OSPF neighbors have multiple states, such as Down, Init, 2-way, Loading, or Full. In which of the following states do OSPF routers negotiate the master and slave roles?
The IP prefix list configuration on a Huawei router is shown below. Which of the following routes can match this IP prefix list?
bash
Copy
[huawei] ip ip-prefix test index 10 permit 10.0.0.0 8 less-equal 32
L2TP does not provide security encryption. Therefore, other security measures, such as IPsec, are required to ensure the security of the entire tunnel for data transmission.
IP multicast effectively conserves network bandwidth and reduces network load. Therefore, it is widely used in network services, such as IPTV, real-time data transmission, and multimedia conferencing.
In IPv6, to communicate with a destination host, a host must obtain the link-layer address of the destination host through ARP.
A router performs a lookup in its FIB table for a packet. If the tunnel ID in the matching entry is 0, the packet needs to be forwarded through a tunnel, such as an MPLS tunnel.
A company has a stack consisting of three switches that are running properly. The master switch restarts due to a fault. Given this, which of the following statements are true?
An IP prefix list is configured on a router using the following command:
ip ip-prefix huawei index 10 permit 10.1.1.0 24 greater-equal 26
In this case, the value of greater-equal-value is ____, and the value of less-equal-value is ____.
On an OSPF network, all OSPF routers generate Router LSAs. If the E bit in a Router LSA is set to 1, the router that generates this LSA is a/an ______.
As shown in the figure, SWA, SWB, and SWC run the Rapid Spanning Tree Protocol (RSTP). What are the roles of SWB's GE0/0/2 and SWC's GE0/0/1?
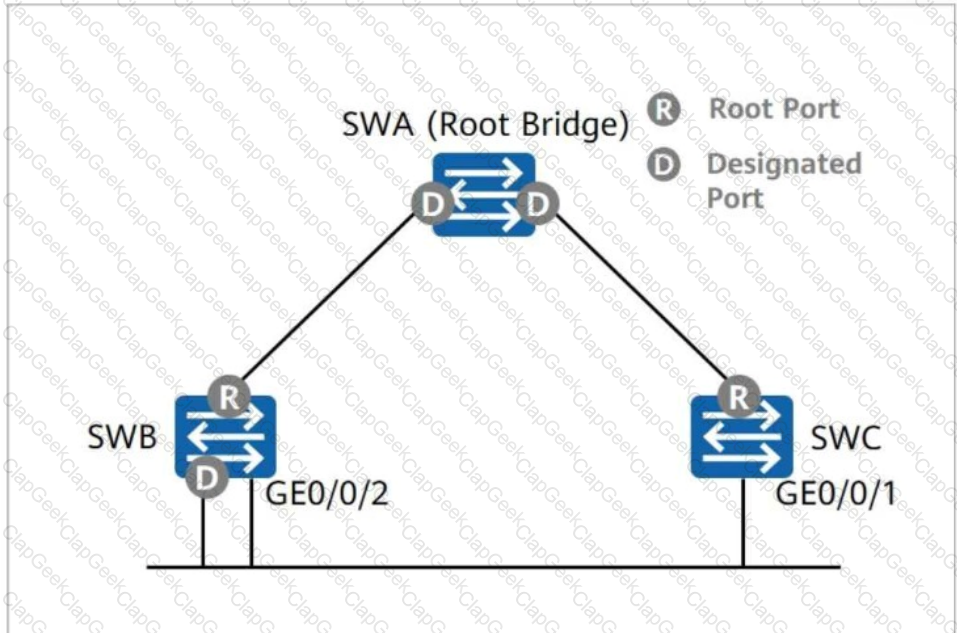
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
On a network, each router has a local core routing table and protocol routing tables. A routing entry in the local core routing table has multiple key fields. Which of the following are included?
VRF, also called VPN instance, is a network virtualization technology that helps VPN technology to isolate users. In normal cases, multiple VPN instances can be created on a physical device, and each VPN instance has independent entries. Which of the following resources can be independently owned by a VPN instance?
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
Both MQC and PBR can be applied on device interfaces to filter received and sent packets or control packet forwarding paths.
ASPF enables the firewall to support multi-channel protocols such as FTP and to define security policies for complex applications.
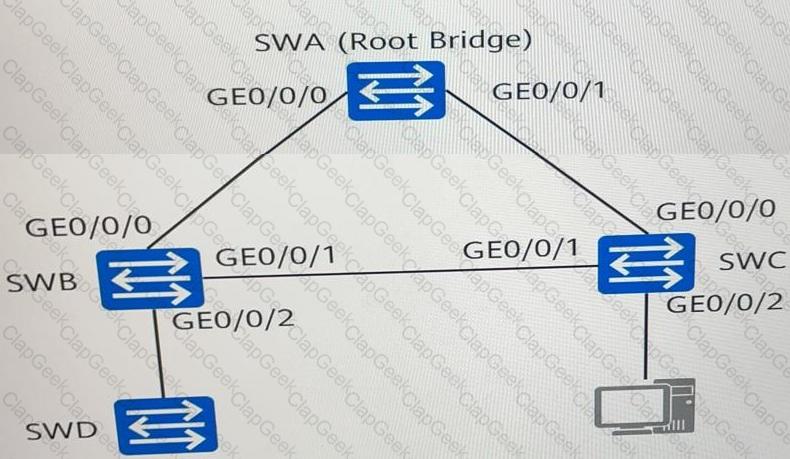
As shown in the figure, SWA, SWB, SWC, and SWD run the Rapid Spanning Tree Protocol (RSTP). Which of the following statements are true?
An enterprise office network runs OSPF and is divided into multiple OSPF areas. Enterprise network engineers can configure route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
On an IS-IS network, each device needs to be configured with a network entity title (NET), which consists of three parts, each containing different fields. Which of the following fields are contained in the Area Address part?
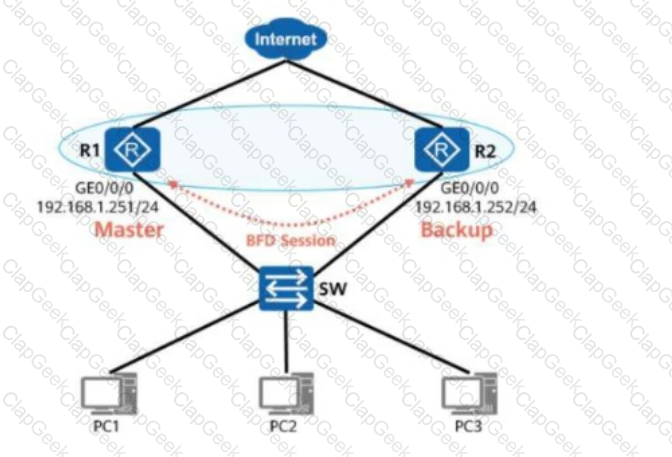
As shown in the figure, VRRP is associated with a BFD session. When a backup device detects a fault through BFD, the backup device immediately assumes the master role after the Master_Down_Timer timer expires.
Which of the following statements regarding the firewall zone security level is false?
IGMP group entries play an important role in multicast forwarding. An administrator runs a command to view information about a multicast entry. The information is as follows:
sql
Copy
Interface group report information
Vlanif100(10.1.6.2):
Total 1 IGMP Group reported
Group Address Last Reporter Uptime Expires
225.1.1.2 10.1.6.10 00:02:04 00:01:17
Given this, which of the following statements are true?
An ACL can be used to match routes or data, but cannot be used to match both the IP address prefix length and mask length.
IGMPV3 not only supports IGMPv1 General Query and IGMPv2 Group-Specific Query, and also IGMPv3 Source/Group-Specific Query.
On an OSPF network, LSDBs are used to store LSAs. Common LSAs include router LSAs and network LSAs. Which of the following items is not included in the 3-tuple that is used to uniquely identify an LSA?
On an OSPF network, interfaces are classified into four types based on link layer protocols. Which of the following types can interfaces on an IS-IS network be classified into based on physical links?
BGP is generally applied to complex networks where routes change frequently. Frequent route flapping consumes a large number of bandwidth and CPU resources, and even affects the normal operation of the network. This is an unavoidable problem that cannot be solved in BGP.
In BGP, the origin attribute of the routes imported using the import-route command is incomplete.
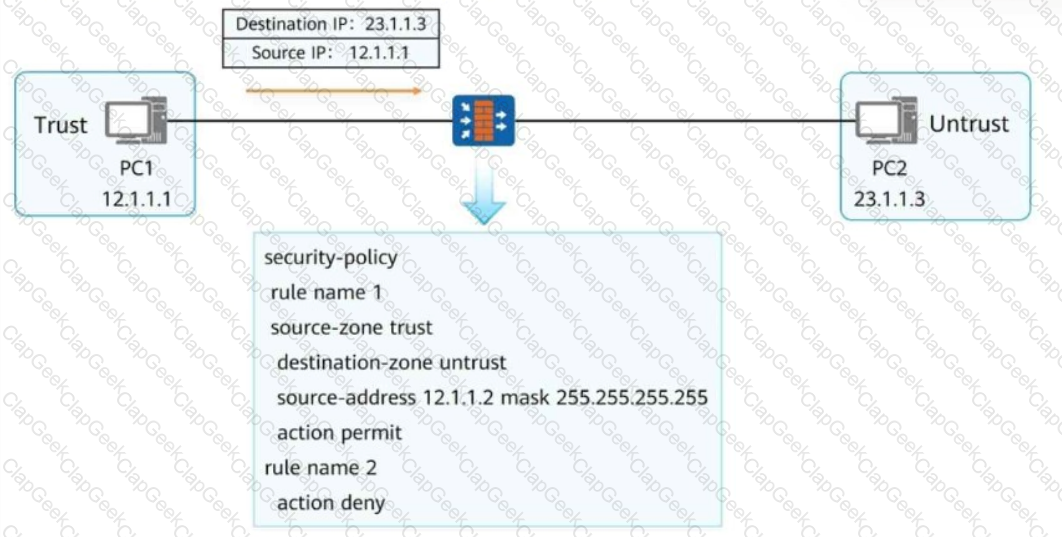
A firewall receives a packet that PC1 sends to PC2. Which of the following statements are true?
STAs stay on different subnets before and after Layer 3 roaming. To enable the STAs to access the original network after roaming, network engineers need to configure user traffic to be forwarded to the original subnet over a CAPWAP tunnel.
A Huawei firewall by default creates security zones named untrust, dmz, _________ and local. (Use Lowercase letters.)
Route summarization is a mechanism that combines multiple routes. BGP supports automatic summarization and manual summarization on IPv6 networks.
In the SNMP management model, which of the following elements defines the attributes of a managed device?
Which of the following statements regarding OSPF route summarization commands are true?
On a broadcast IS-IS network shown in the following figure, a DIS needs to be elected to create and update pseudonodes. Which of the following routers is elected as the DIS?
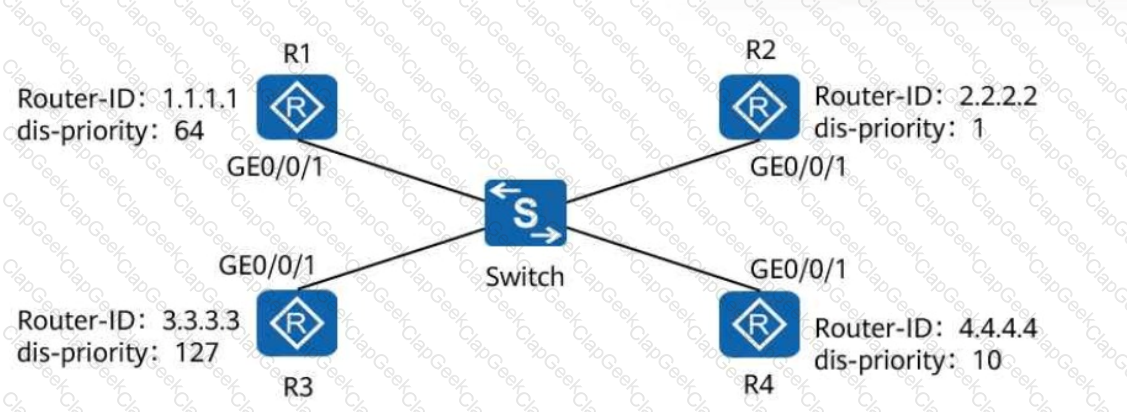
If a router ID is configured in both the system via and the BGP view, BGP uses the router ID configured in the BGP view because the BGP view takes precedence over the system view.
BGP can select routes based on the AS_Path attribute. Therefore, in some cases, a route-policy needs to be used to modify the AS_Path attribute for route selection. Which of the following parameters can be specified in the apply as-path command for a route-policy to modify this attribute?
ACLs are a common matching tool in routing policies. An ACL can be configured on a router to match routes.
To enable PC1 to access PC2 using the IP address of the firewall's GE0/0/2, you need to configure NAPT for source address translation. In the following figure, fill in the blank to complete the command. 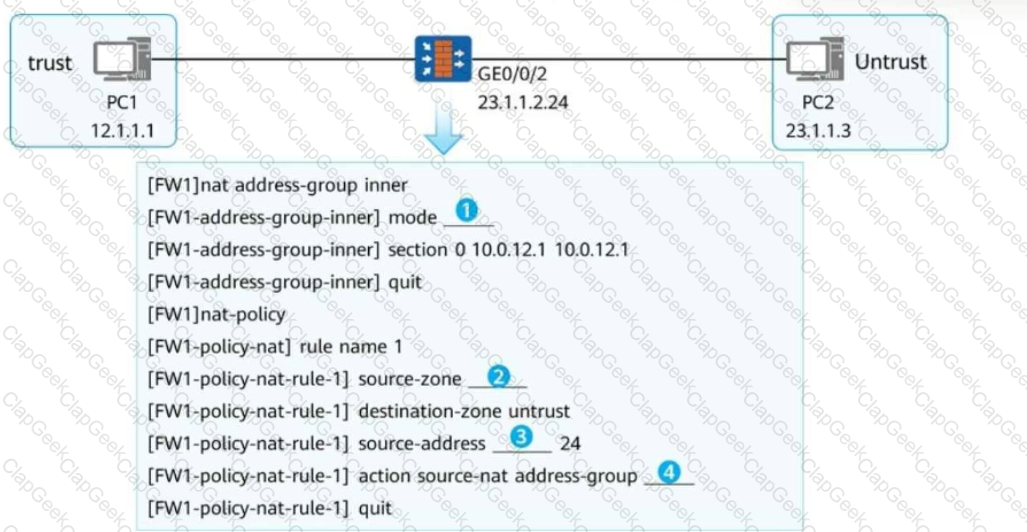
On an OSPF network, routers learn routing information on the entire network by exchanging LSAs. Which of the following values is the LS Age in the LSA header when an LSA is deleted?
On an OSPF network, if a router receives an update of an LSA that exists in the local LSDB, the router updates the LSDB and floods the LSA.
A filter named si is configured on a device using the as-path-filter command and is applied to a specified BGP peer. The detailed configurations are as follows:
csharp
Copy
[SW1] ip as-path-filter si permit _65500$
[SW1] bgp 65100
[SW1-bgp] ipv4-family unicast
[SW1-bgp-af-ipv4] peer 10.1.1.2 as-path-filter si import
After the configuration is complete, which of the following statements is true about the way the local device processes the routes received from the peer?
Which of the following is the default interval at which the DIS on a broadcast IS_IS network sends CSNPs.
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
As a next-generation wireless technology, Wi-Fi 6 greatly improves bandwidth rate and performance. Which of the following statements is false about the features of Wi-Fi 6?
BFD provides fast fault detection independent of media and routing protocols. To use this mechanism to detect link connectivity, devices at both ends must support this feature.
On an STP network, the root bridge, root port, and designated port are elected in sequence. The election rules of these ports are different. List the steps for electing the root port in sequence.
During routine O&M, the administrator checks the IGMP configuration on a router interface. The configuration is as follows:
Interface information of VPN-Instance: public net
GigabitEthernet0/0/1(192.168.1.1):
IGMP is enabled
Current IGMP version is 2
IGMP state: up
IGMP group policy: none
IGMP limit: -
Value of query interval for IGMP (negotiated): -
Value of query interval for IGMP (configured): 60 s
Value of other querier timeout for IGMP: 0 s
Value of maximum query response time for IGMP: 10 s
Querier for IGMP: 192.168.1.1 (this router)
Given this, which of the following statements are true?
A switch running a later IGMP version can identify Report messages of an earlier IGMP version, but the switch running an earlier IGMP version cannot identify Report messages of a later IGMP version. To ensure that IGMP runs properly, you are advised to set the IGMP version on the switch to be the same as or later than the IGMP version of member hosts.
When two routers exchange LSDB information using DD packets, a master/slave relationship is formed first, the router with a larger router ID is the master, and determine the MS bit.
Link aggregation is a common network technology. Which of the following are advantages of link aggregation?
In an IPv4 address space, Class D addresses are used for multicast. Among Class D addresses, which of the following is the permanent group address range reserved for routing protocols?
This configuration is part of RTA configuration. Which of the following statements regarding the configuration are true?
[RTA] ospf 100
[RTA-ospf-100]silent-interface GigabitEthernet 1/0/0
The traffic limiting policy feature only supports the number of connections initiated by the specified IP or the number of connections received.
When receiving a packet, a router matches the packet against ACL rules. The ACL matching result is either Matched or Unmatched. If the matching result is Unmatched, which of the following are possible causes?
A BGP device receives a route carrying an unknown attribute from a peer but does not know whether other devices need the attribute. In this case, the BGP device retains this attribute when advertising the route to other peers. Which of the following attributes is of this type?
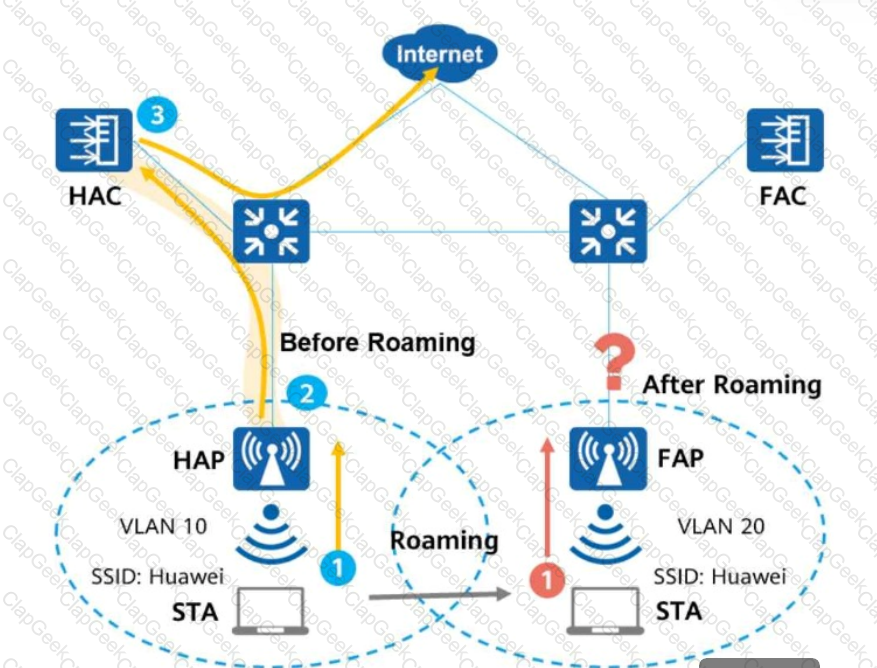
As shown in the figure, data traffic is forwarded in tunnel mode along the path of STA -> HAP -> HAC -> upper-layer network before roaming. What is the flow direction of data traffic after Layer 3 roaming?
In an OSPF routing domain, two routers must be specified as one DR and one BDR in a broadcast or NBMA network with at least two routers.
The Next_Hop attribute in BGP records the next hop of a route. Similar to the next hop in an IGP, the Next_Hop attribute in BGP must be the IP address of a peer interface.
In VRRP networking, if VRRP is not configured to track an uplink interface and the uplink interface or link of the master device in a VRRP group fails, no switchover will be triggered. As a result, a traffic blackhole occurs.
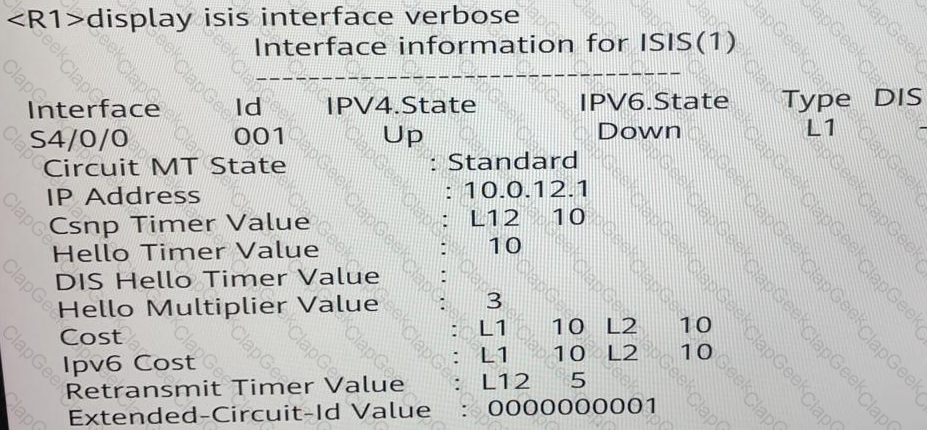
A local router runs IS-IS and its command output is shown in the following figure. Which of the following statements is true?
On an OSPF network, if two indirectly connected routers with the same router ID run in the same area, Type 1 LSA calculation fails.
When multiple access channels are set for the same access requirement, the insecure access channels are not used and secure access channels are selected in normal cases. Which of the following are secure access channels?
On a BGP network, a route-policy can be used to modify route attributes. Which of the following statements is false about route-policies?
Similar to the OSPF DR, the IS-IS DIS needs to be elected on a broadcast network. However, the OSPF DR is preemptive by default, whereas the IS-IS DIS is not preemptive by default.
OSPF networks are classified into four types of networks by link layer protocol. Drag the following link layer protocols to the corresponding network types.(Token is reusable)

A large shopping mall configures a VLAN pool to prevent network performance deterioration caused by potentially large broadcast domains. A network engineer runs the display vlan pool name STA command to check information about the VLAN pool. The following command output is displayed:
Which of the following statements are true?
After which of the following parameters are modified does an IS-IS neighbor relationship need to re-established?
On an OSPF network, Type 7 LSAs can be generated only by ASBRs in NSSAs or stub areas and describe AS-external routes.
RSTP provides different functions in different scenarios. Which of the following statements Is false?
STP ensures a loop-free network but has a slow network topology convergence speed, affecting communication quality. RSTP has made some improvements based on STP. Which of the following improvements is not included?
During routine operation and maintenance, an engineer checks the IGMP configuration on RTA. The configuration is as follows:
Interface information of VPN-Instance: public net
GigabitEthernet0/0/1 (192.168.1.1):
IGMP is enabled
Current IGMP version is 2
IGMP state: up
IGMP group policy: none
IGMP limit: -
Value of query interval for IGMP (negotiated): -
Value of query interval for IGMP (configured): 60 s
Value of other querier timeout for IGMP: 0 s
Value of maximum query response time for IGMP: 10 s
Querier for IGMP: 192.168.1.1 (this router)
Given this, which of the following statements is false?
The BFD (Bidirectional Forwarding Detection) state machine implements a three-way handshake for BFD session setup or teardown. Which of the following session states are involved in BFD session setup?


