Trojan horses may disclose sensitive information of victims or even remotely manipulate victims' hosts, causing serious harm. Which of the following are the transmission modes of Trojan horses?(Select All that Apply)
During deployment of Portal authentication, an authentication-free rule profile needs to be configured to ensure Portal pages can be opened on authentication terminals. To achieve this purpose, the following traffic needs to be permitted in the authentication-free rule profile: DNS resolution traffic of user terminals, traffic from user terminals for accessing Portal pages, and traffic from user terminals to the RADIUS server.
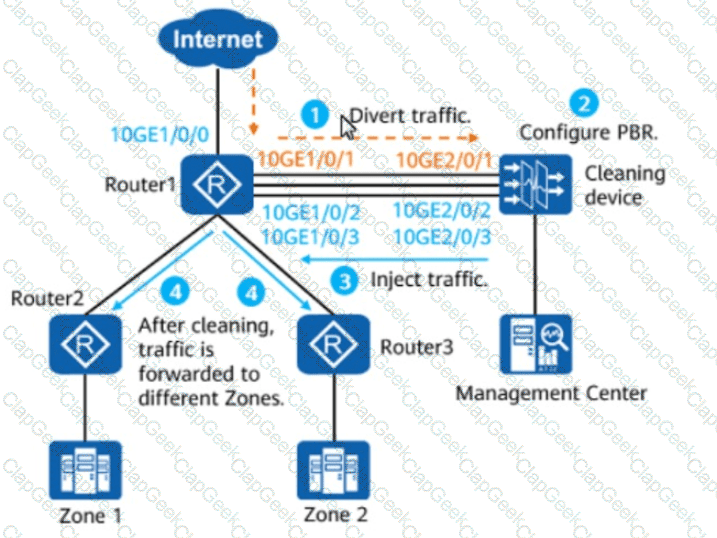
The figure shows the PBR-based injection scenario. Which of the following statements are true about this scenario?(Select All that Apply)
Which of the following statements is true about the outgoing traffic in the firewall virtual system?
Which of the following statements are true about SYN scanning attacks?(Select All that Apply)
iMaster NCE-Campus has a built-in LDAP module that enables it to function as an LDAP server to interconnect with access devices through LDAP.
If data filtering is configured on the firewall but is not correctly referenced in the security policy, the data that should be blocked can still be transmitted normally.
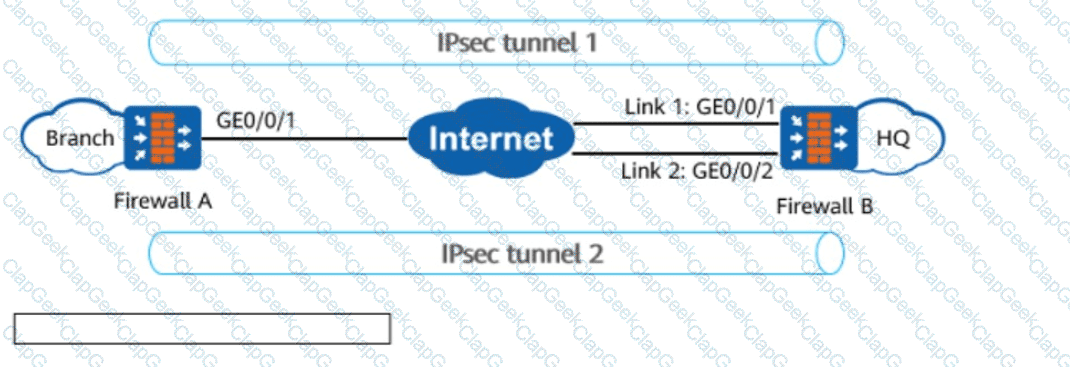
In the figure, enterprise A and enterprise B need to communicate securely, and an IPsec tunnel is established between firewall A and firewall B. Which of the following security protocols and encapsulation modes can meet the requirements of this scenario?
Authentication rules configured on iMaster NCE-Campus support multiple matching conditions, such as matching account information, SSID information, and terminal IP address ranges, so that different authentication rules can be executed for different users.
In the figure, FW_A connects to FW_B through two links working in active/standby mode. When the active link of FW_A is faulty, the old IPsec tunnel 1 needs to be torn down, and IPsec tunnel 2 needs to be established with FW_B through the standby link to route traffic. In this case, configuring the IKE _____ detection mechanism on FW_A helps detect link faults and tear down the IPsec tunnel.(Enter lowercase letters.)
Which of the following statements is false about Eth-Trunk?(Select All that Apply)
Huawei iMaster NCE-Campus is a web-based centralized management and control system in the CloudCampus Solution. It supports user access management and can function as multiple types of authentication servers. Which of the following servers can iMaster NCE-Campus not be used as?
Which of the following statements is false about virtual system resource allocation?
SYN scanning requires a fully established TCP connection and is recorded in system logs.