Which of the following technologies is most appropriate for a business that requires high-speed access to frequently used web content, such as images and videos?
Network administrators are using the Telnet protocol to administer network devices that are on the 192.168.1.0/24 subnet. Which of the following tools should the administrator use to best identify the devices?
Which of the following most directly secures sensitive information on a network?
A user connects to a corporate VPN via a web browser and is able to use TLS to access the internal financial system to input a time card. Which of the following best describes how the VPN is being used?
A company recently implemented a videoconferencing system that utilizes large amounts of bandwidth. Users start reporting slow internet speeds and an overall decrease in network performance. Which of the following are most likely the causes of the network performance issues? (Select two)
An imaging workstation at a hospital is experiencing intermittent connectivity loss. Which of the following would most likely be used to resolve the issue at the least expense?
A help desk technician receives a report that users cannot access internet URLs. The technician performs ping tests and finds that sites fail when a URL is used but succeed when an IP is used. Which of the following tools should the technician utilize next?
A network engineer wants to implement a new IDS between the switch and a router connected to the LAN. The engineer does not want to introduce any latency by placing the IDS in line with the gateway. The engineer does want to ensure that the IDS sees all packets without any loss. Which of the following is the best way for the engineer to implement the IDS?
A network technician sets up a computer on the accounting department floor for a user from the marketing department. The user reports that they cannot access the marketing department’s shared drives but can access the internet. Which of the following is the most likely cause of this issue?
Which of the following actions should be taken as part of the first step of the troubleshooting methodology?
A storage network requires reduced overhead and increased efficiency for the amout of data being sent. Which of the following should an engineer likely configure to meet these requirements>?
A network technician is troubleshooting the connection to the company website. The traceroute command produces the following output:
Traceroute towww.mysite.com(8.8.8.8) over a maximum of 30 hops
10.1.1.1 <1 ms 2. * <1 ms <1 ms
k k
k kTraceroute completeWhich of the following should the technician do to identify the path to the server?
A technician is troubleshooting a user's laptop that is unable to connect to a corporate server. The technician thinks the issue pertains to routing. Which of the following commands should the technician use to identify the issue?
A customer needs six usable IP addresses. Which of the following best meets this requirement?
A company's network is experiencing high levels of suspicious network traffic. The security team finds that the traffic is coming from an unknown, foreign IP address. Which of the following is the most cost-efficient way to mitigate this threat?
Which of the following ports is used to transfer data between mail exchange servers?
Which of the following tools uses ICMP to help determine whether a network host is reachable?
During a security audit, a consulting firm notices inconsistencies between the documentation and the actual environment. Which of the following can keep a record of who made the changes and what the changes are?
Which of the following VPN configurations forces a remote user to access internet resources through the corporate network?
A company reports that their facsimile machine no longer has a dial tone when trying to send a fax. The phone cable is damaged on one end. Which of the following types of connectors should a technician replace?
Which of the following technologies are X.509 certificates most commonly associated with?
Which of the following requires network devices to be managed using a different set of IP addresses?
Which of the following will allow secure, remote access to internal applications?
A user tries to visit a website, but instead of the intended site, the page displays vmw.cba.com. Which of the following should be done to reach the correct website?
Which of the following should be configured so users can authenticate to a wireless network using company credentials?
Which of the following is used to store and deliver content to clients in a geographically distributed manner using edge servers?
A network administrator is unable to ping a remote server from a newly connected workstation that has been added to the network. Ping to 127.0.0.1 on the workstation is failing. Which of the following should the administrator perform to diagnose the problem?
A network administrator is planning to host a company application in the cloud, making the application available for all internal and third-party users. Which of the following concepts describes this arrangement?
Which of the following cloud deployment models is most commonly associated with multitenancy and is generally offered by a service provider?
An attacker gained access to the hosts file on an endpoint and modified it. Now, a user is redirected from the company’s home page to a fraudulent website. Which of the following most likely happened?
A user tries to visit www.abc.com, but the website that displays is www.cba.com. Which of the following should be done in order to reach the correct website?
A network engineer is installing new PoE wireless APs. The first five APs deploy successfully, but the sixth one fails to start. Which of the following should the engineer investigate first?
Which of the following fiber connector types is the most likely to be used on a network interface card?
In the troubleshooting methodology, which of the following actions comes after verifying that the initial problem has been resolved?
A network technician is working on a PC with a faulty NIC. The host is connected to a switch with secured ports. After testing the connection cables and using a known-good NIC, the host is still unable to connect to the network. Which of the following is causing the connection issue?
Which of the following types of attacks is most likely to occur after an attacker sets up an evil twin?
Which of the following attacks can cause users who are attempting to access a company website to be directed to an entirely different website?
A network engineer queries a hostname using dig, and a valid IP address is returned. However, when the engineer queries that same IP address using dig, no hostname is returned. Which of the following DNS records is missing?
Which of the following is the greatest advantage of maintaining a cold DR site compared to other DR sites?
A client wants to increase overall security after a recent breach. Which of the following would be best to implement? (Select two.)
A network technician implements a switch with multiple VLANs. Which of the following items should the technician configure to ensure that clients can communicate with clients in other VLANs?
Employees report that the network is slow. The network engineer thinks the performance issue is with an upstream router. Which of the following tools should the engineer use to determine the location of the issue?
Which of the following is the best way to securely access a network appliance from an external location?
Which of the following involves an attacker traversing from one part of a network to another part that should be inaccessible?
Users cannot connect to an internal website with an IP address 10.249.3.76. A network administrator runs a command and receives the following output:
1 3ms 2ms 3ms 192.168.25.234
2 2ms 3ms 1ms 192.168.3.100
3 4ms 5ms 2ms 10.249.3.1
4 *
5 ’
6 *
7 •
Which of the following command-line tools is the network administrator using?
A research facility is expecting to see an exponential increase in global network traffic in the near future. The offices are equipped with 2.5Gbps fiber connections from the ISP, but the facility is currently only utilizing 1Gbps connections. Which of the following would need to be configured in order to use the ISP's connection speed?
Users report performance issues on the network. A network administrator notices broadcast storms occurring. Which of the following protocols should the administrator configure to mitigate this issue?
A network technician receives a new ticket while working on another issue. The new ticket is critical to business operations. Which of the following documents should the technician reference to determine which ticket to complete first?
A network engineer is testing a website to ensure it is compatible with IPv6. After attempting to ping the website by its IPv6 address, the engineer determines that the DNS has not been set up properly. Which of the following should the network engineer complete to resolve this issue?
A network administrator recently updated configurations on a Layer 3 switch. Following the updates, users report being unable to reach a specific file server. Which of the following is the most likely cause?
Users are reporting latency on the network. The network engineer notes the following:
Confirms the only change was a new network switch
Confirms all users are experiencing latency
Thinks the issue is a network loop caused by the lower bridge ID of the new switch
Which of the following describes the next step in the troubleshooting methodology?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host’s TCP/IP stack first. Which of the following commands should the network administrator run?
A network technician is troubleshooting network latency and has determined the issue to be occuring two network switches( Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying. Given the following informtion:
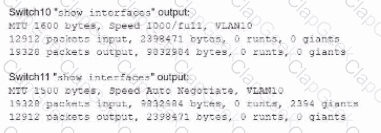
Which of the following should the technician most likely do to resolve the issue?
A network engineer needs to deploy an access point at a remote office so that it will not communicate back to the wireless LAN controller. Which of the following deployment methods must the engineer use to accomplish this task?
Which of the following standards enables the use of an enterprise authentication for network access control?
A university is implementing a new campus wireless network. A network administrator needs to configure the network to support a large number of devices and high-bandwidth demands from students.
Which of the following wireless technologies should the administrator consider for this scenario?
A network security administrator needs to monitor the contents of data sent between a secure network and the rest of the company. Which of the following monitoring methods will accomplish this task?
A network administrator performed upgrades on a server and installed a new NIC to improve performance. Following the upgrades, usera are unable to reach the server. Which of the following is the most likely reason.
Which of the following appliances provides users with an extended footprint that allows connections from multiple devices within a designated WLAN?
A network administrator installs new cabling to connect new computers and access points. After deploying the equipment, the administrator notices a few of the devices are not connecting properly. The administrator moves the devices to a different port, but it does not resolve the issue. Which of the following should the administrator verify next?
A network administrator needs to divide 192.168.1.0/24 into two equal halves. Which of the following subnet masks should the administrator use?
A network engineer needs to virtualize network services, including a router at a remote branch location. Which of the following solutions meets the requirements?
As part of an attack, a threat actor purposefully overflows the content-addressable memory (CAM) table on a switch. Which of the following types of attacks is this scenario an example of?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses (one for a computer and one for a phone). Which of the following classful IPv4 address ranges will be best-suited for the network?
A user's VoIP phone and workstation are connected through an inline cable. The user reports that the VoIP phone intermittently reboots, but the workstation is not having any network-related issues Which of the following is the most likely cause?
A company experiences an incident involving a user who connects an unmanaged switch to the network. Which of the following technologies should the company implement to help avoid similar incidents without conducting an asset inventory?
A network administrator needs to ensure that users accept internet usage rules. Which of the following will help the administrator accomplish this task?
An investment bank is seeking a DR backup solution. Which of the following provides the most cost-effective backup site?
Which of the following typically uses compromised systems that become part of a bot network?
After a recent security awareness phishing campaign, the cybersecurity team discovers that additional security measures need to be set up when users access potentially malicious websites. Which of the following security measures will best address this concern?
A company's marketing team created a new application and would like to create a DNS record for newapplication.comptia.org that always resolves to the same address as www.comptia.org. Which of the following records should the administrator use?
A network engineer is troubleshooting connectivity for a newly installed server on an existing VLAN. The engineer reviews the following output:
C:\> ipconfig
IP Address: 192.168.100.225
Mask: 255.255.255.224
Gateway: 192.168.100.254
Router# show ip route
C 192.168.100.0/24 is directly connected, GigabitEthernet0/0
Which of the following describes the issue?
Which of the following network traffic types is sent to all nodes on the network?
A network administrator receives a ticket from a user. The user reports that they cannot access any websites and that they have already checked everything on their computer. Which of the following is the first action the administrator should take?
Which of the following best describes a group of devices that is used to lure unsuspecting attackers and to study the attackers' activities?
A company receives a cease-and-desist order from its ISP regarding prohibited torrent activity. Which of the following should be implemented to comply with the cease-and-desist order?
Which of the following is the most likely reason an insurance brokerage would enforce VPN usage?
After installing a new 6E wireless router in a small office, a technician notices that some wireless devices are not able to achieve the rated speeds.
Which of the following should the technician check to troubleshoot the issue? (Select two)
A network architect is implementing an off-premises computing facility and needs to ensure that operations will not be impacted by major outages. Which of the following should the architect consider?
Which of the following would be violated if an employee accidentally deleted a customer's data?
Which of the following protocols is used to send networking status messages between clients and servers?
A technician needs to quickly set up a network with five wireless devices. Which of the following network types should the technician configure to accomplish this task?
A network engineer configures a NIC that has an IP address of 192.168.123.232. Which of the following classes is this address an example of?
Which of the following should a company implement in order to share a single IP address among all the employees in the office?
After running a Cat 8 cable using passthrough plugs, an electrician notices that connected cables are experiencing a lot of cross talk. Which of the following troubleshooting steps should the electrician take first?
A network administrator is troubleshooting a connectivity issue between two devices on two different subnets. The administrator verifies that both devices can successfully ping other devices on the same subnet. Which of the following is the most likely cause of the connectivity issue?
A network manager connects two switches together and uses two connecting links. Which of the following configurations will prevent Layer 2 loops?
Which of the following connection methods allows a network engineer to automate the configuration deployment for network devices across the environment?
Which of the following kinds of targeted attacks uses multiple computers or bots to request the same resource repeatedly?
Which of the following routing technologies uses an attribute list for path selection?
Which of the following physical installation factors is the most important when a network switch is installed in a sealed enclosure?
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
An administrator is configuring a switch that will be placed in an area of the office that is accessible to customers. Which of the following is the best way for the administrator to mitigate unknown devices from connecting to the network?
A network administrator needs to fail over services to an off-site environment. This process will take four weeks to become fully operational. Which of the following DR (Disaster Recovery) concepts does this describe?
A network administrator needs to add 255 useable IP addresses to the network. A /24 is currently in use. Which of the following prefixes would fulfill this need?
An organization has four departments that each need access to different resources that do not overlap. Which of the following should a technician configure in order to implement and assign an ACL?
Which of the following protocols has a default administrative distance value of 90?
Which of the following is an XML-based security concept that works by passing sensitve information about users, such as log-in information and attributes, to providers.
An administrator needs to configure an IoT device with a /21 subnet mask, but the device will only accept dotted decimal notation. Which of the following subnet masks should the administrator use?
A user is unable to navigate to a website because the provided URL is not resolving to the correct IP address. Other users are able to navigate to the intended website without issue. Which of the following is most likely causing this issue?
Which of the following is the correct order of components in a bottom-up approach for the three-tier hierarchical model?
A user submits an escalated ticket regarding failed logins on their laptop. The user states that the time displayed on the laptop is incorrect. An administrator thinks the issue is related to the NTP. Which of the following should the administrator do next?
A network administrator needs to assign IP addresses to a newly installed network. They choose 192.168.1.0/24 as their network address and need to create three subnets with 30 hosts on each subnet. Which of the following is a valid subnet mask that will meet the requirements?
A network administrator configured a router interface as 10.0.0.95 255.255.255.240. The administrator discovers that the router is not routing packets to a web server with IP 10.0.0.81/28. Which of the following is the best explanation?
A network administrator is looking for a solution to extend Layer 2 capabilities and replicate backups between sites. Which of the following is the best solution?
Which of the following is used to redistribute traffic between one source and multiple servers that run the same service?
A network administrator needs a solution to isolate and potentially identify any threat actors that are attempting to breach the network. Which of the following should the administrator implement to determine the type of attack used?
Which of the following network ports is used when a client accesses an SFTP server?
Which of the following is the best way to reduce the likelihood of electrostatic discharge?
Which of the following routing protocols is most commonly used to interconnect WANs?
A company wants to implement a disaster recovery site or non-critical applicance, which can tolerance a short period of downltime. Which of the followig type of sites should the company impelement to achive this goal?
An organization moved its DNS servers to new IP addresses. After this move, customers are no longer able to access the organization's website. Which of the following DNS entries should be updated?
Which of the following is most closely associated with having a leased line to a public cloud provider?
Which of the following devices can operate in multiple layers of the OSI model?
Which of the following allows a user to connect to an isolated device on a stand-alone network?
Which of the following concepts describes the idea of housing different customers in the same public cloud data center?
Which of the following is the best networking appliance for interconnecting multiple logical networks and forwarding data packets between them while minimizing latency?
An organization wants better network visibility. The organization's requirements include:
Multivendor/OS-monitoring capabilities
Real-time collection
Data correlation
Which of the following meets these requirements?
An organization recently connected a new computer to the LAN. The user is unable to ping the default gateway. The technician examines the configuration and sees a self-assigned IP address. Which of the following is the most likely cause?
A medical clinic recently configured a guest wireless network on the existing router. Since then, guests have been changing the music on the speaker system. Which of the following actions should the clinic take to prevent unauthorized access? (Select two).
A network administrator needs to set up a multicast network for audio and video broadcasting. Which of the following networks would be the most appropriate for this application?
A network technician needs to resolve some issues with a customer's SOHO network.
The customer reports that some of the devices are not connecting to the network, while others appear to work as intended.
INSTRUCTIONS
Troubleshoot all the network components and review the cable test results by Clicking on each device and cable.
Diagnose the appropriate component(s) by identifying any components with a problem and recommend a solution to correct each problem.
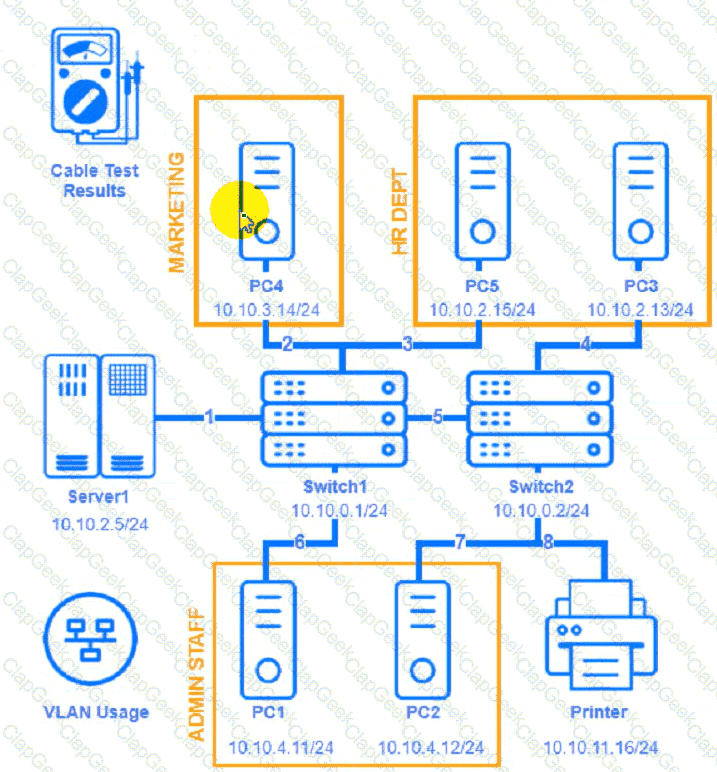


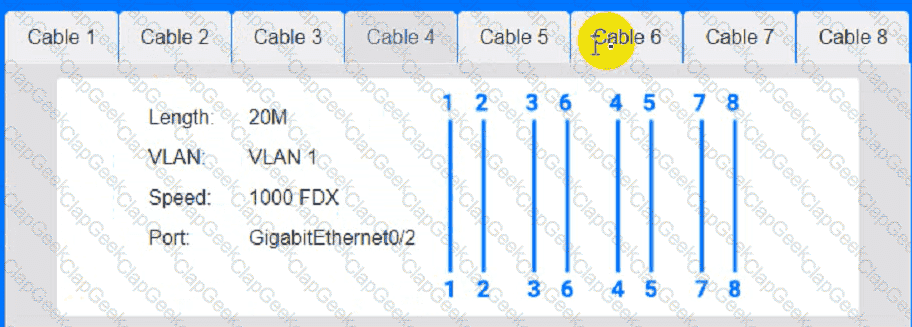
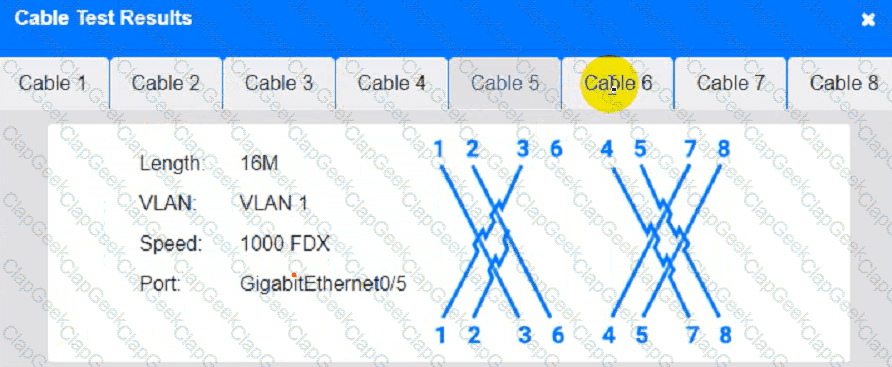
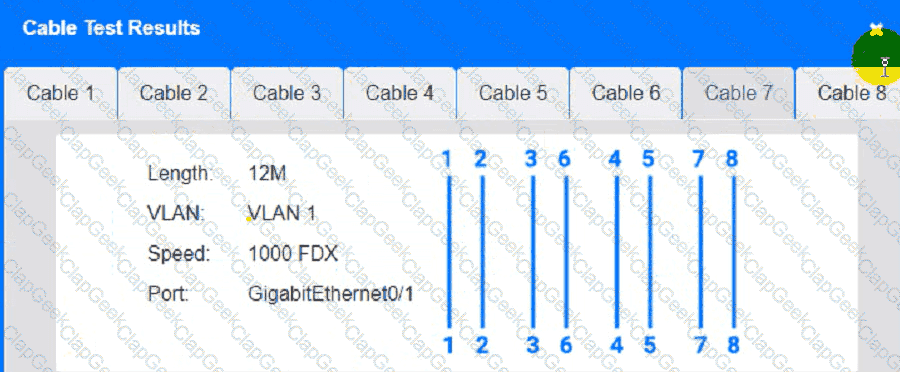
Cable Test Results:
Cable 1:
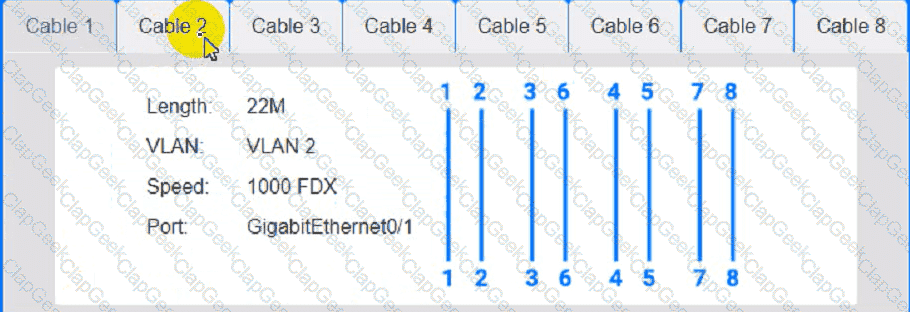
Cable 2:
Cable 3:
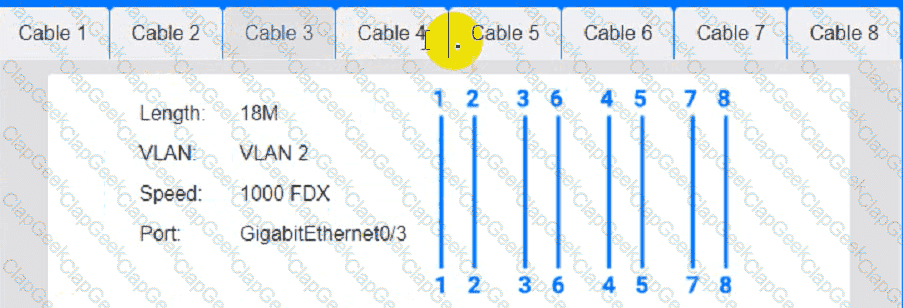
Cable 4:
Which of the following OSI model layers can utilize a connectionless protocol for data transmission?
A wireless technician wants to implement a technology that will allow user devices to automatically navigate to the best available frequency standard. Which of the following technologies should the technician use?
A network administrator needs to connect two routers in a point-to-point configuration and conserve IP space. Which of the following subnets should the administrator use?
A junior network administrator gets a text message from a number posing as the domain registrar of the firm. The administrator is tricked into providing global administrator credentials. Which of the following attacks is taking place?
In an environment with one router, which of the following will allow a network engineer to communicate between VLANs without purchasing additional hardware?
In the troubleshooting methodology, which of the following actions comes after verifying that the initial problem has been resolved?
After a recent merger, a large number of alerts are coming in regarding extremely high utilization. Which of the following should be generated to help inform new alerting requirements?
Which of the following best describes the transmission format that occurs at the transport layer over connectionless communication?
A network administrator prepares a VLAN for a new office while planning for minimal IP address waste. The new office will have approximately 800 workstations. Which of the following network schemes meets the requirements?
A systems administrator is looking for operating system information, running services, and network ports that are available on a server. Which of the following software tools should the administrator use to accomplish this task?
Which of the following steps of the troubleshooting methodology comes after testing the theory to determine cause?
A network engineer adds a tunnel for a new branch network. Which of the following ensures that all data is encrypted inside the tunnel?
A network administrator recently upgraded a wireless infrastructure with new APs. Users report that when stationary, the wireless connection drops and reconnects every 20 to 30 seconds. While reviewing logs, the administrator notices the APs are changing channels.
Which of the following is the most likely reason for the service interruptions?
A network engineer configures the network settings in a new server as follows:
IP address = 192.163.1.15
Subnet mask = 255.255.255.0
Gateway = 192.163.1.255
The server can reach other hosts on the same subnet successfully, but it cannot reach hosts on different subnets. Which of the following is most likely configured incorrectly?


