A user reports that a specific application is not working properly. This application makes
multiple connection to the server and must have the same address every time from a pool and this behavior needs to be changed.
What would solve this problem?
You are using AutoVPN to deploy a hub-and-spoke VPN to connect your enterprise sites.
In this scenario, which two statements are true? (Choose two.)
Which two statements about policy enforcer and the forescout integration are true? (Choose two)
Referring to the exhibit, you are assigned the tenantSYS1 user credentials on an SRX series
device.
In this scenario, which two statements are correct? (Choose two.)
You want to use a security profile to limit the system resources allocated to user logical systems.
In this scenario, which two statements are true? (Choose two.)
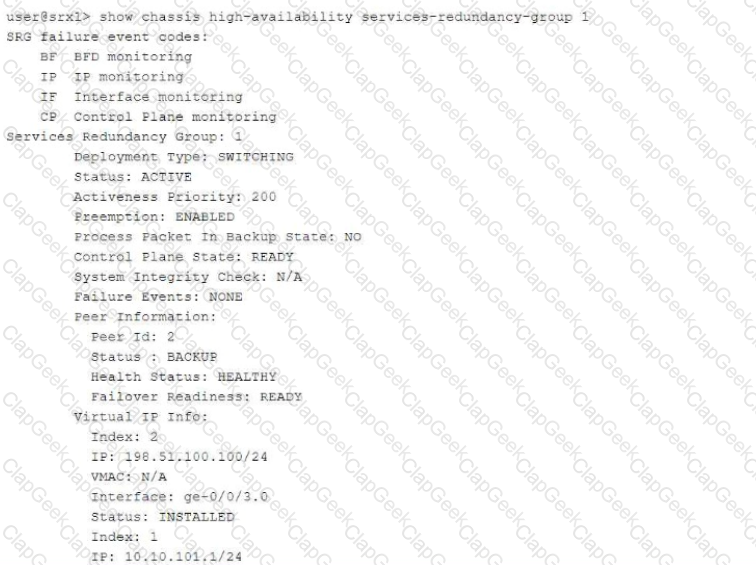
Referring to the exhibit,
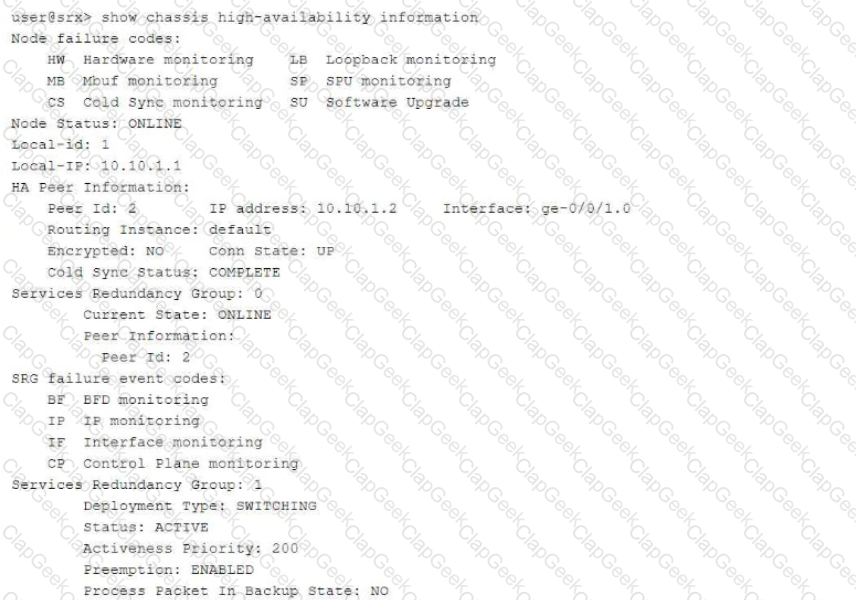
which three statements about the multinode HA environment are true? (Choose three.)
A company has acquired a new branch office that has the same address space as one of its local networks, 192.168.100.0/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
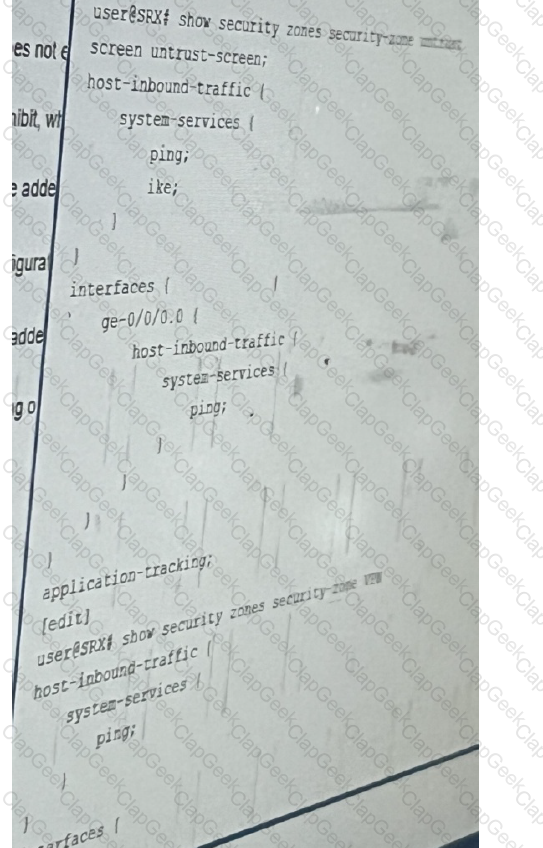
Referring to the exhibit, you are attempting to set up a remote access VPN on your SRX series devices.
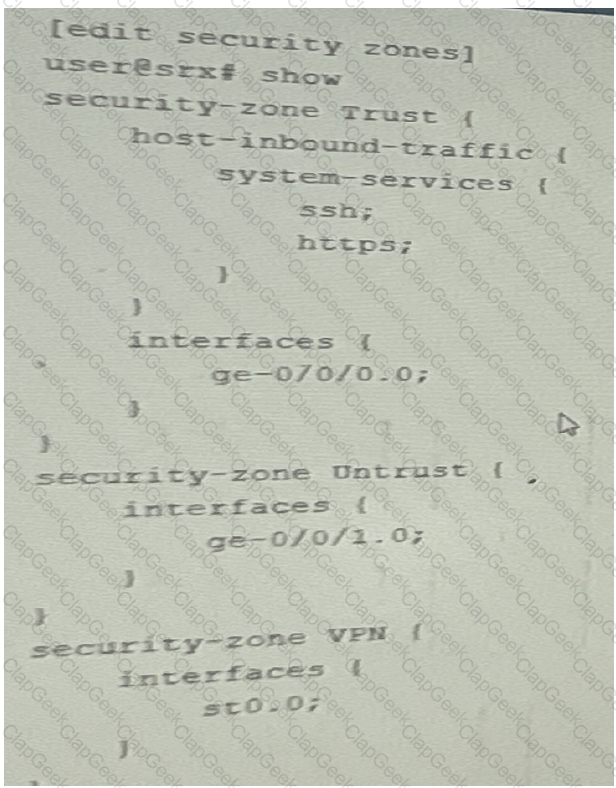
However you are unsure of which system services you should allow and in which zones they should be allowed to correctly finish the remote access VPN configuration
Which two statements are correct? (Choose two.)
Exhibit:
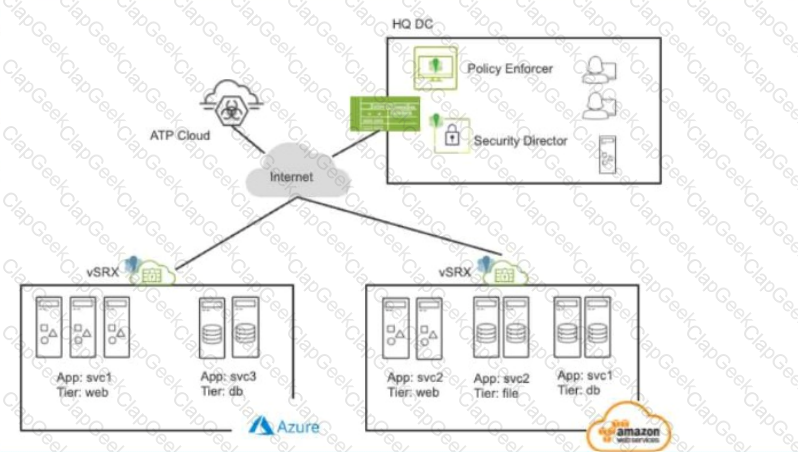
Referring to the exhibit, what do you use to dynamically secure traffic between the Azure and AWS clouds?
Exhibit:

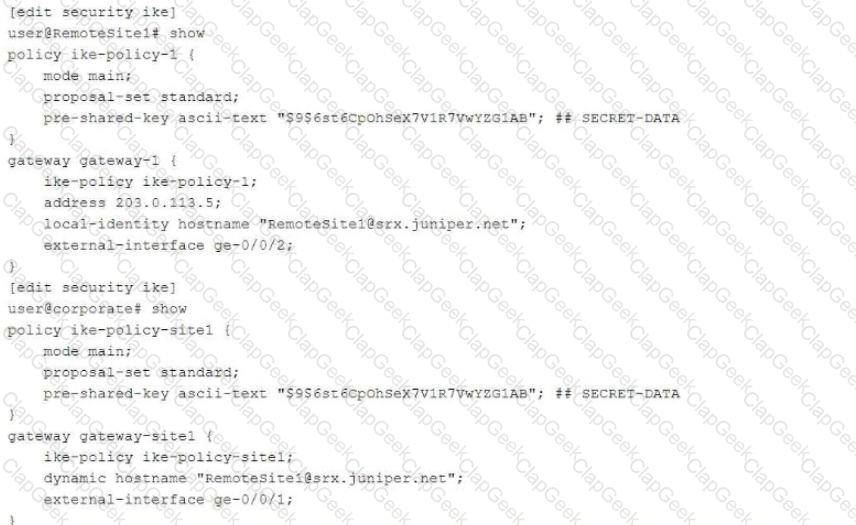
You are troubleshooting a new IPsec VPN that is configured between your corporate office and the RemoteSite1 SRX Series device. The VPN is not currently establishing. The RemoteSite1 device is being assigned an IP address on its gateway interface using DHCP.
Which action will solve this problem?
Exhibit:
Referring to the exhibit, which two statements are correct? (Choose two.)
You are asked to create multiple virtual routers using a single SRX Series device. You must ensure that each virtual router maintains a unique copy of the routing protocol daemon (RPD) process.
Which solution will accomplish this task?
You are setting up multinode HA for redundancy.
Which two statements are correct in this scenario? (Choose two.)
In a multinode HA environment, which service must be configured to synchronize between nodes?
You are enabling advanced policy-based routing. You have configured a static route that has a next hop from the inet.0 routing table. Unfortunately, this static route is not active in your routing instance.
In this scenario, which solution is needed to use this next hop?
What are three attributes that APBR queries from the application system cache module. (Choose Three)
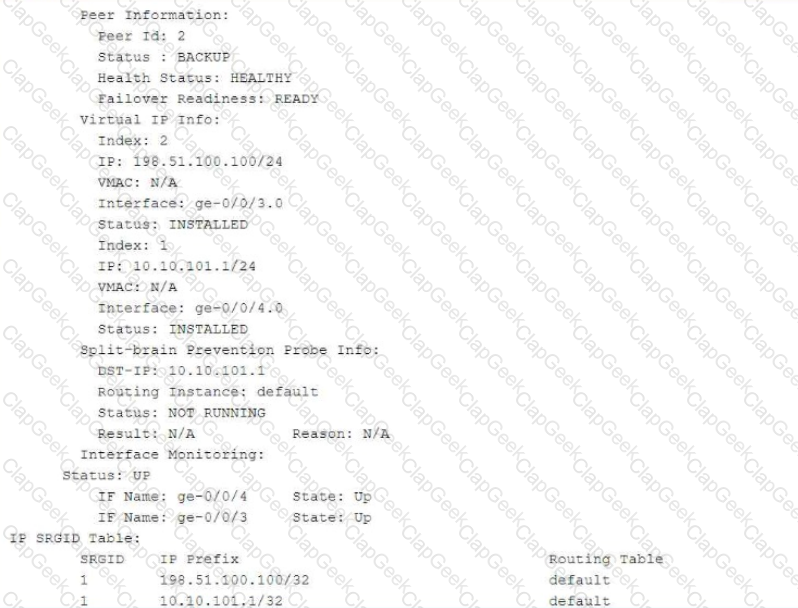
The exhibit shows part of the flow session logs.
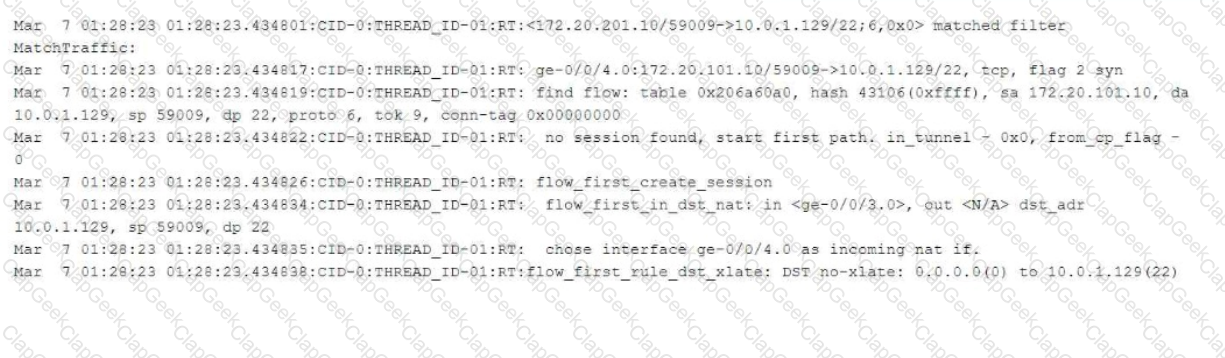
Which two statements are true in this scenario? (Choose two.)
You have configured the backup signal route IP for your multinode HA deployment, and the ICL link fails.
Which two statements are correct in this scenario? (Choose two.)
Referring to the exhibit,
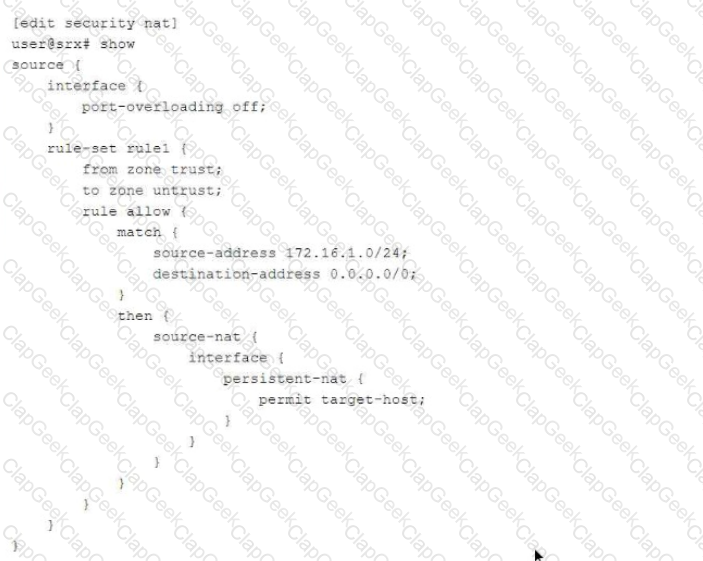
which two statements are correct about the NAT configuration? (Choose two.)
You are asked to select a product offered by Juniper Networks that can collect and assimilate data from all probes and determine the optimal links for different applications to maximize the full potential of AppQoE.
Which product provides this capability?
Exhibit:
The Ipsec VPN does not establish when the peer initiates, but it does establish when the SRX
series device initiates. Referring to the exhibit, what will solve this problem?
You have an initial setup of ADVPN with two spokes and a hub. A host at partner Spoke-1 is sending traffic to a host at partner Spoke-2.
In this scenario, which statement is true?
You are configuring an interconnect logical system that is configured as a VPLS switch to allow two logical systems to communicate.
Which two parameters are required when configuring the logical tunnel interfaces? (Choose two.)
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
You want to create a connection for communication between tenant systems without using physical revenue ports on the SRX Series device.
What are two ways to accomplish this task? (Choose two.)
You are asked to configure tenant systems.
Which two statements are true in this scenario? (Choose two.)
A company has acquired a new branch office that has the same address space of one of its local networks, 192.168.100/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
You configured two SRX series devices in an active/passive multimode HA setup.
In this scenario, which statement is correct?
You have cloud deployments in Azure, AWS, and your private cloud. You have deployed
multicloud using security director with policy enforcer to. Which three statements are true in this scenario? (Choose three.)


