Refer to the exhibit.
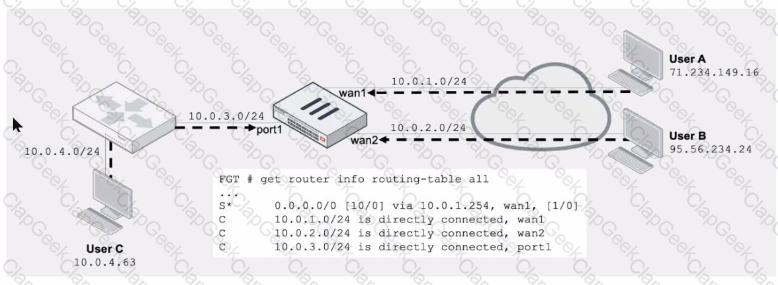
Assuming a default configuration, which three statements are true? (Choose three.)
Exhibit.
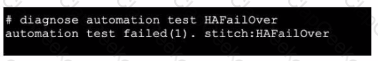
Refer to the exhibit, which shows the output of diagnose automation test.
What can you observe from the output? (Choose two.)
Exhibit.
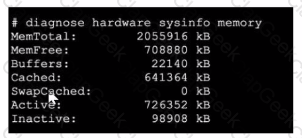
Refer to the exhibit, which shows a partial output of diagnose hardware aysinfo memory.
Which two statements about the output are true? (Choose two.)
Refer to the exhibits.
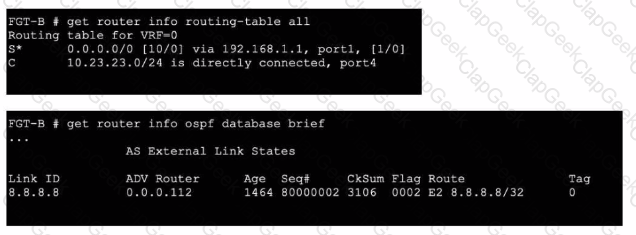
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?
Exhibit.
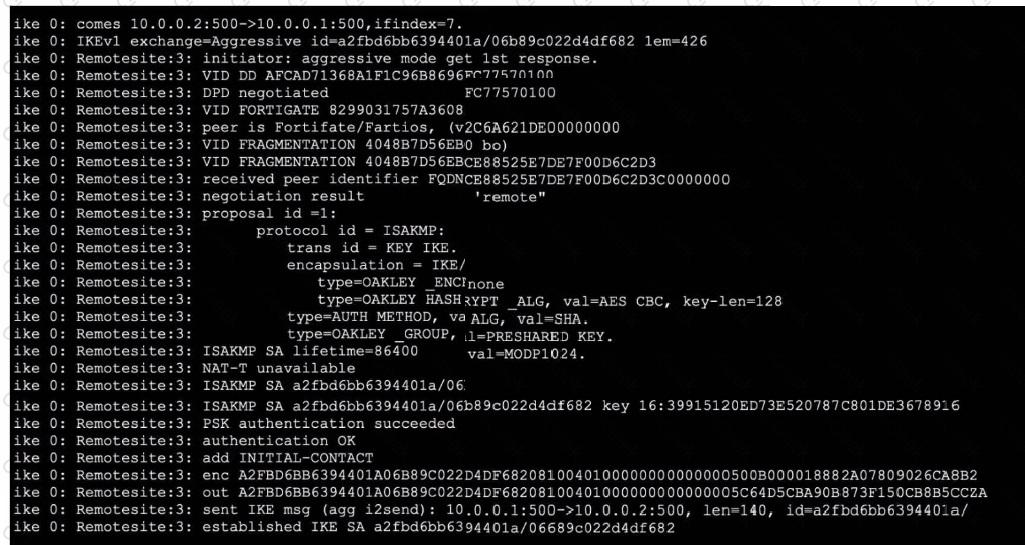
Refer to the exhibit, which contains partial output from an IKE real-time debug.
Which two statements about this debug output are correct? (Choose two.)
Exhibit.
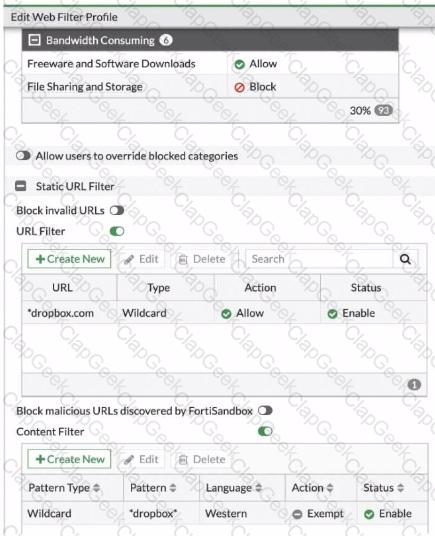
Refer to the exhibit, which shows a partial web fillet profile configuration.
Which action does FortiGate lake if a user attempts to access www. dropbox. com, which is categorized as File Sharing and Storage?


