Refer to the Exhibit:
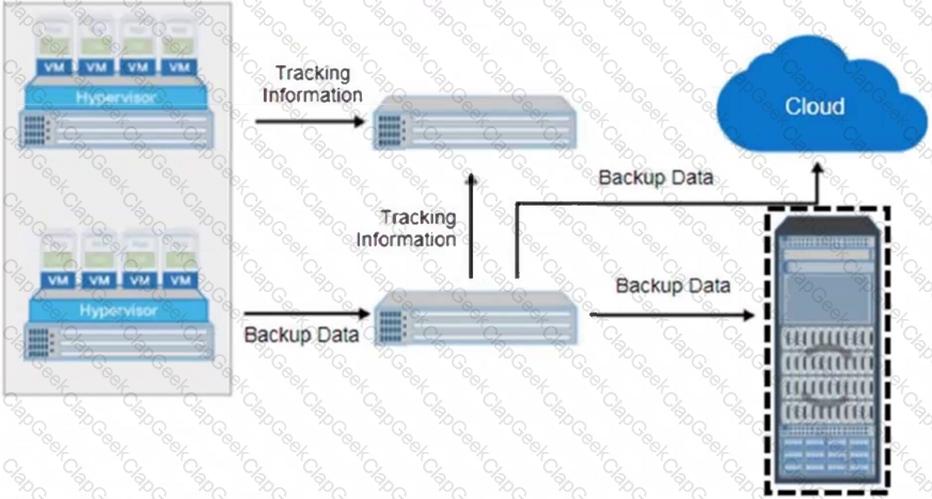
What is the name of the selected backup architecture component?
Which data protection solution provides the ability to select a backup technology based on demand?
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
An Ethernet switch has eight ports and all ports must be operational for 24 hours from Monday through Friday. However, failures of Port 6 occur within the week as follows:
Tuesday = 6 AM to 8 AM
Thursday = 5 PM to 10 PM
Friday = 7 AM to 9 AM
What is the MTBF of Port 6?
Which product enables employees to enroll their mobile devices in an enterprise environment and ensures secure access from the devices to the enterprise resources?
How should vulnerabilities be managed in a data center environment? (Verify the Correct answer from Associate - Information Storage and Management Study Manual from dellemc.com)
An organization is planning to adopt pre integrated systems to deploy compute, network, storage, and management functions as a single engineered solution.
Which approach should the organization adopt?
Which uses an orchestrated approval process to assist decision making using an agile methodology?
What is a key function of the orchestration layer in a modern data center architecture?
Which plane of the SDDC architecture provides a CLI and GUI for IT to administrator the infrastructure and to configure policies? (Choose Correct Answer from Associate - Information Storage and Management version 5 Manual from dellemc.com and give explanation)
Which interface does an SCM device use to connect to intelligent storage system controllers?
Which type of machine learning algorithm produces results using a reward and feedback mechanism?
What is a benefit of including a Defense-in-depth strategy as part of the data center security strategy?
Which backup component sends metadata and tracking information about each backup to the system that maintains this information?
Refer to the Exhibit:
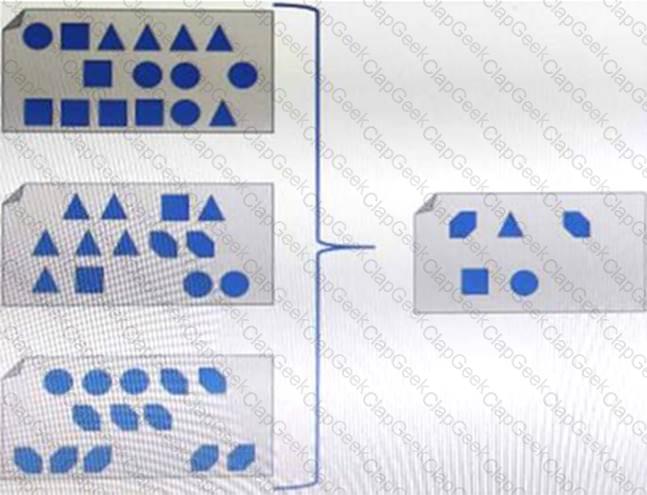
What type of process, when performed on data, would produce the result shown?
In a modern data center environment, which mechanism secures internal assets while allowing Internet-based access to selected resources?
Refer to the Exhibit:
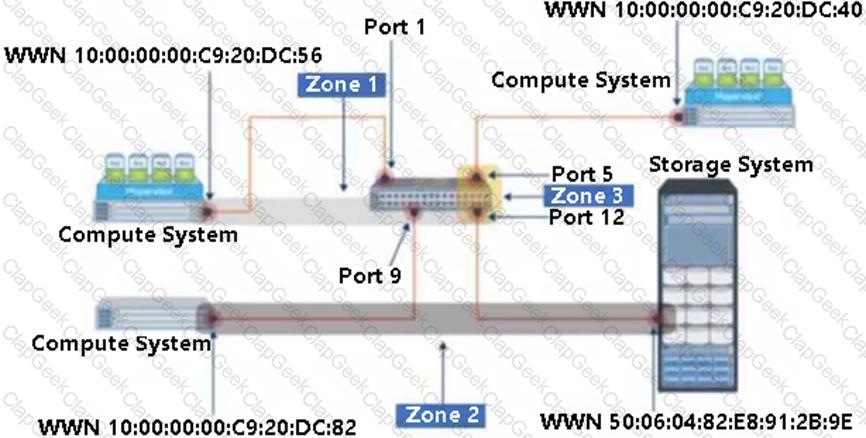
Select the option that represents the three Zone Types for each of the labeled zones.
An organization has two data centers separated by a distance of 1600 km. They want to replicate between these data centers for disaster recovery purposes. They are concerned that this will impact application response time.
Which solution will address this concern?
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
Monday = 10 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 PM to 7 PM
Friday = 3 PM to 6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?
Refer to the Exhibit:
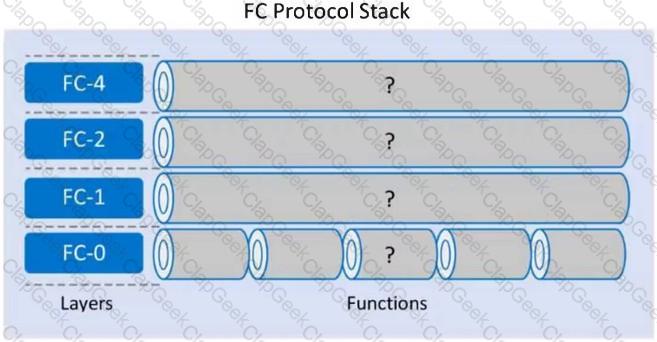
Which functions align with each layer of the FC Protocol Stack using the following order: FC-4, FC-2, FC-1, and FC-0?
An organization wants to replicate their data by extending the local network across a public network. Prior to implementing replication, they need to secure the network.
Which security control mechanism is recommended?
What functionality does the control layer provide in a software-defined networking architecture?
What is a benefit of using an existing Ethernet network infrastructure for storage connectivity?
Which layer of the OSI reference model is responsible for logical addressing and routing?
Which security mechanism ensures secure access to internal assets while enabling Internet-based access to selected resources?
An Ethernet switch has eight ports and all ports must be operational for 24 hours from Monday through Friday.
However, a failure of Port 7 occurs as follows:
● Monday=4 PM to 11 PM
● Wednesday= 2 PM to 10 PM
● Friday= 5 AM to11 AM
What is the MTTR of Port 7?
What triggers an appropriate workflow upon receiving a service provisioning or management request?
A Fibre Channel switch has eight ports and all ports must be operational from 6 AM to 6 PM, Monday through Friday.
However, a failure of Port 4 occurs with the week as follows:
Monday= 11 AM to 1 PM
Wednesday= 5 PM to 10 PM
Thursday= 7 AM to 10 AM
Saturday= 11 AM to 1 PM
What is the availability of Port 4 in that week?
Which method automatically allocates a large capacity secondary cache using SSD and SCM?
In a NAS environment, which file system enables file sharing with Windows clients and uses the TCP/IP protocol?
Which technology allows automation of sensors and devices to share and process information?
Which VM file is used to keep a record of the VM's activity and is often used for troubleshooting?
What is the total usable data storage capacity in this scenario:
a RAID 6 array with four 250 GB disks
In a data archiving environment, which component scans primary storage to find the files that are required to archive?
Why is it important for organizations to implement a multi-site remote replication solution?


