Which two settings can you configure to speed up routing convergence in BGP? (Choose two.)
Which best describes the SD-WAN traffic shaping mode that bases itself on a percentage of available bandwidth?
Refer to the exhibit.
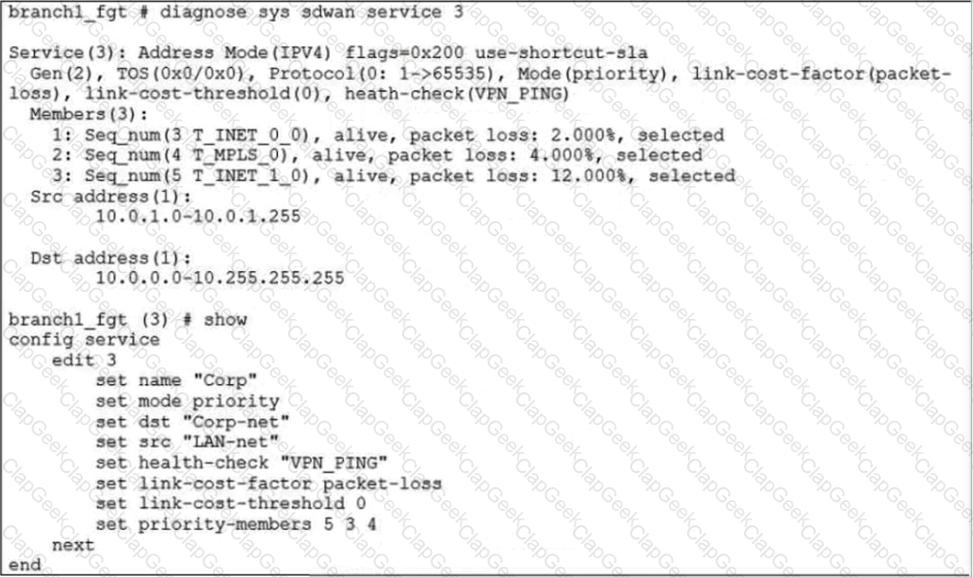
The exhibit shows the SD-WAN rule status and configuration.
Based on the exhibit, which change in the measured packet loss will make T_INET_1_0 the new preferred member?
Refer to the exhibits.
Exhibit A
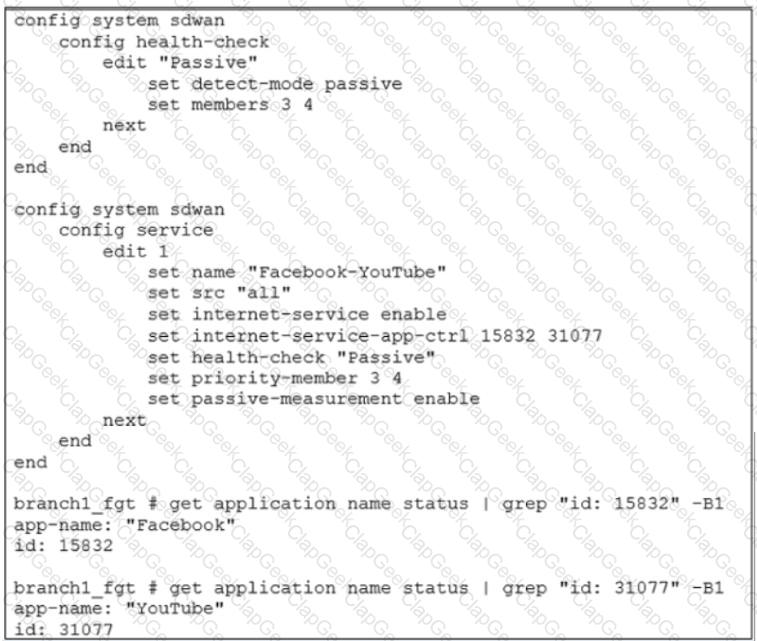
Exhibit B
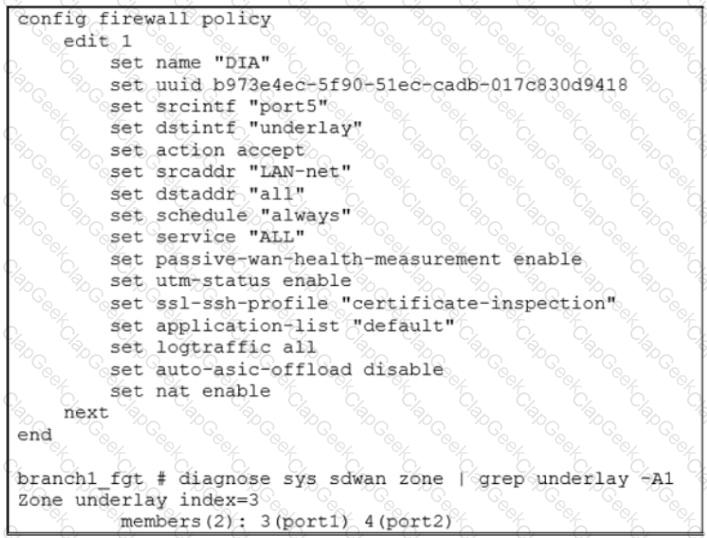
Exhibit A shows the SD-WAN performance SLA configuration, the SD-WAN rule configuration, and the application IDs of Facebook and YouTube. Exhibit B shows the firewall policy configuration and the underlay zone status.
Based on the exhibits, which two statements are correct about the health and performance of port1 and port2? (Choose two.)
What does enabling theexchange-interface-ipsetting enable FortiGate devices to exchange?
Which diagnostic command can you use to show the SD-WAN rules, interface information, and state?
diagnose sys sdwan service
diagnose sys sdwan route-tag-list
diagnose sys sdwan member
Refer to the exhibit.
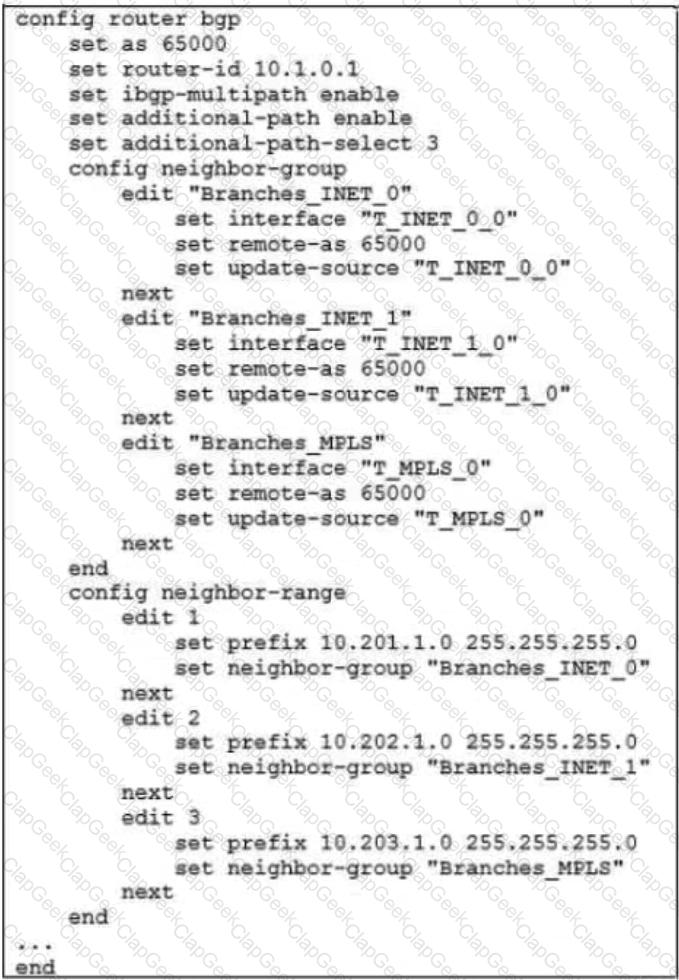
The exhibit shows the BGP configuration on the hub in a hub-and-spoke topology. The administrator wants BGP to advertise prefixes from spokes to other spokes over the IPsec overlays, including additional paths. However, when looking at the spoke routing table, the administrator does not see the prefixes from other spokes and the additional paths.
Based on the exhibit, which three settings must the administrator configure inside each BGP neighbor group so spokes can learn other spokes prefixes and their additional paths? (Choose three.)
Refer to the exhibit.
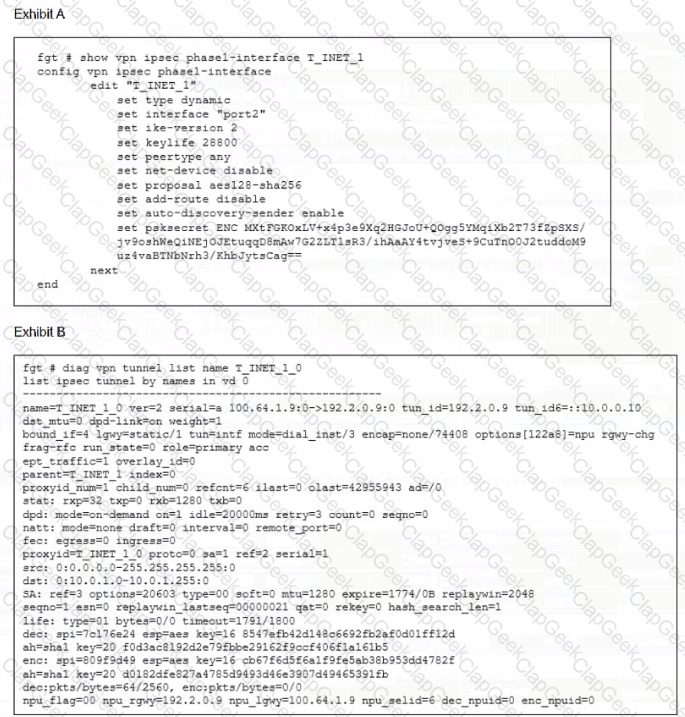
Which two statements about the IPsec VPN configuration and the status of the IPsec VPN tunnel are true? (Choose two.)
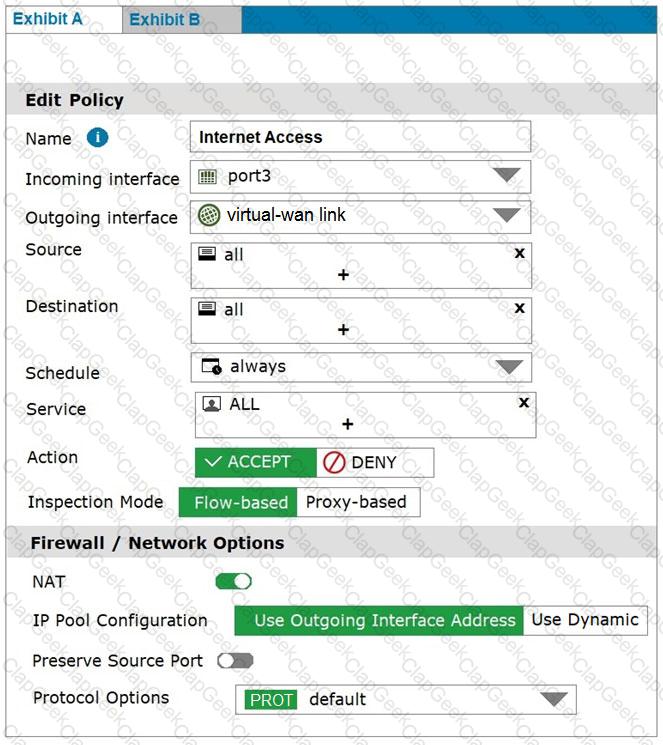
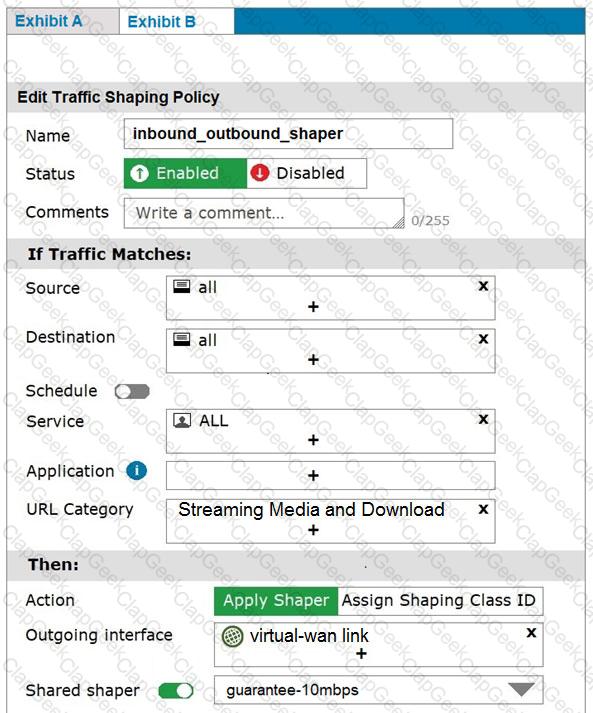
Exhibit A shows the firewall policy and exhibit B shows the traffic shaping policy.
The traffic shaping policy is being applied to all outbound traffic; however, inbound traffic is not being evaluated by the shaping policy.
Based on the exhibits, what configuration change must be made in which policy so that traffic shaping can be applied to inbound traffic?
Which two statements describe how IPsec phase 1 main mode id different from aggressive mode when performing IKE negotiation? (Choose two.)
Which action fortigate performs on the traffic that is subject to a per-IP traffic shaper of 10 Mbps?
Which two protocols in the IPsec suite are most used for authentication and encryption? (Choose two.)
The SD-WAN overlay template helps to prepare SD-WAN deployments. To complete the tasks performed by the SD-WAN overlay template, the administrator must perform some post-run tasks. What are three mandatory post-run tasks that must be performed? (Choose three.)
Refer to the exhibit.
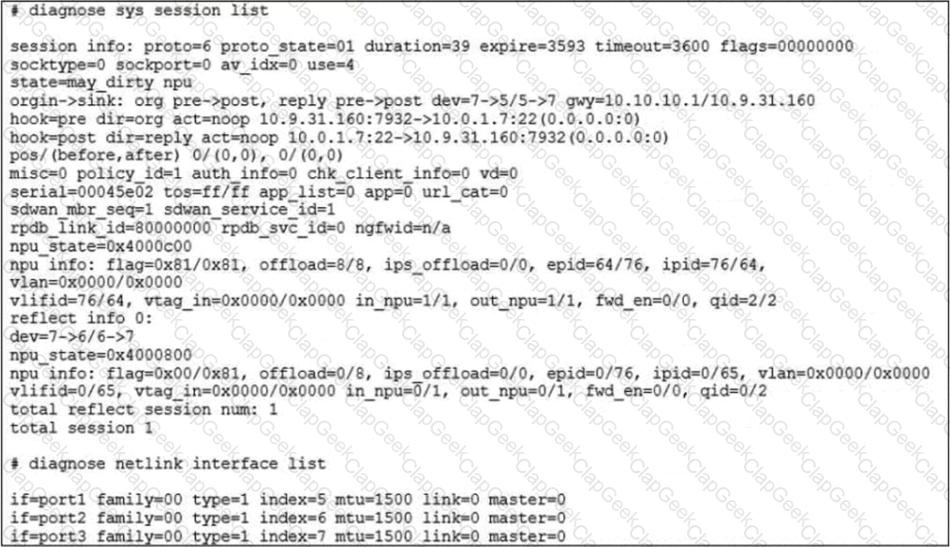
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate appliance that supports hardware offloading. Based on the information shown in the exhibits, which two statements about the session are true? (Choose two.)
Refer to the exhibit.
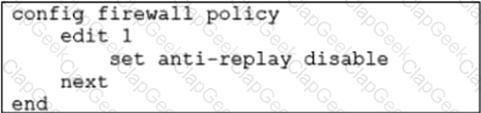
In a dual-hub hub-and-spoke SD-WAN deployment, which is a benefit of disabling theanti-replaysetting on the hubs?
Which two statements describe how IPsec phase 1 main mode is different from aggressive mode when performing IKE negotiation? (Choose two )
Refer to the exhibits.
Exhibit A -
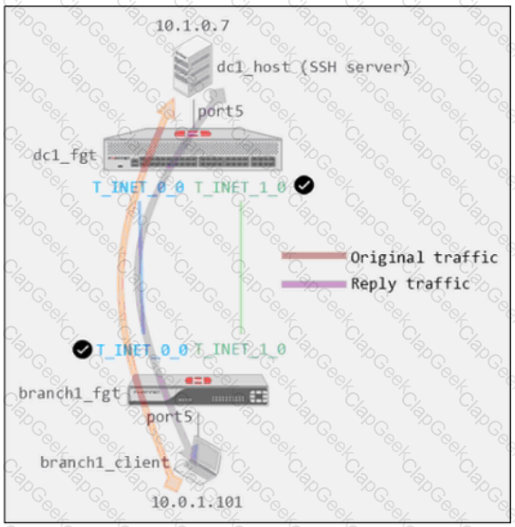
Exhibit B -

Exhibit A shows a site-to-site topology between two FortiGate devices: branch1_fgt and dc1_fgt. Exhibit B shows the system global and system settings configuration on dc1_fgt.
When branch1_client establishes a connection to dc1_host, the administrator observes that, on dc1_fgt, the reply traffic is routed over T_INET_0_0, even though T_INET_1_0 is the preferred member in the matching SD-WAN rule.
Based on the information shown in the exhibits, what configuration change must be made on dc1_fgt so dc1_fgt routes the reply traffic over T_INET_1_0?
Refer to the exhibit.
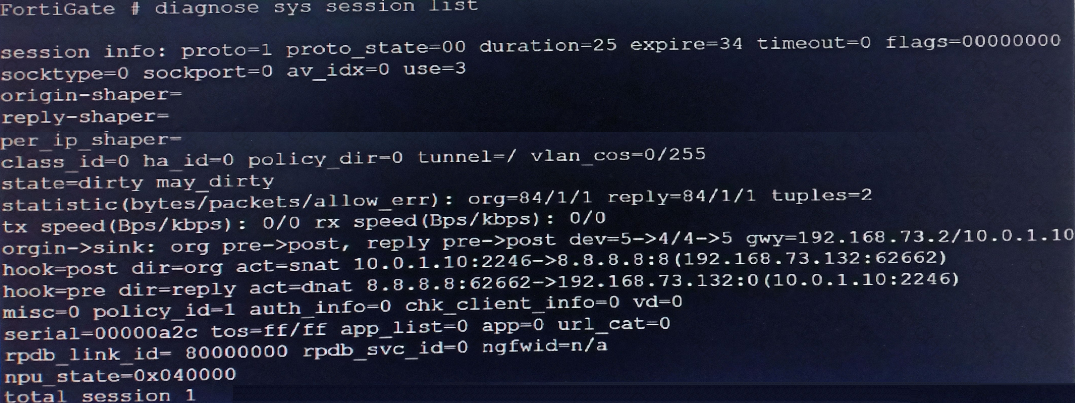
Based on the exhibit, which statement about FortiGate re-evaluating traffic is true?
Refer to the exhibit.
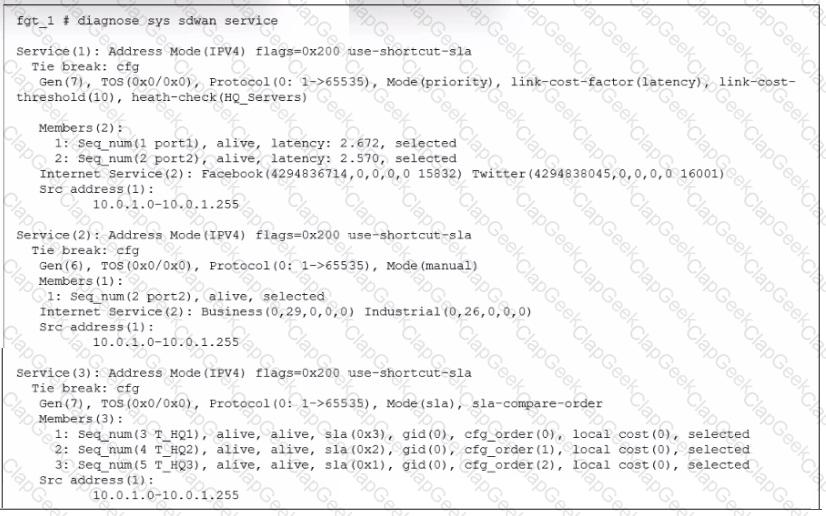
The exhibit shows output of the command diagnose 3vg sdwan service collected on a FortiGate device.
The administrator wants to know through which interface FortiGate will steer the traffic from local users on subnet 10.0.1.0/255.255.255.192 and with a destination of the business application Salesforce located on HO servers 10.0.0.1.
Based on the exhibits, which two statements are correct? (Choose two.)
Which CLI command do you use to perform real-time troubleshooting for ADVPN negotiation?


