being maintained by business units to address specific functionality gaps in the organization'senterprise resource planning (ERP) system. What is the BEST way to reduce this risk going forward?
Which of the following should be included in a risk scenario to be used for risk analysis?
Which of the following is the BEST metric to demonstrate the effectiveness of an organization's patch management process?
Which of the following is MOST important information to review when developing plans for using emerging technologies?
A penetration testing team discovered an ineffectively designed access control. Who is responsible for ensuring the control design gap is remediated?
Which of the following is the MOST important element of a successful risk awareness training program?
Which of the following controls would BEST mitigate the risk of user passwords being compromised by a man in the middle technique?
Which of the following is the MOST significant benefit of using quantitative risk analysis instead of qualitative risk analysis?
When creating a program to manage data privacy risk, which of the following is MOST important to ensure that the program is successful?
Which of the following presents the GREATEST challenge to managing an organization's end-user devices?
An organization's stakeholders are unable to agree on appropriate risk responses. Which of the following would be the BEST course of action?
Which of the following would MOST effectively reduce risk associated with an increase of online transactions on a retailer website?
Which of the following is MOST likely to cause a key risk indicator (KRI) to exceed thresholds?
Which of the following s MOST likely to deter an employee from engaging in inappropriate use of company owned IT systems?
The MAIN reason for prioritizing IT risk responses is to enable an organization to:
Which of the following would provide the BEST evidence of an effective internal control environment/?
Which of the following is the GREATEST concern when an organization uses a managed security service provider as a firewall administrator?
Which of the following is the BEST way to mitigate the risk to IT infrastructure availability?
Which of the following is the BEST recommendation to senior management when the results of a risk and control assessment indicate a risk scenario can only be partially mitigated?
Which key performance indicator (KPI) BEST measures the effectiveness of an organization's disaster recovery program?
As part of its risk strategy, an organization decided to transition its financial system from a cloud-based provider to an internally managed system. Which of the following should the risk practitioner do FIRST?
The MOST important measure of the effectiveness of risk management in project implementation is the percentage of projects:
When developing risk treatment alternatives for a Business case, it is MOST helpful to show risk reduction based on:
Which of the following is MOST important to review when determining whether a potential IT service provider’s control environment is effective?
After several security incidents resulting in significant financial losses, IT management has decided to outsource the security function to a third party that provides 24/7 security operation services. Which risk response option has management implemented?
Who should be accountable for monitoring the control environment to ensure controls are effective?
Which of the following is the BEST indicator of an effective IT security awareness program?
Which of the following is the PRIMARY reason for an organization to ensure the risk register is updated regularly?
Which of the following would BEST mitigate the risk associated with reputational damage from inappropriate use of social media sites by employees?
A poster has been displayed in a data center that reads. "Anyone caught taking photographs in the data center may be subject to disciplinary action." Which of the following control types has been implemented?
Which of the following provides the BEST evidence that a selected risk treatment plan is effective?
Which of the following BEST indicates whether security awareness training is effective?
Which of the following is MOST important to ensure when reviewing an organization's risk register?
During an IT department reorganization, the manager of a risk mitigation action plan was replaced. The new manager has begun implementing a new control after identifying a more effective option. Which of the following is the risk practitioner's BEST course of action?
Which of the following would be MOST helpful to an information security management team when allocating resources to mitigate exposures?
What should be the PRIMARY driver for periodically reviewing and adjusting key risk indicators (KRIs)?
Which of the following outcomes of disaster recovery planning is MOST important to enable the initiation of necessary actions during a disaster?
Which of the following is the PRIMARY purpose of creating and documenting control procedures?
Which of the following data would be used when performing a business impact analysis (BIA)?
Which of the following provides the BEST evidence that robust risk management practices are in place within an organization?
When defining thresholds for control key performance indicators (KPIs). it is MOST helpful to align:
Which of the following is MOST important to the successful development of IT risk scenarios?
A key risk indicator (KRI) for technology operations has been above risk thresholds for the last three reporting periods. What is the BEST way for a risk practitioner to address this concern?
During the creation of an organization's IT risk management program, the BEST time to identify key risk indicators (KRIs) is while:
Which of the following will BEST ensure that information security risk factors are mitigated when developing in-house applications?
Which of the following is the GREATEST benefit of having a mature enterprise architecture (EA) in place?
Which of the following would BEST help identify the owner for each risk scenario in a risk register?
Which of the following should be considered FIRST when assessing risk associated with the adoption of emerging technologies?
A migration from an in-house developed system to an external cloud-based solution is affecting a previously rated key risk scenario related to payroll processing. Which part of the risk register should be updated FIRST?
Which of the following approaches BEST identifies information systems control deficiencies?
Which of the following is the MOST important information to be communicated during security awareness training?
An organization is increasingly concerned about loss of sensitive data and asks the risk practitioner to assess the current risk level. Which of the following should the risk practitioner do FIRST?
Which of the following BEST helps to identify significant events that could impact an organization?
Vulnerability analysis
Which of the following is the PRIMARY reason to aggregate risk assessment results from different business units?
Which of the following attributes of a key risk indicator (KRI) is MOST important?
After conducting a risk assessment for regulatory compliance, an organization has identified only one possible mitigating control. The cost of the control has been determined to be higher than the penalty of noncompliance. Which of the following would be the risk practitioner's BEST recommendation?
If concurrent update transactions to an account are not processed properly, which of the following will MOST likely be affected?
Which of the following scenarios is MOST important to communicate to senior management?
Print jobs containing confidential information are sent to a shared network printer located in a secure room. Which of the following is the BEST control to prevent the inappropriate disclosure of confidential information?
Which of the following provides the BEST evidence that risk mitigation plans have been implemented effectively?
Which of the following cloud service models is MOST appropriate for client organizations that want to maximize their control over management of the data life cycle?
Which of the following is a PRIMARY objective of privacy impact assessments (PIAs)?
A risk practitioner identifies a database application that has been developed and implemented by the business independently of IT. Which of the following is the BEST course of action?
Which of the following should be the PRIMARY driver for an organization on a multi-year cloud implementation to publish a cloud security policy?
Which of the following is the PRIMARY role of the second line when an IT risk management framework is adopted?
An organization's senior management is considering whether to acquire cyber insurance. Which of the following is the BEST way for the risk practitioner to enable management’s decision?
Which of the following is MOST useful for measuring the existing risk management process against a desired state?
Which of the following is the MAIN reason for documenting the performance of controls?
Which of the following BEST mitigates the risk of violating privacy laws when transferring personal information lo a supplier?
Which of the following would be MOST useful when measuring the progress of a risk response action plan?
An information system for a key business operation is being moved from an in-house application to a Software as a Service (SaaS) vendor. Which of the following will have the GREATEST impact on the ability to monitor risk?
Which of the following is MOST important for maintaining the effectiveness of an IT risk register?
Which of the following will BEST help to ensure implementation of corrective action plans?
A risk practitioner is collaborating with key stakeholders to prioritize a large number of IT risk scenarios. Which scenarios should receive the PRIMARY focus?
An organization is analyzing the risk of shadow IT usage. Which of the following is the MOST important input into the assessment?
Several newly identified risk scenarios are being integrated into an organization's risk register. The MOST appropriate risk owner would be the individual who:
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of an anti-virus program?
Recent penetration testing of an organization's software has identified many different types of security risks. Which of the following is the MOST likely root cause for the identified risk?
A key risk indicator (KRI) indicates a reduction in the percentage of appropriately patched servers. Which of the following is the risk practitioner's BEST course of action?
The use of multi-factor authentication (MFA) when applied to an FTP connection is an example of which type of control category?
Senior management is deciding whether to share confidential data with the organization's business partners. The BEST course of action for a risk practitioner would be to submit a report to senior management containing the:
Which of the following IT key risk indicators (KRIs) provides management with the BEST feedback on IT capacity?
Which of the following will be the GREATEST concern when assessing the risk profile of an organization?
Which of the following is the MOST efficient method for monitoring control effectiveness?
Which of the following BEST supports the integration of IT risk management into an organization's strategic planning?
Which of the following is MOST important to enable well-informed cybersecurity risk decisions?
Which of the following aspects of an IT risk and control self-assessment would be MOST important to include in a report to senior management?
Which of the following is the GREATEST benefit to an organization when updates to the risk register are made promptly after the completion of a risk assessment?
To reduce the risk introduced when conducting penetration tests, the BEST mitigating control would be to:
Which of the following is the BEST response when a potential IT control deficiency has been identified?
Which of the following is the MOST important input when developing risk scenarios?
Which of the following provides The MOST useful information when determining a risk management program's maturity level?
Which of the following is the BEST indicator of the effectiveness of a control monitoring program?
A large organization recently restructured the IT department and has decided to outsource certain functions. What action should the control owners in the IT department take?
Which of the following is the BEST way to quantify the likelihood of risk materialization?
Which of the following is the BEST method to mitigate the risk of an unauthorized employee viewing confidential data in a database''
Who is BEST suited to provide information to the risk practitioner about the effectiveness of a technical control associated with an application?
Which of the following will BEST help to improve an organization's risk culture?
A service provider is managing a client’s servers. During an audit of the service, a noncompliant control is discovered that will not be resolved before the next audit because the client cannot afford the downtime required to correct the issue. The service provider’s MOST appropriate action would be to:
Which of the following is the BEST key control indicator (KCI) for measuring the security of a blockchain network?
Which of the following is the PRIMARY benefit of identifying and communicating with stakeholders at the onset of an IT risk assessment?
Which of the following is the MOST important objective of regularly presenting the project risk register to the project steering committee?
An organization outsources the processing of us payroll data A risk practitioner identifies a control weakness at the third party trial exposes the payroll data. Who should own this risk?
An organization is unable to implement a multi-factor authentication requirement until the next fiscal year due to budget constraints. Consequently, a policy exception must be submitted. Which of the following is MOST important to include in the analysis of the exception?
While reviewing the risk register, a risk practitioner notices that different business units have significant variances in inherent risk for the same risk scenario. Which of the following is the BEST course of action?
Which of the following is the MAIN benefit of involving stakeholders in the selection of key risk indicators (KRIs)?
A risk practitioner has learned that the number of emergency change management tickets without subsequent approval has doubled from the same period of the previous year. Which of the following is the MOST important action for the risk practitioner to take?
Which of the following is MOST important for an organization that wants to reduce IT operational risk?
Which of the following is the MOST comprehensive resource for prioritizing the implementation of information systems controls?
Which of the following is the MOST appropriate key control indicator (KCI) to help an organization prevent successful cyber risk events on the external-facing infrastructure?
An organization's risk practitioner learns a new third-party system on the corporate network has introduced vulnerabilities that could compromise corporate IT systems. What should the risk practitioner do
FIRST?
Which of the following is a risk practitioner's BEST recommendation to help reduce IT risk associated with scheduling overruns when starting a new application development project?
The PRIMARY reason for periodic penetration testing of Internet-facing applications is to:
An organization maintains independent departmental risk registers that are not automatically aggregated. Which of the following is the GREATEST concern?
Which of the following is the PRIMARY reason for an organization to include an acceptable use banner when users log in?
An organization has established workflows in its service desk to support employee reports of security-related concerns. Which of the following is the MOST efficient approach to analyze these concerns?
A risk practitioner is performing a risk assessment of recent external advancements in quantum computing. Which of the following would pose the GREATEST concern for the risk practitioner?
A deficient control has been identified which could result in great harm to an organization should a low frequency threat event occur. When communicating the associated risk to senior management the risk practitioner should explain:
Who should be responsible (of evaluating the residual risk after a compensating control has been
A company has recently acquired a customer relationship management (CRM) application from a certified software vendor. Which of the following will BE ST help lo prevent technical vulnerabilities from being exploded?
Which of the following provides the MOST useful input to the development of realistic risk scenarios?
Which of the following BEST measures the efficiency of an incident response process?
Which of the following should be the risk practitioner s PRIMARY focus when determining whether controls are adequate to mitigate risk?
The analysis of which of the following will BEST help validate whether suspicious network activity is malicious?
Which of the following functions can be performed by any of the three lines of defense?
Which of the following should be a risk practitioner's GREATEST concern upon learning of failures in a data migration activity?
An organization is outsourcing a key database to be hosted by an external service provider. Who is BEST suited to assess the impact of potential data loss?
Which of the following is the BEST way to ensure data is properly sanitized while in cloud storage?
Which of the following is MOST effective against external threats to an organizations confidential information?
Which of the following is MOST important to ensure before using risk reports in decision making?
Which of the following is the BEST approach when a risk practitioner has been asked by a business unit manager for special consideration during a risk assessment of a system?
An organization has been notified that a disgruntled, terminated IT administrator has tried to break into the corporate network. Which of the following discoveries should be of GREATEST concern to the organization?
When updating a risk register with the results of an IT risk assessment, the risk practitioner should log:
Management has required information security awareness training to reduce the risk associated with credential compromise. What is the BEST way to assess the effectiveness of the training?
From a risk management perspective, the PRIMARY objective of using maturity models is to enable:
Which of the following is the PRIMARY reason to establish the root cause of an IT security incident?
Which of the following is the PRIMARY risk management responsibility of the third line of defense?
Days before the realization of an acquisition, a data breach is discovered at the company to be acquired. For the accruing organization, this situation represents which of the following?
Which of the following would MOST likely drive the need to review and update key performance indicators (KPIs) for critical IT assets?
Which of the following BEST represents a critical threshold value for a key control indicator (KCI)?
Which of the following is the MOST important characteristic when designing a key risk indicator (KRI)?
Which of the following would be MOST helpful in assessing the risk associated with data loss due to human vulnerabilities?
The PRIMARY advantage of involving end users in continuity planning is that they:
Which of the following would be MOST useful to senior management when determining an appropriate risk response?
Which of the following is MOST helpful in aligning IT risk with business objectives?
Which of the following is the PRIMARY reason for logging in a production database environment?
Which of the following should a risk practitioner review FIRST when evaluating risk events associated with the organization's data flow model?
Which of the following should be the risk practitioner s FIRST course of action when an organization has decided to expand into new product areas?
An organization is increasingly concerned about loss of sensitive data and asks the risk practitioner to assess the current risk level. Which of the following should the risk practitioner do FIRST?
Which of the following will BEST help to ensure new IT policies address the enterprise's requirements?
Which of the following is the BEST approach when a risk practitioner has been asked by a business unit manager to exclude an in-scope system from a risk assessment?
Which of the following risk scenarios would be the GREATEST concern as a result of a single sign-on implementation?
Which of the following is the MOST important consideration for a risk practitioner when making a system implementation go-live recommendation?
Which of the following would be a risk practitioners’ BEST recommendation for preventing cyber intrusion?
The risk associated with data loss from a website which contains sensitive customer information is BEST owned by:
Which of the following is a KEY consideration for a risk practitioner to communicate to senior management evaluating the introduction of artificial intelligence (Al) solutions into the organization?
An IT risk practitioner has been asked to regularly report on the overall status and effectiveness of the IT risk management program. Which of the following is MOST useful for this purpose?
During a risk treatment plan review, a risk practitioner finds the approved risk action plan has not been completed However, there were other risk mitigation actions implemented. Which of the fallowing is the BEST course of action?
An organization planning to transfer and store its customer data with an offshore cloud service provider should be PRIMARILY concerned with:
Which of the following can be interpreted from a single data point on a risk heat map?
Of the following, whose input is ESSENTIAL when developing risk scenarios for the implementation of a third-party mobile application that stores customer data?
Which of the following controls BEST enables an organization to ensure a complete and accurate IT asset inventory?
Which of the following will BEST help ensure that risk factors identified during an information systems review are addressed?
Which of the following should be the FIRST step when a company is made aware of new regulatory requirements impacting IT?
A risk assessment has identified that an organization may not be in compliance with industry regulations. The BEST course of action would be to:
For no apparent reason, the time required to complete daily processing for a legacy application is approaching a risk threshold. Which of the following activities should be performed FIRST?
When establishing leading indicators for the information security incident response process it is MOST important to consider the percentage of reported incidents:
A risk practitioner has identified that the agreed recovery time objective (RTO) with a Software as a Service (SaaS) provider is longer than the business expectation. Which of the following is the risk practitioner's BEST course of action?
Which of the following is the BEST approach to mitigate the risk associated with outsourcing network management to an external vendor who will have access to sensitive information assets?
Which of the following is MOST important to ensure when continuously monitoring the performance of a client-facing application?
Which of the following is the PRIMARY concern for a risk practitioner regarding an organization's adoption of innovative big data analytics capabilities?
Periodically reviewing and updating a risk register with details on identified risk factors PRIMARILY helps to:
Which of the following is the MOST important objective of an enterprise risk management (ERM) program?
Which of the following requirements is MOST important to include in an outsourcing contract to help ensure sensitive data stored with a service provider is secure?
Which of the following is the MOST important reason to communicate control effectiveness to senior management?
During a review of the asset life cycle process, a risk practitioner identified several unreturned and unencrypted laptops belonging to former employees. Which of the following is the GREATEST concern with this finding?
Which of the following is MOST helpful in verifying that the implementation of a risk mitigation control has been completed as intended?
A control owner responsible for the access management process has developed a machine learning model to automatically identify excessive access privileges. What is the risk practitioner's BEST course of action?
Which of the following is the MOST important reason for a risk practitioner to identify stakeholders for each IT risk scenario?
Which of the following activities is a responsibility of the second line of defense?
When communicating changes in the IT risk profile, which of the following should be included to BEST enable stakeholder decision making?
Which of the following provides the MOST helpful information in identifying risk in an organization?
Which of the following is the MOST important consideration when sharing risk management updates with executive management?
An organization is concerned that its employees may be unintentionally disclosing data through the use of social media sites. Which of the following will MOST effectively mitigate tins risk?
Which of the following is MOST important to identify when developing generic risk scenarios?
Which of the following activities would BEST contribute to promoting an organization-wide risk-aware culture?
Which of the following is the BEST way for a risk practitioner to present an annual risk management update to the board''
When developing a new risk register, a risk practitioner should focus on which of the following risk management activities?
Which of the following is MOST important to identify when developing top-down risk scenarios?
An organization's Internet-facing server was successfully attacked because the server did not have the latest security patches. The risk associated with poor patch management had been documented in the risk register and accepted. Who should be accountable for any related losses to the organization?
A risk practitioner notes control design changes when comparing risk response to a previously approved action plan. Which of the following is MOST important for the practitioner to confirm?
During the control evaluation phase of a risk assessment, it is noted that multiple controls are ineffective. Which of the following should be the risk practitioner's FIRST course of action?
A risk practitioner is organizing risk awareness training for senior management. Which of the following is the MOST important topic to cover in the training session?
Which of the following is MOST helpful in developing key risk indicator (KRl) thresholds?
Which of the following is the BEST way to ensure ongoing control effectiveness?
Which of the following is MOST important for a risk practitioner to consider when determining the control requirements for data privacy arising from emerging technologies?
Which of the following is the GREATEST impact of implementing a risk mitigation strategy?
An organization has outsourced its IT security operations to a third party. Who is ULTIMATELY accountable for the risk associated with the outsourced operations?
While evaluating control costs, management discovers that the annual cost exceeds the annual loss expectancy (ALE) of the risk. This indicates the:
An incentive program is MOST likely implemented to manage the risk associated with loss of which organizational asset?
Which of the following is MOST helpful to understand the consequences of an IT risk event?
An organization has an internal control that requires all access for employees be removed within 15 days of their termination date. Which of the following should the risk practitioner use to monitor
adherence to the 15-day threshold?
Which of the following provides the MOST up-to-date information about the effectiveness of an organization's overall IT control environment?
An organization has identified that terminated employee accounts are not disabled or deleted within the time required by corporate policy. Unsure of the reason, the organization has decided to monitor the situation for three months to obtain more information. As a result of this decision, the risk has been:
The PRIMARY reason for establishing various Threshold levels for a set of key risk indicators (KRIs) is to:
A key performance indicator (KPI) has been established to monitor the number of software changes that fail and must be re-implemented. An increase in the KPI indicates an ineffective:
The risk associated with an asset after controls are applied can be expressed as:
Which of the following provides the MOST important information to facilitate a risk response decision?
Which of the following is the MOST essential factor for managing risk in a highly dynamic environment?
Which of the following is MOST important for management to consider when deciding whether to invest in an IT initiative that exceeds management's risk appetite?
It is MOST important that security controls for a new system be documented in:
Which of the following is the PRIMARY reason for a risk practitioner to use global standards related to risk management?
To enable effective risk governance, it is MOST important for senior management to:
Which of the following changes would be reflected in an organization's risk profile after the failure of a critical patch implementation?
When of the following is the BEST key control indicator (KCI) to determine the effectiveness of en intrusion prevention system (IPS)?
Which of the following is MOST likely to be impacted as a result of a new policy which allows staff members to remotely connect to the organization's IT systems via personal or public computers?
An organization is implementing data warehousing infrastructure. Senior management is concerned about safeguarding client data security in this new environment. Which of the following should the risk practitioner recommend be done NEXT?
Within the three lines of defense model, the responsibility for managing risk and controls resides with:
Which of the following is the MOST important reason for integrating IT risk management practices into enterprise risk management (ERM)?
Which of the following would provide the MOST comprehensive information for updating an organization's risk register?
Which of the following would be MOST useful to management when allocating resources to mitigate risk to the organization?
Which of the following is the BEST way to manage the risk associated with malicious activities performed by database administrators (DBAs)?
Which of the following would MOST effectively enable a business operations manager to identify events exceeding risk thresholds?
A risk practitioner has been asked to mark an identified control deficiency as remediated, despite concerns that the risk level is still too high. Which of the following is the BEST way to address this concern?
When developing risk scenario using a list of generic scenarios based on industry best practices, it is MOST imported to:
A risk action plan has been changed during the risk mitigation effort. Which of the following is MOST important for the risk practitioner to verify?
The software version of an enterprise's critical business application has reached end-of-life and is no longer supported by the vendor. IT has decided to develop an in-house replacement application. Which of the following should be the PRIMARY concern?
A risk practitioner discovers that an IT operations team manager bypassed web filtering controls by using a mobile device, in violation of the network security policy. Which of the following should the risk practitioner do FIRST?
An organization is considering outsourcing user administration controls tor a critical system. The potential vendor has offered to perform quarterly sett-audits of its controls instead of having annual independent audits. Which of the following should be of GREATEST concern to me risk practitioner?
A vendor’s planned maintenance schedule will cause a critical application to temporarily lose failover capabilities. Of the following, who should approve this proposed schedule?
In order to determining a risk is under-controlled the risk practitioner will need to
Which of the following is the MOST important consideration when developing risk strategies?
After a business unit implemented an Internet of Things (IoT) solution, the organization became aware of an emerging risk from the interoperability of IoT devices. Which of the following should be done FIRST in response to this situation?
In an organization dependent on data analytics to drive decision-making, which of the following would BEST help to minimize the risk associated with inaccurate data?
Upon learning that the number of failed backup attempts continually exceeds
the current risk threshold, the risk practitioner should:
Which of the following is the BEST key performance indicator (KPI) to measure how effectively risk management practices are embedded in the project management office (PMO)?
An organization is moving its critical assets to the cloud. Which of the following is the MOST important key performance indicator (KPI) to include in the service level agreement (SLA)?
A key risk indicator (KRI) that incorporates data from external open-source threat intelligence sources has shown changes in risk trend data. Which of the following is MOST important to update in the risk register?
Which of the following is the MOST important consideration when performing a risk assessment of a fire suppression system within a data center?
Which of the following should be done FIRST when a new risk scenario has been identified
Which of the following is the BEST evidence that risk management is driving business decisions in an organization?
Which of the following BEST facilitates the process of documenting risk tolerance?
Which of the following is the MOST important metric to monitor the performance of the change management process?
Which of the following provides the MOST reliable evidence of a control's effectiveness?
Which of the following is MOST helpful in defining an early-warning threshold associated with insufficient network bandwidth’’?
Which of the following is the GREATEST benefit of incorporating IT risk scenarios into the corporate risk register?
Which of the following will BEST communicate the importance of risk mitigation initiatives to senior management?
Which of the following is MOST important for a multinational organization to consider when developing its security policies and standards?
Which of the following is MOST important for a risk practitioner to verify when periodically reviewing risk response action plans?
Which of the following is the MOST critical factor to consider when determining an organization's risk appetite?
When of the following 15 MOST important when developing a business case for a proposed security investment?
Which of the following is the MOST significant risk related to an organization's use of AI technology?
Which of the following is the MOST effective way for a large and diversified organization to minimize risk associated with unauthorized software on company devices?
The FIRST step for a startup company when developing a disaster recovery plan (DRP) should be to identify:
Which of the following MUST be assessed before considering risk treatment options for a scenario with significant impact?
Which of the following is the MOST important concern when assigning multiple risk owners for an identified risk?
A failure in an organization s IT system build process has resulted in several computers on the network missing the corporate endpoint detection and response (EDR) software. Which of the following should be the risk practitioner’s IMMEDIATE concern?
Which of the following is the GREATEST risk associated with the use of data analytics?
Which of the following should be the MOST important consideration when performing a vendor risk assessment?
Which of the following would MOST likely cause management to unknowingly accept excessive risk?
After the implementation of a blockchain solution, a risk practitioner discovers noncompliance with new industry regulations. Which of the following is the MOST important course of action prior to informing senior management?
Which of the following is MOST important to consider when determining the risk associated with re-identification of obfuscated personal data?
To communicate the risk associated with IT in business terms, which of the following MUST be defined?
Which of the following is MOST important to review when an organization needs to transition the majority of its employees to remote work during a crisis?
Who should be responsible for approving the cost of controls to be implemented for mitigating risk?
A control process has been implemented in response to a new regulatory requirement, but has significantly reduced productivity. Which of the following is the BEST way to resolve this concern?
When reviewing a risk response strategy, senior management's PRIMARY focus should be placed on the:
A recent risk workshop has identified risk owners and responses for newly identified risk scenarios. Which of the following should be the risk practitioner s NEXT step? r
A systems interruption has been traced to a personal USB device plugged into the corporate network by an IT employee who bypassed internal control procedures. Of the following, who should be accountable?
The risk associated with inadvertent disclosure of database records from a public cloud service provider (CSP) would MOST effectively be reduced by:
A peer review of a risk assessment finds that a relevant threat community was not included. Mitigation of the risk will require substantial changes to a software application. Which of the following is the BEST course of action?
An organization that has been the subject of multiple social engineering attacks is developing a risk awareness program. The PRIMARY goal of this program should be to:
A risk practitioner observes that the fraud detection controls in an online payment system do not perform as expected. Which of the following will MOST likely change as a result?
Which of these documents is MOST important to request from a cloud service
provider during a vendor risk assessment?
An organization has established a single enterprise-wide risk register that records high-level risk scenarios. The IT risk department has created its own register to record more granular scenarios applicable to IT. Which of the following is the BEST way to ensure alignment between these two registers?
An organization has opened a subsidiary in a foreign country. Which of the following would be the BEST way to measure the effectiveness of the subsidiary's IT systems controls?
Which of the following BEST helps to mitigate risk associated with excessive access by authorized users?
Which of the following is the MAIN benefit to an organization using key risk indicators (KRIs)?
Which of the following will BEST help to ensure key risk indicators (KRIs) provide value to risk owners?
An organization's business gap analysis reveals the need for a robust IT risk strategy. Which of the following should be the risk practitioner's PRIMARY consideration when participating in development of the new strategy?
A financial institution has identified high risk of fraud in several business applications. Which of the following controls will BEST help reduce the risk of fraudulent internal transactions?
Which of the following is of GREATEST concern when uncontrolled changes are made to the control environment?
From a governance perspective, which of the following is MOST important to ensure when risk management policies are being updated to facilitate the pursuit of new opportunities?
IT stakeholders have asked a risk practitioner for IT risk profile reports associated with specific departments to allocate resources for risk mitigation. The BEST way to address this request would be to use:
Which of the following is the PRIMARY reason to have the risk management process reviewed by a third party?
Which of the following is the BEST indication that key risk indicators (KRIs) should be revised?
How does the identification of risk scenarios contribute to effective IT risk management?
Which of the following is MOST helpful in determining the effectiveness of an organization's IT risk mitigation efforts?
Which of the following is the MOST important requirement when implementing a data loss prevention (DLP) system?
While conducting an organization-wide risk assessment, it is noted that many of the information security policies have not changed in the past three years. The BEST course of action is to:
Which of the following should a risk practitioner recommend FIRST when an increasing trend of risk events and subsequent losses has been identified?
Which of the following should be a risk practitioner's PRIMARY focus when tasked with ensuring organization records are being retained for a sufficient period of time to meet legal obligations?
Which of the following is the MOST significant indicator of the need to perform a penetration test?
An organization is subject to a new regulation that requires nearly real-time recovery of its services following a disruption. Which of the following is the BEST way to manage the risk in this situation?
Which of the following should be of MOST concern to a risk practitioner reviewing an organization risk register after the completion of a series of risk assessments?
A risk practitioner identifies an increasing trend of employees copying company information unrelated to their job functions to USB drives. Which of the following elements of the risk register should be updated to reflect this observation?
Which of the following is the BEST control to minimize the risk associated with scope creep in software development?
Which of the following is the FIRST step when developing a business case to drive the adoption of a risk remediation project by senior management?
Which of the following is the GREATEST risk associated with inappropriate classification of data?
Which of the following should be a risk practitioner’s MOST important consideration when developing IT risk scenarios?
Who is the BEST person to an application system used to process employee personal data?
Which of the following should be used as the PRIMARY basis for evaluating the state of an organization's cloud computing environment against leading practices?
An internal audit report reveals that not all IT application databases have encryption in place. Which of the following information would be MOST important for assessing the risk impact?
Which of the following would BEST help to address the risk associated with malicious outsiders modifying application data?
Which of the following approaches MOST effectively enables accountability for data protection?
What is the MOST important consideration when aligning IT risk management with the enterprise risk management (ERM) framework?
A risk practitioner has received an updated enterprise risk management (ERM) report showing that residual risk is now within the organization's defined appetite and tolerance levels. Which of the following is the risk practitioner's BEST course of action?
Which of the following should be the PRIMARY focus of a disaster recovery management (DRM) framework and related processes?
Which of the following is the MOST effective way to mitigate identified risk scenarios?
Which of the following should an organization perform to forecast the effects of a disaster?
An application development team has a backlog of user requirements for a new system that will process insurance claim payments for customers. Which of the following should be the MOST important consideration for a risk-based review of the user requirements?
Which of the following would BEST help an enterprise define and communicate its risk appetite?
An audit reveals that several terminated employee accounts maintain access. Which of the following should be the FIRST step to address the risk?
A risk practitioner has identified that the organization's secondary data center does not provide redundancy for a critical application. Who should have the authority to accept the associated risk?
Which of the following would be MOST helpful when communicating roles associated with the IT risk management process?
Zero Trust architecture is designed and deployed with adherence to which of the following basic tenets?
Which of the following is the BEST evidence that a user account has been properly authorized?
Which of the following would provide the MOST helpful input to develop risk scenarios associated with hosting an organization's key IT applications in a cloud environment?
Which type of cloud computing deployment provides the consumer the GREATEST degree of control over the environment?
A business unit has decided to accept the risk of implementing an off-the-shelf, commercial software package that uses weak password controls. The BEST course of action would be to:
Which of the following should be the starting point when performing a risk analysis for an asset?
An organization operates in an environment where the impact of ransomware attacks is high, with a low likelihood. After quantifying the impact of the risk associated with ransomware attacks exceeds the organization's risk appetite and tolerance, which of the following is the risk practitioner's BEST recommendation?
Which of the following helps ensure compliance with a nonrepudiation policy requirement for electronic transactions?


