Refer to the exhibits.
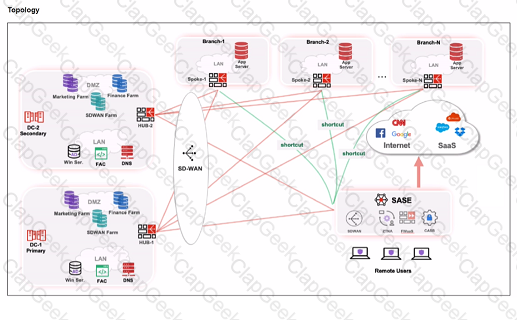
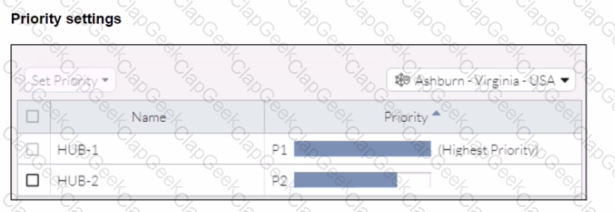
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
Which two statements describe a zero trust network access (ZTNA) private access use case? (Choose two.)
When viewing the daily summary report generated by FortiSASE, the administrator notices that the report contains very little data.
What is a possible explanation for this almost empty report?
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system.
What is the recommended way to provide internet access to the contractor?
In which three ways does FortiSASE help organizations ensure secure access for remote workers? (Choose three.)


