A technician has verified full system functionality. Which of the following actions should the technician take next?
A systems administrator uses a program that interacts directly with hardware to manage storage, network, and virtual machines. This program is an example of:
Which of the following is MOST likely used to represent international text data?
A programmer creates an object to retrieve customer names from a database. Which of the following best describes the object that is retrieving the names?
Given the following pseudocode:
If the Breakfast program ran on Sunday, which of the following would be the output?
A network administrator wants to keep track of all system messages and alerts. Which of the following would best allow for the administrator to follow trends?
A company will begin to allow staff to work from home by means of formal request. Which of the following is the BEST way for the company to document this change?
A database administrator wants to populate a database with large amounts of data from an external source.
Which of the following actions should be used to get the database populated?
During a meeting, managers spoke of several instances in which confidential information appeared on inappropriate websites. The company also discovered its firewall did not filter out certain traffic to prevent such issues. Which of the following most likely exposed the confidential information?
A music studio needs to store artist data as text, demos as MP3 files, and sheet music as PDF files in an organized and easily searchable format. Which of the following is best suited to meet this need?
For which of the following is a relational database management system MOST commonly used?
Meaningful and accurate reporting is essential to retailers in making business decisions while managing
inventory. Which of the following offers the BEST assistance in generating reports?
A systems administrator wants to run a script at a certain time every day. Which of the following is the BEST
way to achieve this?
A technician is installing a new wireless network and wants to secure the wireless network to prevent
unauthorized access. Which of the following protocols would be the MOST secure?
A help desk technician encounters an issue and wants to find out if a colleague has encountered the same issue before. Which of the following should the technician do FIRST?
Which of the following is most likely managed directly by the operating system?
Which of the following would be the easiest component to upgrade on a laptop that is experiencing slow performance?
Which of the following database types would be best in which to place financial data?
A user clicks a link to a web page to view a document, but nothing happens. Which of the following is most likely the issue?
Which of the following internal computing components is typically tasked with handling complex mathematical calculations required for realistic in-game physics?
Which of the following is most appropriate to list on a social media site about an employer?
A technician is troubleshooting a problem. The technician tests the theory and determines the theory is
confirmed. Which of the following should be the technician’s NEXT step?
A remote user, who is working from home, requires significant bandwidth to connect to the corporate systems.
Which of the following types of Internet service connections would BEST meet the user’s needs?
A network technician is working on the configuration of a SOHO router. After entering the IP address of the router, the technician uses a GUI to complete the final configuration steps. Which of the following configuration types is this an example of?
A user installs a wireless router and opens a browser to modify the settings. Which of the following installation types does this describe?
After creating a database, which of the following would a developer most likely use to put data in the database?
Ann, a user, connects to the corporate WiFi and tries to browse the Internet. Ann finds that she can only get to local (intranet) pages. Which of the following actions would MOST likely fix the problem?
Which of the following interfaces is best for viewing database performance information?
Which of the following is the BEST option for a developer to use when storing the months of a year and when
performance is a key consideration?
Which of the following license types would be most cost effective for an organization if all users need to access software but not on a consistent basis?
Which of the following BEST explains the use of float over integer to store monetary values?
In an effort to reduce costs, a company decides not to renew its contract for a secure shredding service. Which of the following risks should the management team most likely be concerned with if employees fail to properly dispose of documents according to security protocols?
Which of the following allows wireless devices to communicate to a wired network?
Which of the following would be best to use to store a project task list that will be updated by multiple team members?
A Chief Executive Officer (CEO) wants to have the ability to log on to all applications upon arrival at the office. The CEO would like to have the ability to provide credentials only once. Which of the following is best for this requirement?
A product advertising kiosk at a mall is set up using a thin client without a hard drive and is running a web application managed and updated through an internet connection. Which of the following application delivery methods is most likely being used for the kiosk?
Which of the following availability concerns is mitigated by having a business continuity site?
Which of the following filesystems is most commonly found on a computer running macOS?
A systems administrator wants to return results for a time range within a database. Which of the following
commands should the administrator use?
A user has an HDD that is almost at full capacity. Which of the following operating system features should be used to free up some space without deleting any files?
A business would like to create an employee portal that employees will have access to when they are at work.
The employees will not be able to connect to the portal from home without a VPN connection. Which of the
following types of application does this describe?
Which of the following scripting languages is most likely to be used in a Linux command-line environment?
An application is hosted on a local network. Which of the following descriptions is correct?
Which of the following business continuity concepts is the best example of fault tolerance?
A user wants to use a laptop outside the house and still remain connected to the Internet. Which of the
following would be the BEST choice to accomplish this task?
Which of the following filesystems is compatible with the greatest number of operating systems?
Which of the following BEST describes the physical location of the data in the database?
A developer is writing a program to process a long list of employees and apply a cost-of-living increase of 3.2% to all employees making less than $15 per hour. Which of the following pseudocode snippets provides the best solution?
Which of the following operating systems is best used in creating and managing virtual machines?
Joe, a user, finds out his password for a social media site has been compromised. Joe tells a friend that his email and banking accounts are probably also compromised. Which of the following has Joe MOST likely performed?
Which of the following is a quality of solutions created by web browsers?
A Proprietary
B. Cross-platform
C. Single platform
D. Site licensed
When editing a document, which of the following describes where the changes are located before they are saved to permanent storage?
A user opens an application that is installed locally on a PC. The application connects directly to a database that is located on a server in a data closet in the same building. Which of the following application architecture models does this describe?
A user wants to ensure port 3389 is open for remote desktop on a PC. Which of the following describes where the user should verify the port is open?
A user works at a health insurance company. Which of the following is the best method for ensuring a customer's personal information is kept confidential when it needs to be shared with another authorized employee?
A regulation requires new applicants to provide a scan of their retinas in case of any future legal questions regarding who applied for the position. Which of the following concepts is this an example of?
Which of the following tasks is typically performed during the identification phase of the troubleshooting
methodology?
Which of the following shows how many results are possible when evaluating Boolean data types?
Which of the following describes something in a database that refers to the unique identifier in the parent
table?
The IT department has established a new password policy for employees. Specifically, the policy reads:
Passwords must not contain common dictionary words
Passwords must contain at least one special character.
Passwords must be different from the las six passwords used.
Passwords must use at least one capital letter or number.
Which of the following practices are being employed? (Select TWO).
Which of the following allows network traffic to pass through it and filters specific packets?
Which of the following are the primary functions of an operating system? (Choose two.)
On which of the following distinct numbers of digits is the hexadecimal numbering system based?
Which of the following is the least expensive way for users at a large company to load a 2GB spreadsheet quickly?
A gaming console needs to allow for inbound connectivity on a home network to facilitate chat functions. Which
of the following devices is a user MOST likely to configure to allow this?
Given the following pseudocode:
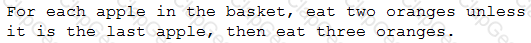
If there are seven apples in the basket, which of the following would be the number of oranges a person eats?
Which of the following connection types is typically used for a display monitor?
A technician needs to install and configure a wireless SOHO network. Which of the following should the technician configure to reduce Wi-Fi interference from other household appliances?
Which of the following data types should a database administrator use to store customer postal codes?
A customer is looking for a device that uses tap to pay when making purchases. Which of the following technologies should the customer use?
A user inserts a USB flash drive into a computer tor the first time and sees a message on the screen indicating the device is being set up. The message quickly changes to indicate the device is ready for use. Which of the following device configuration types most likely occurred?
A technician replaces the video card in a user’s PC. The user reports the resolution on the display seems very low, but the operating system will not let the user adjust it any higher. Which of the following steps would MOST likely fix this problem?
An executive is sharing a series of slides with coworkers in a conference room. Which of the following applications is the executive most likely to use?
Which of the following describes the ability to recover access to a specific account if a credential is forgotten?
Employees of a large technology company are provided access to the internet as a work resource. Which of the following most likely represents the level of privacy employees should expect when utilizing this resource?
A user needs to enter text and numbers to produce charts that demonstrate sales figures. Which of the
following types of software would BEST complete this task?
A technician is called to replace a display for a workstation. Which of the following would MOST likely be used to connect the display to the workstation?
Which of the following would MOST likely prevent malware sent as compromised file via email from infecting a person’s computer?


