A cloud administrator checked out the deployment scripts used to deploy the sandbox environment to a public cloud provider. The administrator modified the script to add an application load balancer in front of the web- based front-end application. The administrator next used the script to recreate a new sandbox environment successfully, and the application was then using the new load balancer.
The following week, a new update was required to add more front-end servers to the sandbox environment. A second administrator made the necessary changes and checked out the deployment scripts. The second administrator then ran the script, but the application load balancer was missing from the new deployment.
Which of the following is the MOST likely reason for this issue?
After analyzing a web server’s logs, a systems administrator sees that users are connecting to the company’s application through HTTP instead of HTTPS. The administrator then configures a redirect from HTTP to HTTPS on the web server, and the application responds with a connection time-out message.
Which of the following should the administrator verify NEXT?
A technician is working with an American company that is using cloud services to provide video-based training for its customers. Recently, due to a surge in demand, customers in Europe are experiencing latency.
Which of the following services should the technician deploy to eliminate the latency issue?
A systems administrator in a large enterprise needs to alter the configuration of one of the finance department’s database servers.
Which of the following should the administrator perform FIRST?
An organization is hosting a DNS domain with private and public IP ranges.
Which of the following should be implemented to achieve ease of management?
A systems administrator is deploying a GPU-accelerated VDI solution. Upon requests from several users, the administrator installs an older version of the OS on their virtual workstations. The majority of the VMs run the latest LTS version of the OS.
Which of the following types of drivers will MOST likely ensure compatibility will all virtual workstations?
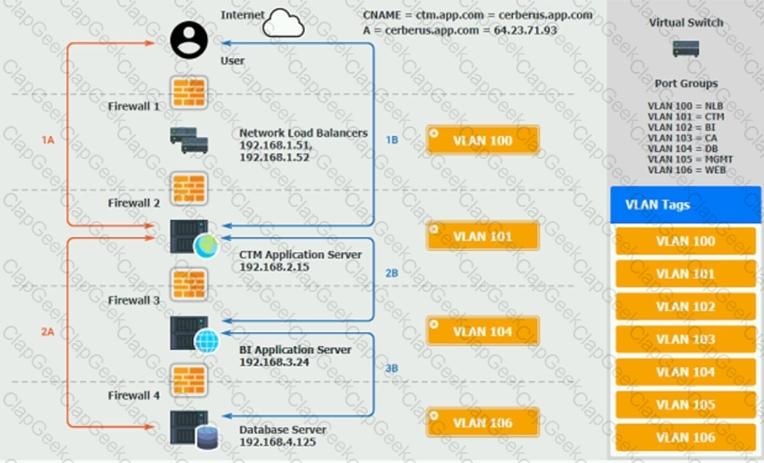
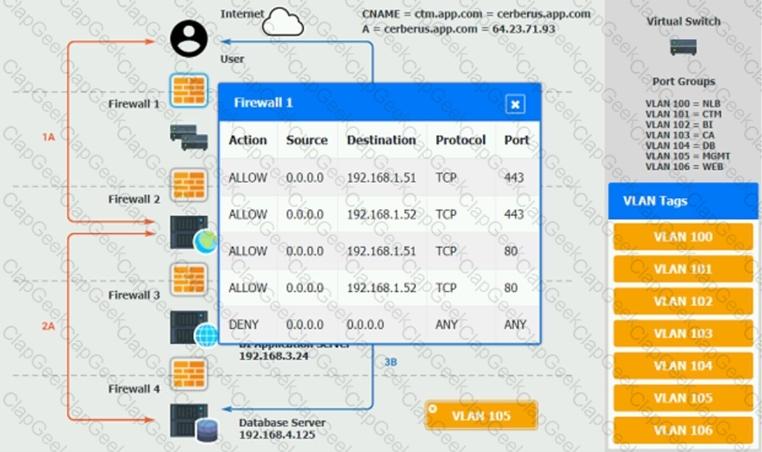
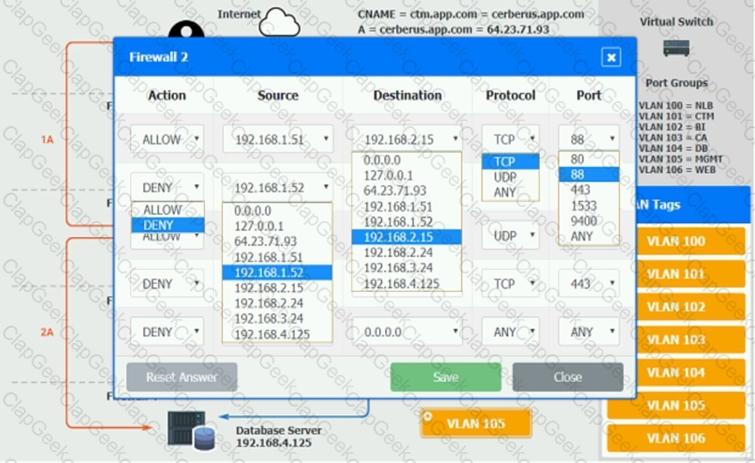
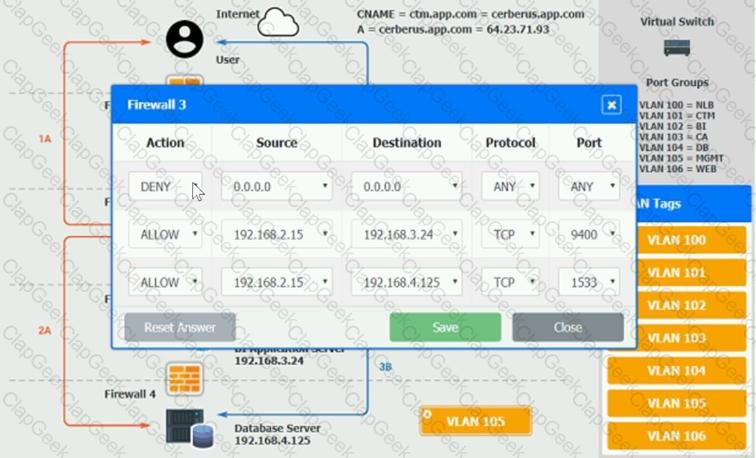
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.
1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An application deployment team has observed delays in deployments and has asked the cloud administrator to evaluate the issue. Below is the result of a latency test that was conducted by the cloud administrator from offices located in the following regions:
• Asia-Pacific (APAC)
• Europe, the Middle East, and Africa (EMEA)
• Americas
Tests were conducted from each location, and the results are shown below:
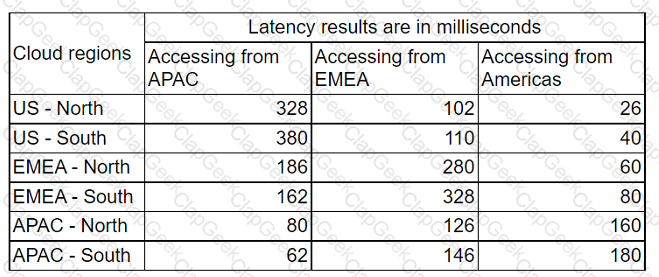
Which of the following locations needs to be investigated further?
An organization’s web server farm, which is hosted in the cloud with DNS load balancing, is experiencing a spike in network traffic. This has caused an outage of the organization’s web server infrastructure.
Which of the following should be implemented to prevent this in the future as a mitigation method?
An OS administrator is reporting slow storage throughput on a few VMs in a private IaaS cloud. Performance graphs on the host show no increase in CPU or memory. However, performance graphs on the storage show a decrease of throughput in both IOPS and MBps but not much increase in latency. There is no increase in workload, and latency is stable on the NFS storage arrays that are used by those VMs.
Which of the following should be verified NEXT?
A cloud administrator is reviewing the authentication and authorization mechanism implemented within the cloud environment. Upon review, the administrator discovers the sales group is part of the finance group, and the sales team members can access the financial application. Single sign-on is also implemented, which makes access much easier.
Which of the following access control rules should be changed?
Lateral-moving malware has infected the server infrastructure.
Which of the following network changes would MOST effectively prevent lateral movement in the future?
A cloud administrator is reviewing a new application implementation document. The administrator needs to make sure all the known bugs and fixes are applied, and unwanted ports and services are disabled.
Which of the following techniques would BEST help the administrator assess these business requirements?
After announcing a big sales promotion, an e-commerce company starts to experience a slow response on its platform that is hosted in a public cloud. When checking the resources involved, the systems administrator sees the following consumption:
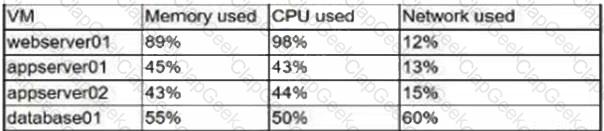
Considering all VMs were built from the same templates, which of the following actions should the administrator perform FIRST to speed up the response of the e-commerce platform?
An organization is running a database application on a SATA disk, and a customer is experiencing slow performance most of the time.
Which of the following should be implemented to improve application performance?
The security team for a large corporation is investigating a data breach. The team members are all trying to do the same tasks but are interfering with each other’s work.
Which of the following did the team MOST likely forget to implement?
An organization that currently stores a set of documents in the cloud is concerned about potential loss if these documents are accidentally deleted. Which of the following is the best way for the organization to quickly recover a lost file?
A systems administrator is trying to connect to a remote KVM host. The command line appears as follows:
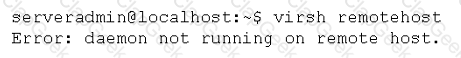
After logging in to the remote server, the administrator verifies the daemon is running. Which of the following should the administrator try NEXT?
A systems administrator has verified that a physical switchport that is connected to a virtualization host is using all available bandwidth. Which of the following would best address this issue?
A cloud administrator recently misconfigured the permission policy on a credential vault by granting public access to it. Which of the following should the administrator do? (Select two).
A new development team requires workstations hosted in a PaaS to develop a new website. Members of the team also require remote access to the workstations using their corporate email addresses. Which of the following solutions will BEST meet these requirements? (Select TWO).
After an infrastructure-as-code cloud migration to an laaS environment, the cloud engineer discovers that configurations on DB servers have drifted from the corporate standard baselines. Which of the following should the cloud engineer do to best ensure configurations are restored to the baselines?
A systems administrator is selecting the appropriate RAID level to support a private cloud with the following requirements:
. The storage array must withstand the failure of up to two drives.
. The storage array must maximize the storage capacity of its drives.
Which of the following RAID levels should the administrator implement?
A systems administrator is performing an OS upgrade on a production VM. Which of the following actions should the administrator take before the upgrade to ensure the FASTEST recovery of the system in case the upgrade fails in an unrecoverable way?
One of the web applications in a public subnet is vulnerable to a newly discovered zero-day vulnerability. Which of the following actions can a security engineer perform to reduce the risk of exploitation and application downtime?
An integration application that communicates between different application and database servers is currently hosted on a physical machine. A P2V migration needs to be done to reduce the hardware footprint. Which of the following should be considered to maintain the same level of network throughput and latency in the virtual server?
A cloud solutions architect needs to determine the best strategy to deploy an application environment in production, given the following requirements:
No downtime
Instant switch to a new version using traffic control for all users
Which of the following deployment strategies would be the BEST solution?
Users are experiencing slow response times from an intranet website that is hosted on a cloud platform. There is a site-to-site VPN connection to the cloud provider over a link of 100Mbps.
Which of the following solutions will resolve the issue the FASTEST?
An administrator recently provisioned a file server in the cloud. Based on financial considerations, the administrator has a limited amount of disk space. Which of the following will help control the amount of space that is being used?
A systems administrator wants to verify the word "qwerty" has not been used as a password on any of the administrative web consoles in a network. Which of the following will achieve this goal?
A company has decided to get multiple compliance and security certifications for its public cloud environment. However, the company has few staff members to handle the extra workload, and it has limited knowledge of the current infrastructure.
Which of the following will help the company meet the compliance requirements as quickly as possible?
A cloud administrator is switching hosting companies and using the same script that was previously used to deploy VMs in the new cloud. The script is returning errors that the command was not found.
Which of the following is the MOST likely cause of the script failure?
A company that utilizes an IaaS service provider has contracted with a vendor to perform a penetration test on its environment. The vendor is able to exploit the virtualization layer and obtain access to other instances within the cloud provider’s environment that do not belong to the company.
Which of the following BEST describes this attack?
A systems administrator is trying to establish an RDP session from a desktop to a server in the cloud. However, the connection appears to be refused even through the VM is responding to ICMP echo requests. Which of the following should the administrator check FIRST?
A cloud administrator needs to reduce the cost of cloud services by using the company's off-peak period. Which of the following would be the BEST way to achieve this with minimal effort?
A SaaS provider wants to maintain maximum availability for its service.
Which of the following should be implemented to attain the maximum SLA?
A company needs to rehost its ERP system to complete a datacenter migration to the public cloud. The company has already migrated other systems and configured VPN connections.
Which of the following MOST likely needs to be analyzed before rehosting the ERP?
Due to a policy change, a few of a customer’s application VMs have been migrated to synchronously replicated storage. The customer now reports that performance is lower. The systems administrator checks the resource usage and discovers CPU utilization is at 60% and available memory is at 30%.
Which of the following is the MOST likely cause?
Company A has acquired Company B and is in the process of integrating their cloud resources. Company B needs access to Company A’s cloud resources while retaining its IAM solution.
Which of the following should be implemented?
A systems administrator is reviewing two CPU models for a cloud deployment. Both CPUs have the same number of cores/threads and run at the same clock speed.
Which of the following will BEST identify the CPU with more computational power?
Which of the following will mitigate the risk of users who have access to an instance modifying the system configurations?
A systems administrator recently deployed a VDI solution in a cloud environment; however, users are now experiencing poor rendering performance when trying to display 3-D content on their virtual desktops, especially at peak times.
Which of the following actions will MOST likely solve this issue?
A systems administrator for an e-commerce company will be migrating the company’s main website to a cloud provider. The principal requirement is that the website must be highly available.
Which of the following will BEST address this requirement?
A DevOps administrator is automating an existing software development workflow. The administrator wants to ensure that prior to any new code going into production, tests confirm the new code does not negatively impact existing automation activities.
Which of the following testing techniques would be BEST to use?
A systems administrator is troubleshooting network throughput issues following a deployment. The network is currently being overwhelmed by the amount of traffic between the database and the web servers in the environment.
Which of the following should the administrator do to resolve this issue?
A systems administrator needs to configure monitoring for a private cloud environment. The administrator has decided to use SNMP for this task.
Which of the following ports should the administrator open on the monitoring server’s firewall?
A systems administrator needs to configure SSO authentication in a hybrid cloud environment.
Which of the following is the BEST technique to use?
An organization requires the following to be achieved between the finance and marketing departments:
Allow HTTPS/HTTP.
Disable FTP and SMB traffic.
Which of the following is the MOST suitable method to meet the requirements?
A SaaS provider wants to maintain maximum availability for its service. Which of the following should be implemented to attain the maximum SLA?
A cloud administrator used a deployment script to recreate a number of servers hosted in a public-cloud provider_ However, after the script completes, the administrator receives the following error when attempting to connect to one of the servers Via SSH from the administrators workstation: CHANGED. Which of the following IS the MOST likely cause of the issue?
A cloud solutions architect has an environment that must only be accessed during work hours. Which of the following processes should be automated to BEST reduce cost?
A company's web servers are scheduled for patching and quarterly updates. A cloud administrator must prevent the monitoring systems from logging outage alerts and negatively impacting company SLA targets. Which of the following is the best action for the administrator to take?
A cloud engineer has container images stored on a local filesystem. The developers would like to make the images available for mass deployment in a secure manner. Which of the following technologies best meets the requirements?
A cloud administrator is choosing a backup schedule for a new application platform that creates many small files. The backup process impacts the performance of the application, and backup times should be minimized during weekdays. Which of the following backup types best meets the weekday requirements?
A systems administrator wants to repurpose and implement a legacy tool that has been used in the past as a multicloud monitoring system. Which of the following will be the most probable challenges in the future caused by this implementation? (Select two).
A corporation is evaluating an offer from a CSP to take advantage of volume discounts on a shared platform. The finance department is concerned about cost allocation transparency, as the current structure splits projects into dedicated billing accounts. Which of the following can be used to address this concern?
A systems administrator is responsible for upgrading operating systems on VMs that are hosted in a cloud environment. The systems administrator wants to ensure the VMs receive updates for as long as possible. Which of the following should the systems administrator choose?
A systems administrator is planning the storage requirements for a two-disk mirror of a server OS disk partition. Which of the following is the amount of disk space available in the mirrored volume?
After a virtualized host is rebooted, ten guest VMs take a long time to start, and extensive memory utilization is observed. Which of the following should be done to optimize the host?
A technician needs to deploy two virtual machines in preparation for the configuration of a financial application next week. Which of the following cloud deployment models should the technician use?
A systems administrator is reviewing the logs from a company's IDS and notices a large amount of outgoing traffic from a particular server. The administrator then runs a scan on the server, which detects malware that cannot be removed. Which of the following should the administrator do first?
A company is preparing a hypervisor environment to implement a database cluster. One of the requirements is to share the disks between the nodes of the cluster to access the same LUN. Which of the following protocols Should the company use? (Select TWO)
A company has a large environment with multiple VPCs across three regions in a public cloud. The company is concerned about connectivity within the regions. Which of the following should the cloud administrator implement?
A web consultancy group currently works in an isolated development environment. The group uses this environment for the creation of the final solution, but also for showcasing it to customers, before commissioning the sites in production. Recently, customers of newly commissioned sites have reported they are not receiving the final product shown by the group, and
the website is performing in unexpected ways. Which of the following additional environments should the group adopt and include in its process?
An organization is managing a cloud environment through a custom portal. The information is used to report daily on cloud consumption. All scheduled tasks run every hour. The issue resets every 24 hours. Given the following log report, which of the following is most likely the cause of the issue?
A systems administrator is troubleshooting issues with audio lag during phone conferences. When looking at the core switch, the administrator notices its buffers are consistently full, and packets are being dropped due to the large number being sent and received. There is no room in the budget for new hardware, but it is critical that the audio lag be fixed immediately. Which of the following will most likely resolve the issue?
A cloud engineer is designing a new cloud environment for an organization that requires resilient connectivity to cloud resources over diverse mediums. Which of the following is the best way to ensure resilient networking?
A company recently acquired another company, and the human resources staff expects to see a 50% increase in usage for the employee benefits web portal once the employees from the acquired company receive access. The cloud administrator needs to assess whether the current web portal can handle the increased load. Which of the following should the cloud administrator do first?
A resource pool in a cloud tenant has 90 GB of memory and 120 cores. The cloud administrator needs to maintain a 30% buffer for resources for optimal performance of the hypervisor. Which of the following would all ow for the maximum number of two-core machines with equal memory?
A company is preparing a hypervisor environment to implement a database cluster. One of the requirements is to share the disks between the nodes of the cluster to access the same LUN. Which of the following protocols should the company use? (Choose two.)
An organization suffered a critical failure of its primary datacenter and made the decision to switch to the DR site. After one week of using the DR site, the primary datacenter is now ready to resume operations.
Which of the following is the MOST efficient way to bring the block storage in the primary datacenter up to date with the DR site?
A cloud administrator created a developer desktop image and added it to the VDI farm in a private cloud environment. One of the developers opened a VDI session and noticed that compiling the code was taking up to one hour to complete. However, when the developer compiles the code on a local machine, the job completes in less than five minutes. Which of the following sizing techniques would be best to use to improve the performance of the compile job?
A systems administrator is creating a VM and wants to ensure disk space is not allocated to the VM until it is needed. Which of the following techniques should the administrator use to ensure?
A systems administrator has received an email from the virtualized environment's alarms indicating the memory was reaching full utilization. When logging in, the administrator notices that one out of a five-host cluster has a utilization of 500GB out of 512GB of RAM. The baseline utilization has been 300GB for that host. Which of the following should the administrator check NEXT?
A systems administrator is working in a globally distributed cloud environment. After a file server VM was moved to another region, all users began reporting slowness when saving files. Which of the following is the FIRST thing the administrator should check while troubleshooting?
A cloud administrator is setting up a new coworker for API access to a public cloud environment. The administrator creates a new user and gives the coworker access to a collection of automation scripts. When the coworker attempts to use a deployment script, a 403 error is returned. Which of the following is the MOST likely cause of the error?
Which of the following service models would be used for a database in the cloud?
A systems administrator has finished installing monthly updates to servers in a cloud environment. The administrator notices certain portions of the playbooks are no longer functioning. Executing the playbook commands manually on a server does not work as well. There are no other reports of issues.
Which of the following is the MOST likely cause of this issue?
To save on licensing costs, the on-premises, IaaS-hosted databases need to be migrated to a public DBaaS solution. Which of the following would be the BEST technique?
Which of the following actions should a systems administrator perform during the containment phase of a security incident in the cloud?
Users of a public website that is hosted on a cloud platform are receiving a message indicating the connection is not secure when landing on the website. The administrator has found that only a single protocol is opened to the service and accessed through the URL https://www.comptiasite.com. Which of the following would MOST likely resolve the issue?
A company is concerned about the security of its data repository that contains customer PII. A systems administrator is asked to deploy a security control that will prevent the exfiltration of such data. Which of the following should the systems administrator implement?
A systems administrator is deploying a VM and would like to minimize storage utilization by ensuring the VM uses only the storage if needs. Which of the following will BEST achieve this goal?
A systems administrator is trying to reduce storage consumption. Which of the following file types would benefit the MOST from compression?
All of a company's servers are currently hosted in one cloud MSP. The company created a new cloud environment with a different MSP. A cloud engineer is now tasked with preparing for server migrations and establishing connectivity between clouds. Which of the following should the engineer perform FIRST?
An administrator has been informed that some requests are taking a longer time to respond than other requests of the same type. The cloud consumer is using multiple network service providers and is performing link load balancing for bandwidth aggregation. Which of the following commands will help the administrator understand the possible latency issues?
A private IaaS administrator is receiving reports that all newly provisioned Linux VMs are running an earlier version of the OS than they should be. The administrator reviews the automation scripts to troubleshoot the issue and determines the scripts ran successfully. Which of the following is the MOST likely cause of the issue?
A cloud security analyst is implementing a vulnerability scan of the web server in the DMZ, which is running in an IaaS compute instance. The default inbound firewall settings are as follows:
Which of the following will provide the analyst with the MOST accurate report?
A cloud administrator is managing an organization's infrastructure in a public cloud. All servers are currently located in a single virtual network with a single firewall that all traffic must pass through. Per security requirements, production, QA, and development servers should not be able to communicate directly with each other. Which of the following should an administrator perform to comply with the security requirement?
A systems administrator is using a configuration management tool to perform maintenance tasks in a system. The tool is leveraging the target system's API to perform these maintenance tasks After a number of features and security updates are applied to the target system, the configuration management tool no longer works as expected. Which of the following is the MOST likely cause of the issue?
A company needs a solution to find content in images. Which of the following technologies, when used in conjunction with cloud services, would facilitate the BEST solution?
A cloud administrator is assigned to establish a connection between the on-premises data center and the new CSP infrastructure. The connection between the two locations must be secure at all times and provide service for all users inside the organization. Low latency is also required to improve performance during data transfer operations. Which of the following would BEST meet these requirements?
A systems administrator is analyzing a report of slow performance in a cloud application. This application is working behind a network load balancer with two VMs, and each VM has its own digital certificate configured. Currently, each VM is consuming 85% CPU on average. Due to cost restrictions, the administrator cannot scale vertically or horizontally in the environment. Which of the following actions should the administrator take to decrease the CPU utilization? (Choose two.)
An organization is using multiple SaaS-based business applications, and the systems administrator is unable to monitor and control the use of these subscriptions. The administrator needs to implement a solution that will help the organization apply security policies and monitor each individual SaaS subscription. Which of the following should be deployed to achieve these requirements?
A cloud administrator has deployed a new VM. The VM cannot access the Internet or the VMs on any other subnet. The administrator runs a network command and sees the following output:
The new VM can access another VM at 172.16.31.39. The administrator has verified the IP address is correct. Which of the following is the MOST likely cause of the connectivity issue?
A media company has made the decision to migrate a physical, internal file server to the cloud and use a web- based interface to access and manage the files. The users must be able to use their current corporate logins.
Which of the following is the MOST efficient way to achieve this goal?
A security team is conducting an audit of the security group configurations for the Linux servers that are hosted in a public laaS. The team identifies the following rule as a potential
A cloud administrator, who is working remotely, logs in to the cloud management console and modifies the rule to set the source to "My IR" Shortly after deploying the rule, an internal developer receives the following error message when attempting to log in to the server using SSH: Network error: connection timed out. However, the administrator is able to connect successfully to the same server using SSH. Which of the following is the BEST option for both the developer and the administrator to access the
server from their locations?
A company has two identical environments (X and Y) running its core business application. As part of an upgrade, the X environment is patched/upgraded and tested while the Y environment is still serving the consumer workloads. Upon successful testing of the X environment, all workload is sent to this environment, and the Y environment is then upgraded before both environments start to manage the workloads. Which of the following upgrade methods is being used?
A systems administrator is responding to an outage in a cloud environment that was caused by a network-based flooding attack. Which of the following should the administrator configure to mitigate the attack?
A cloud administrator needs to coordinate and automate the management of a company's secrets and keys for all its cloud services with minimal effort and low cost. Which of the following is the BEST option to achieve the goal?
A DevOps administrator is building a new application slack in a private cloud. This application will store sensitive information and be accessible from the internet. Which of the following would be MOST useful in maintaining confidentiality?
A cloud administrator would like to maintain file integrity checks through hashing on a cloud object store. Which of the following is MOST suitable from a performance perspective?
A cloud administrator has deployed several VM instances that are running the same applications on VDI nodes. Users are reporting that a role instance is looping between STARTED, INITIALIZING, BUSY, and stop. Upon investigation, the cloud administrator can see the status changing every few minutes. Which of the following should be done to resolve the issue?
A cloud architect is deploying a web application that contains many large images and will be accessed on two continents. Which of the following will MOST improve the user experience while keeping costs low?
A systems administrator is asked to implement a new three-host cluster. The cloud architect specifies this should be a testing environment, and the budget is limited. The estimated resource consumption for each application is as follows:
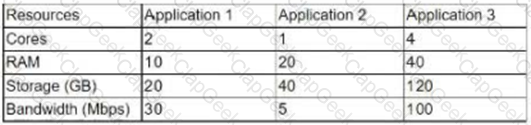
A company is performing a DR drill and is looking to validate its documentation. Which of the following metrics will determine the service recovery duration?
In an IaaS platform, which of the following actions would a systems administrator take FIRST to identify the scope of an incident?
Users currently access SaaS email with five-character passwords that use only letters and numbers. An administrator needs to make access more secure without changing the password policy. Which of the following will provide a more secure way of accessing email at the lowest cost?
A systems administrator is working on the backup schedule for a critical business application that is running in a private cloud. Which of the following would help the administrator schedule the frequency of the backup job?
A systems administrator needs to migrate email services to the cloud model that requires the least amount of administrative effort. Which of the following should the administrator select?
A production engineer is configuring a new application, which is running in containers, that requires access to a database. Which of the following methods will allow the application to authenticate to the database in the MOST secure way?
A cloud administrator is troubleshooting a highly available web application running within three containers behind a Layer 7 load balancer with a WAF inspecting all traffic. The application frequently asks the users to log in again even when the session timeout has not been reached. Which of the following should the cloud administrator configure to solve this issue?
A systems administrator is setting up a backup solution to follow the 3-2-1 policy. Currently, the solution is set to back up from the servers to an on-site storage server. Which of the following should the administrator configure to comply with the 3-2-1 policy?
A company is migrating workloads from on premises to the cloud and would like to establish a connection between the entire data center and the cloud environment. Which of the following VPN configurations would accomplish this task?
An administrator manages a file server that has a lot of users accessing and creating many files. As a result, the storage consumption is growing quickly. Which of the following would BEST control storage usage?
A technician deployed a VM with NL-SAS storage to host a critical application. Two weeks later, users have begun to report high application latency. Which of the following is the BEST action to correct the latency issue?
A cloud engineer, who manages workloads in a public cloud environment, uses autoscaling to maintain availability of a critical application. During a recent burst in demands, the engineer received the following error alert:
LimitedlnstanceCapacity
Which of the following is MOST likely cause of the error?
A systems administrator is securing a new email system for a large corporation. The administrator wants to ensure private corporate information is not emailed to external users. Which of the following would be MOST useful to accomplish this task?
A web application has been configured to use autoscaling for provisioning and deprovisioning more VMs according to the workload. The systems administrator deployed a new CI/CD tool to automate new releases of the web application. During the night, a script was deployed and configured to be executed by the VMs during bootstrapping. Now. the autoscaling configuration is creating a new VM ever\ five minutes. Which of the following actions will MOS I like y resolve the issue?
A company has two primary offices, one in the United States and one in Europe. The company uses a public laaS service that has a global data center presence to host its marketing materials. The marketing team, which is primarily based in Europe, has reported latency issues when retrieving these materials. Which of the following is the BEST option to reduce the latency issues?
A systems administrator needs to deploy a solution to automate new application releases that come from the development team. The administrator is responsible for provisioning resources at the infrastructure layer without modifying any configurations in the application code. Which of the following would BEST accomplish this task?
A systems administrator is deploying a new virtualized environment. The setup is a three-server cluster with 12 VMs running on each server. While executing a vertical-scaling test of the vCPU on the VMs, the administrator gets an error. Which of the following issues is MOST likely occurring?
An organization is hosting its dedicated email infrastructure with unlimited mailbox creation capability. The management team would like to migrate to a SaaS-based solution. Which of the following must be considered before the migration?
A company is deploying a public cloud solution for an existing application using lift and shift. The requirements for the applications are scalability and external access. Which of the following should the company implement? (Select TWO).
An organization has a public-facing API that is hosted on a cloud provider. The API performs slowly at times. Which of the following technologies should the cloud administrator apply to provide speed acceleration and a secure connection?
A piece of software applies licensing fees on a socket-based model. Which of the following is the MOST important consideration when attempting to calculate the licensing costs for this software?
An organization recently deployed a private cloud on a cluster of systems that delivers compute, network, and storage resources in a single hardware, managed by an intelligent software. Which of the following BEST describes this type of deployment?
A cloud administrator needs to control the connections between a group of web servers and database servers as part of the financial application security review. Which of the following would be the BEST way to achieve this objective?
A systems administrator is planning a penetration test for company resources that are hosted in a public cloud. Which of the following must the systems administrator do FIRST?


