Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
Which two agents can validate endpoint compliance transparently to the end user? (Choose two.)
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
By default, if after a successful Layer 2 poll, more than 20 endpoints are seen connected on a single switch port simultaneously, what happens to the port?
During an evaluation of state-based enforcement, an administrator discovers that ports that should not be under enforcement have been added to enforcement groups. In which view would the administrator be able to determine who added the ports to the groups?
Refer to the exhibit.
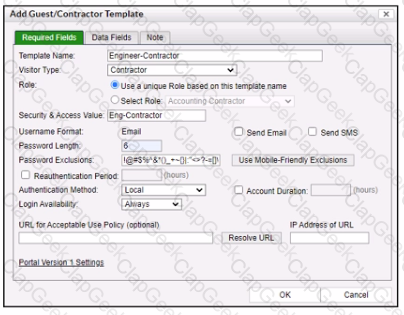
When a contractor account is created using this template, what value will be set in the accounts Rote field?
When FortiNAC is managing FortiGate VPN users, why is an endpoint compliance policy necessary?
An administrator wants the Host At Risk event to generate an alarm. What is used to achieve this result?
Which three of the following are components of a security rule? (Choose three.)


