When designing IGP routes for an enterprise bearer WAN, ensure that the metric of aggregation-layer links is smaller than that of access-layer links, so that data can be preferentially forwarded over aggregation-layer links.
In the admission design for large- and medium-sized campus networks, which of the following authentication modes can be used for PCs connected to IP phones?
On a broadcast network, if the DR priorities of two interfaces connecting two routers are set to 0, in which of the following states will the OSPF neighbor relationship stay?
iMaster NCE-Campus provides the terminal identification function to display the terminal type, operating system, and manufacturer information.
Refer to the following command output on the router R1. Which of the following statements isincorrect?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:23 UTC-08:00
Description: ! 0.0.3.3
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.1.1 (LoopBack0), destination 10.0.3.3
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Current system time: 15:21:37-08:00
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 0 bits/sec, 0 packets/sec
13 seconds input rate 0 bits/sec, 0 packets/sec
13 seconds output rate 448 bits/sec, 0 packets/sec
9 packets output, 824 bytes
0 output error
Input bandwidth utilization : -
Output bandwidth utilization : -
Which of the following number sequences can be matched by the regular expression100.$?
Which of the following statements about configuring user access authentication is incorrect?
MPLS implements data forwarding based on two different planes. Which of the following statements regarding the forwarding mechanism are correct?
On the network shown in the figure, OSPF-based SR-MPLS TE is enabled on all routers. Which of the following adjacency labels are allocated by P3?
Which of the following statements aboutprefix segments and adjacency segmentsare correct?
Refer to the output information of a device below. According to the information, which of the following MPLS labels is carried in a data packet forwarded by the device to 10.0.1.1?
In the Huawei SD-WAN Solution, the topologies of different VNs must be the same.
The Ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is ______ IRB forwarding. (Capitalize the first letter.)
A client sends an HTTP request to a server, and the server sends back an HTTP response. Which of the following parameters isnotcarried in the HTTP response?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following BGP EVPN routes is used to advertise MAC addresses, ARP entries, and IRB routes?
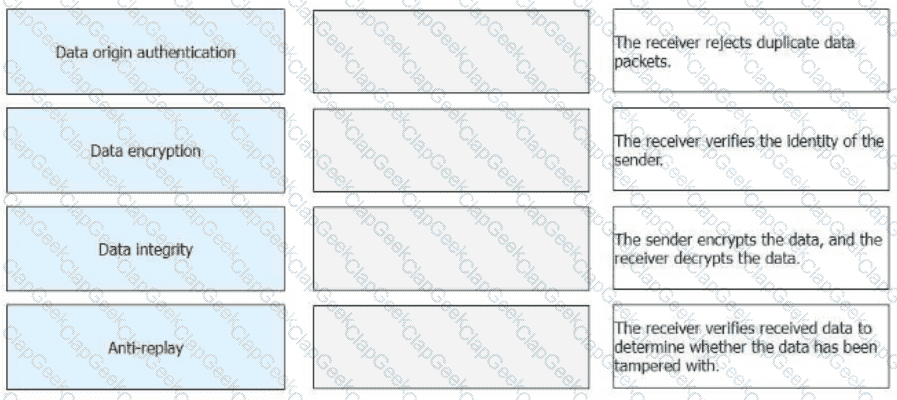
Drag the IPsec functions on the left to the corresponding function description on the right.
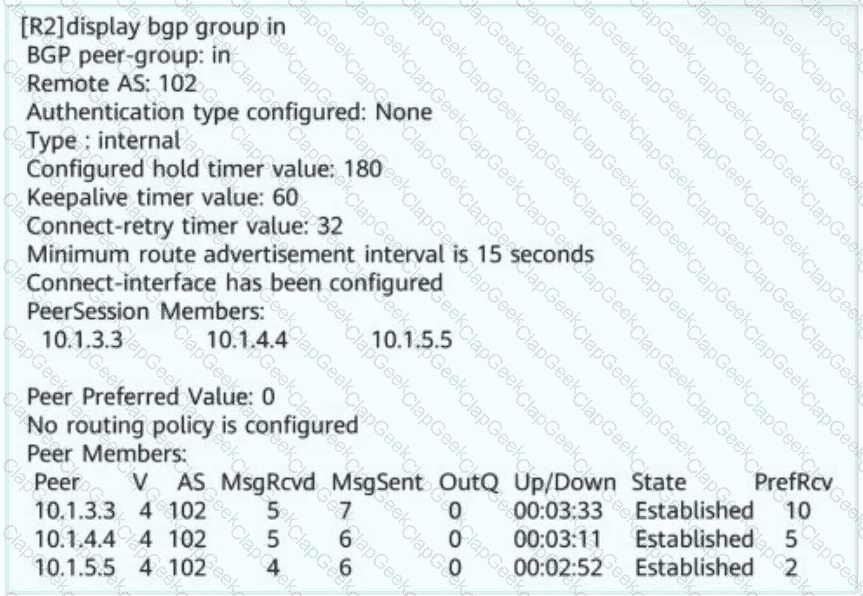
Network administrator A wants to view the BGP peer status of R2. The BGP peer status of R2 is shown in this figure. Obtain the following information: R2 resides in AS _____ (Enter only digits. Do not add punctuations or spaces.)
An O&M platform mainly provides unified monitoring and performance management for network devices. Which of the following is NOT device monitoring data?
The following figure shows the inter-AS MPLS L3VPN Option C (Solution 2). ASBR-PE2 is connected to CE3 and runs eBGP.
To enable all CEs to communicate with each other, which of the following address families must peer relationships be enabled in the BGP process of ASBR-PE2?
In the following figure, all routers are running OSPF. Given this, which of the following statements is correct?
NETCONF provides a set of mechanisms for managing network devices. NETCONF operations take place on a configuration datastore of network devices. Which of the following statements is incorrect about the configuration datastore?
Which of the following inter-AS MPLS L3VPN solutions does not require MPLS to run between ASBRs?
Whenstatic IPsec VPNis used for WAN interconnection in theHuawei CloudCampus Solution, theAP, Router, and ____can be used as egress devices.
Before connecting an SSH client to an SSH server in public key authentication mode, a client needs to create a key pair. Which of the following commands is used to create a DSS key pair on the client using Git Bash?
New IS-IS TLVs are used to carry IPv6 addresses and reachability information to support IPv6 route processing and calculation.
Which of the following statements about static VXLAN tunnel configuration are correct?
In thesmall and midsize campus network designbased on theHuawei CloudCampus Solution, when over100 branchesneed to communicate with each other, which of the following interconnection networking models is recommended?
gRPC (Google Remote Procedure Call)is a language-neutral, platform-neutral, and open-source remote RPC system that supportsunary RPCs and streaming RPCs.
Which of the following service methodsare NOT supportedby gRPC?
Theon-premise modeis recommended for controller deployment onsmall and midsize campus networks.
On a CloudCampus virtualized campus network, virtual networks are defined based on services. Each virtual network corresponds to a service, and isolation needs to be manually configured between virtual networks.
Which of the following operations is not involved in the middle phase of a migration?
In the firewall hot standby scenario, which of the following status information can be backed up between the active and standby firewalls?
As shown in the figure, PE1 establishes an EVPN peer relationship with each of PE2 and PE3. When the network is initialized, CE1 sends an ARP request packet.
Which of the following statements are correct about how a PE processes the packet?
When MPLS/BGP IP VPN is deployed, which of the following statements is incorrect about BGP route exchange between PEs and CEs?
On an SR-MPLS network, manually configured prefix SIDs on different devices may conflict with each other. Assume that there are four routes (prefix/mask SID) as follows. Which of the following routes will be selected according to the conflict handling principle?
Which of the following headend behaviors can insert SRHs into IPv6 packets? (Select All that Apply)
In the following figure, OSPF is enabled on all router interfaces. The IP addresses marked in the figure belong to Loopback0 of the routers.
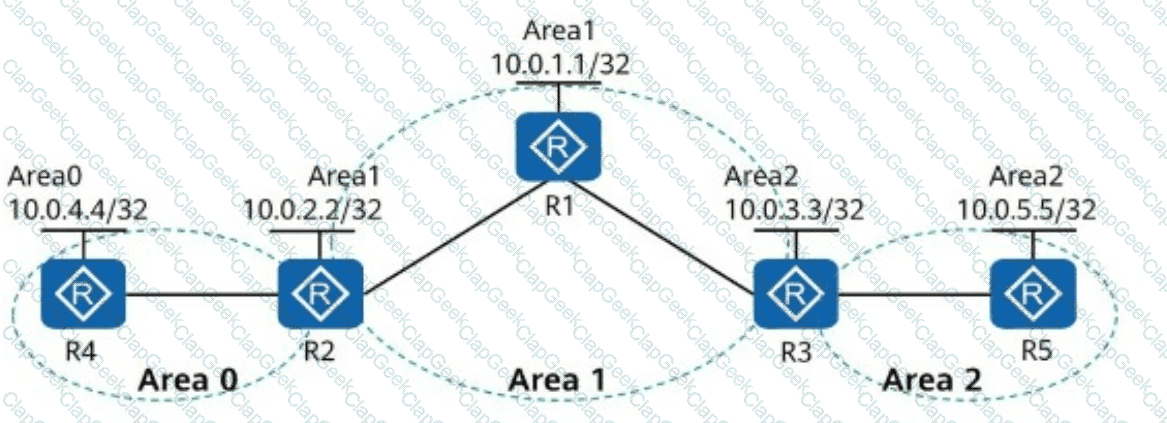
The Loopback0 addresses of R1 and R2 are advertised in Area 1, the Loopback0 address of R4 is advertised in Area 0, and the Loopback0 addresses of R3 and R5 are advertised in Area 2. Given this, which of the following IP addresses can ping each other?
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
After the reset isis all command is run, the specified IS-IS process is reset, and all involved IS-IS neighbor relationships are re-established; however, IS-IS statistics are not cleared.
Drag theIPsec functionson the left to the corresponding function description on the right.
On the network shown in the following figure, a remote LDP session needs to be established between SWA and SWC. Which of the following statements is correct?
[SWA] mpls lsr-id 1.1.1.1
[SWA] mpls
[SWA-mpls] mpls ldp
[SWC] mpls lsr-id 33.3.3.3
[SWC] mpls
[SWC-mpls] mpls ldp
SWA ---- SWB ---- SWC
<------ Remote LDP Session ------>
On a router,SRv6is enabled, and the configurations shown below are performed. Which of the following statements about the configurations are correct?
[Router-segment-routing-ipv6] locator srv6_locator1 ipv6-prefix 2001:DB8:ABCD::/64 static 32
In the LDP session establishment process, the initiator sends an Initialization message for parameter negotiation. Which message will be sent by the responder if it does not accept negotiation parameters?
The RR (Route Reflector) is critical to the Huawei SD-WAN Solution, and its deployment mode varies based on the scenario. In which of the following modes can an RR be deployed?
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
To obtain the token ID of iMaster NCE, you need to send an HTTP request message that includes the following Python code to invoke an iMaster NCE RESTful API.
Which of the following statements is incorrect?
import requests
nbi_name = "demo13@north.com"
nbi_pwd = "CgocVcVe1@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {"Content-Type": "application/json", "Accept": "application/json"}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=False)
Which of the following methods can be used to establish IPsec SAs? (Select All that Apply)
To obtain thetoken IDofiMaster NCE, you need to send anHTTP requestusing the followingPython codeto invoke aniMaster NCE RESTful API:
Which of the following statements isincorrect?
During the implementation of iMaster NCE-Campus Wi-Fi location-based services (LBS), terminal location data is sent to an LBS platform through HTTP requests. Which of the following data formats is used in such HTTP requests?
Which of the following statements is incorrect about the user authentication points on the network?
Which of the following statements about BGP EVPN principles are correct in a scenario where a VXLAN tunnel is dynamically established through BGP EVPN?
An LSR supports various label retention modes. Which of the following statements regarding the liberal mode are correct?
Which of the following statements is incorrect about access control on small and midsize campus networks based on the Huawei CloudCampus solution?
An SRLB is a set of user-specified local labels reserved for SR-MPLS. These labels are locally configured and have only local significance. Therefore, they are not advertised through the IGP.
In the CloudCampus public cloud scenario, if deployment through the Huawei registration query center is used, you do not need to configure DHCP Option 148 on the DHCP server of the campus network.
Which of the following fields is added to BGP4+ Update packets to advertise IPv6 routes?
SR-MPLS uses the MPLS forwarding plane, and therefore requires MPLS to be enabled. Which of the following conditions must be met for MPLS to be automatically enabled on an interface? (Select all that apply)
Which of the following statements regarding OSPF neighbor relationship faults is incorrect?
Telemetry data must be encoded in GPB binary format. This format reduces the number of bytes in telemetry messages and improves the transmission efficiency compared with messages encoded in JSON format.
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
Which of the following intelligent traffic steering policies can be used to fully utilize link bandwidth and implement link bandwidth-based load balancing on an enterprise network with multiple links?
Which of the following statements about SR-MPLS characteristics are correct? (Select all that apply)
An engineer often remotely logs in to the device to check the device status. The engineer can use the Python Paramiko and telnetlib libraries to implement automatic remote login through Python scripts. The remote login implemented using telnetlib is more secure.
During WLAN planning and design, channels 1, 6, and 11 are recommended on the 2.4 GHz frequency band, and channels 1, 5, 9, and 13 are recommended in high-density scenarios. On the 5 GHz frequency band, it is recommended thathigh-frequency and low-frequency channels of adjacent APs be staggered to prevent overlapping.
An SRv6 Policy can be either statically configured on a device or dynamically generated by the controller and then delivered to the device.
In the Huawei CloudCampus Solution, which of the following deployment modes are supported by Huawei switches?
Which of the following statements aboutOPS (Open Programmability System) application scenariosisincorrect?
A network administrator runs thedisplay telemetry subscriptioncommand on a device to check telemetry subscription information. The command output is as follows:
[~CE] display telemetry subscription
Sub-name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
Sub-state : PASSIVE
Total subscription number is : 1
Which of the following statements is incorrect?
Huawei Open Programmability System (OPS) uses HTTP methods to access managed objects to manage network devices. To facilitate script compilation, Huawei OPS provides the Python script template. In the Python script template, what are the contents of the Content-type and Accept fields in the header of an HTTP request packet?
When you configure avirtualized campus networkoniMaster NCE-Campus, Fit APs can immediately go online after you add them toiMaster NCE-Campus.
In SSP packages, Jinja2 templates are used to implement mapping. In the Jinja2 syntax, {% ... %} contains control structures, for example, a 'for' loop.
On traditional campus networks, network admission control (NAC), VLAN, and ACL technologies are used to control users' network access rights. This results in heavy network O&M workload. Which of the following improvements does the free mobility solution of iMaster NCE-Campus make to traditional campus networks in terms of policy management and control?
The following information is displayed during OSPF troubleshooting. Based on this information, which of the following is the cause of the failure in establishing an OSPF adjacency relationship?
OSPF Process 1 with Router ID 10.0.12.2
OSPF error statistics
Interface: GigabitEthernet0/0/0 (10.0.12.2)
General packet errors:
0 : Bad version 0 : Bad checksum
0 : Bad area id 0 : Bad authentication type
0 : Bad authentication key 0 : Unknown neighbor
0 : Bad net segment 0 : Extern option mismatch
0 : Router id confusion
HELLO packet errors:
2 : Netmask mismatch 0 : Hello timer mismatch
0 : Dead timer mismatch 0 : Invalid Source Address
OSPF is deployed on a campus network to implement network interconnection. An engineer configures R2 as shown in the figure. Which of the following statements is incorrect about LSAs on the OSPF network?
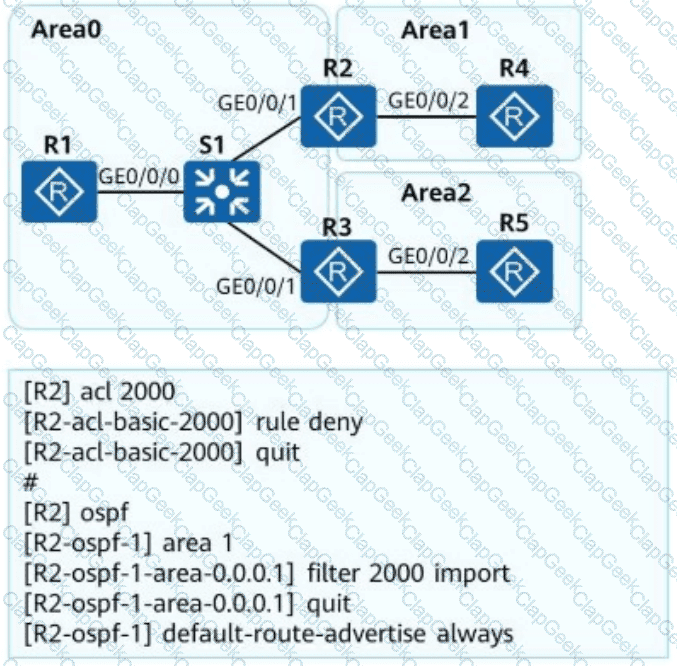
In OSPF, an ABR translates all Type 7 LSAs in a Not-So-Stubby Area (NSSA) into Type 5 LSAs.
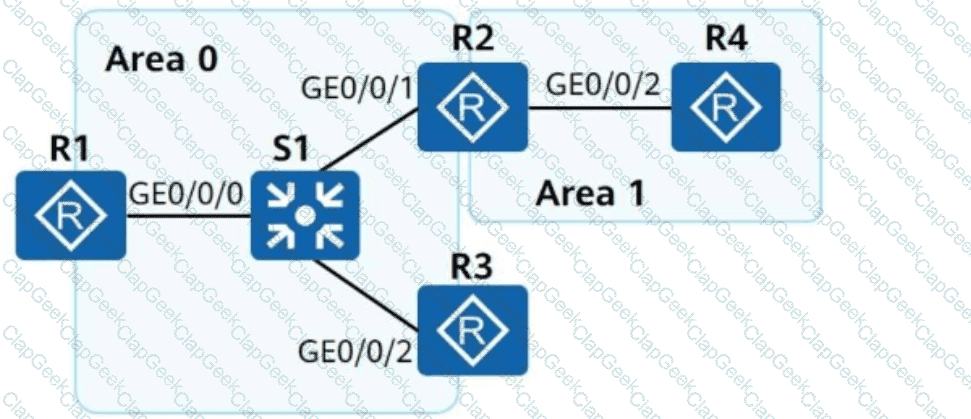
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and these routers use OSPFv3 for network connectivity. Which of the following statements about LSAs generated by the OSPFv3 network is incorrect?
SR-MPLS uses IGP extensions to advertise labels and reserve bandwidth to support high-bandwidth services.
MPLS supports both static and dynamic LSP establishment. Which of the following protocols cannot dynamically establish LSPs in MPLS TE scenarios? (Select all that apply)
Which of the following is the mapping between VNIs and BDs in VXLAN implementation?
Flavors are additional behaviors defined to enhance theEnd series instructionsinSRv6. Which of the followingEnd instructionscan thePSP flavorbe attached to?
In theHuawei CloudCampus Solution, which of the following devices can go online through theregistration query center?
Which of the following statements are correct about authentication points and policy enforcement points in Huawei's free mobility solution?
By default, the domain ID of an OSPF process is the same as the process ID. You can run the domain-id command in the OSPF process view to change a domain ID.
Which of the following statements is incorrect about intranet security design for a large or medium-sized virtualized campus network?
OSPF is a mature protocol and is unlikely to have route computation errors in a regular networking environment under correct configurations. Which of the following statements are correct about the possible causes preventing an OSPF neighbor relationship from entering Full state?
Which of the following is the purpose of configuring IS-IS fragmentation on an IS-IS device?
On an SR-MPLS network, manually configured prefix SIDs on different devices may conflict with each other. Assume that there are four routes (prefix/mask SID) as follows.Which of the following routes will be selected according to the conflict handling principle?
Which of the following statements aboutBIER (Bit Index Explicit Replication) and PIM (Protocol Independent Multicast)are correct?