Refer to the exhibit.
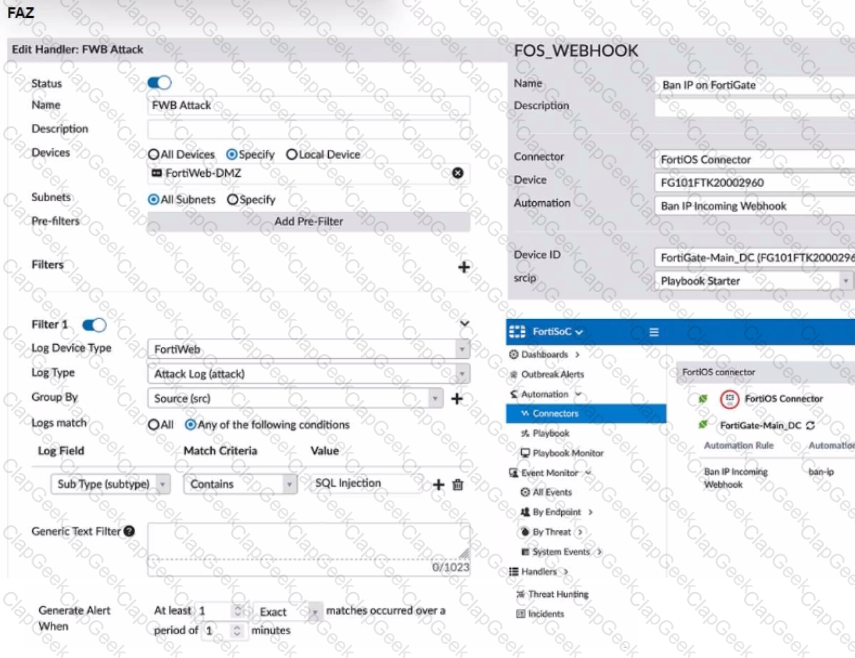
A customer is trying to setup a Playbook automation using a FortiAnalyzer, FortiWeb and FortiGate. The intention is to have the FortiGate quarantine any source of SQL Injection detected by the FortiWeb. They got the automation stitch to trigger on the FortiGate when simulating an attack to their website, but the quarantine object was created with the IP 0.0.0.0. Referring to the configuration and logs in the exhibits, which two statements are true? (Choose two.)
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)
Refer to the exhibit of a FortiNAC configuration.
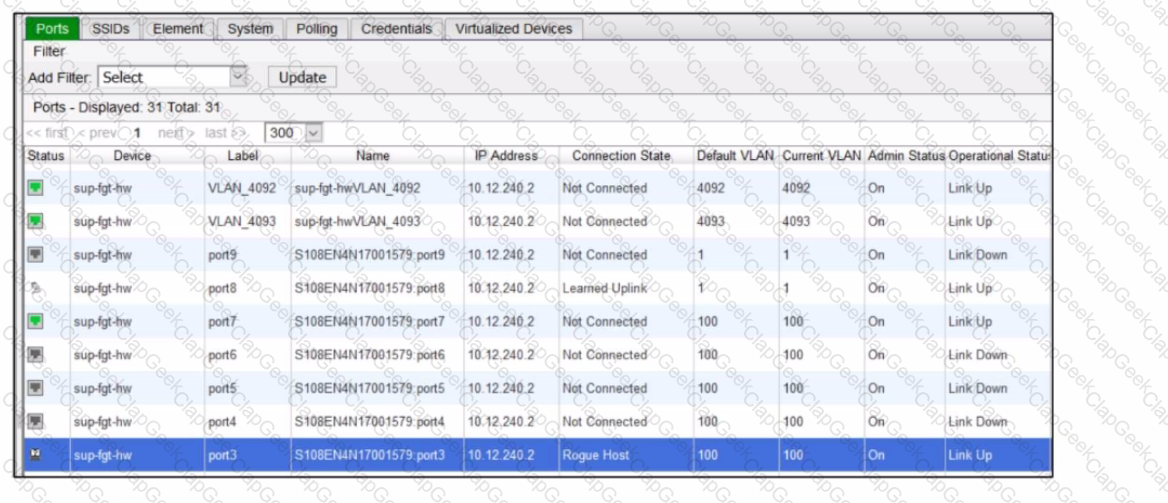
In this scenario, which two statements are correct? (Choose two.)
A customer would like to improve the performance of a FortiGate VM running in an Azure D4s_v3 instance, but they already purchased a BYOL VM04 license.
Which two actions will improve performance the most without making a FortiGate license change? (Choose two.)
Refer to the exhibits.
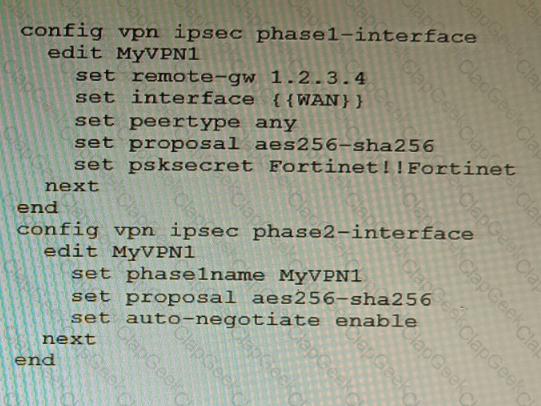
Exhibit A
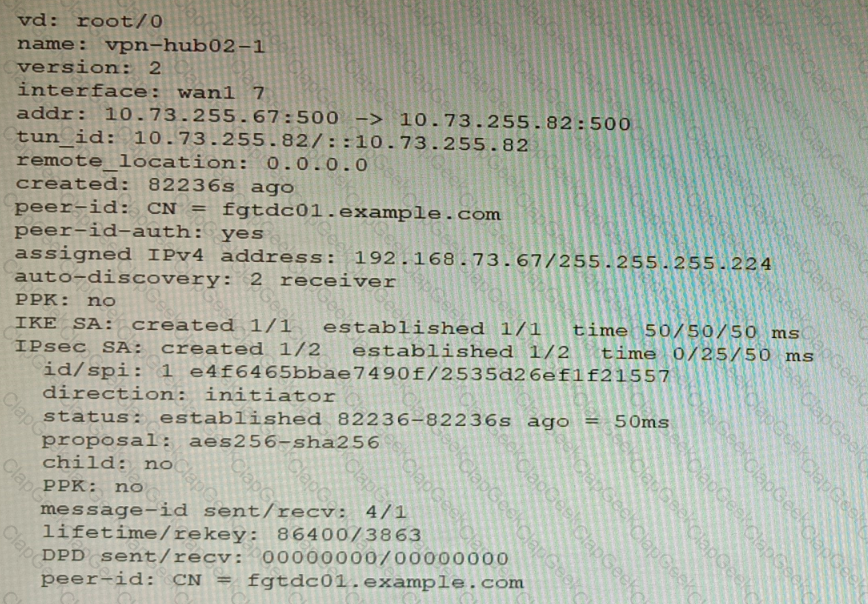
Exhibit B
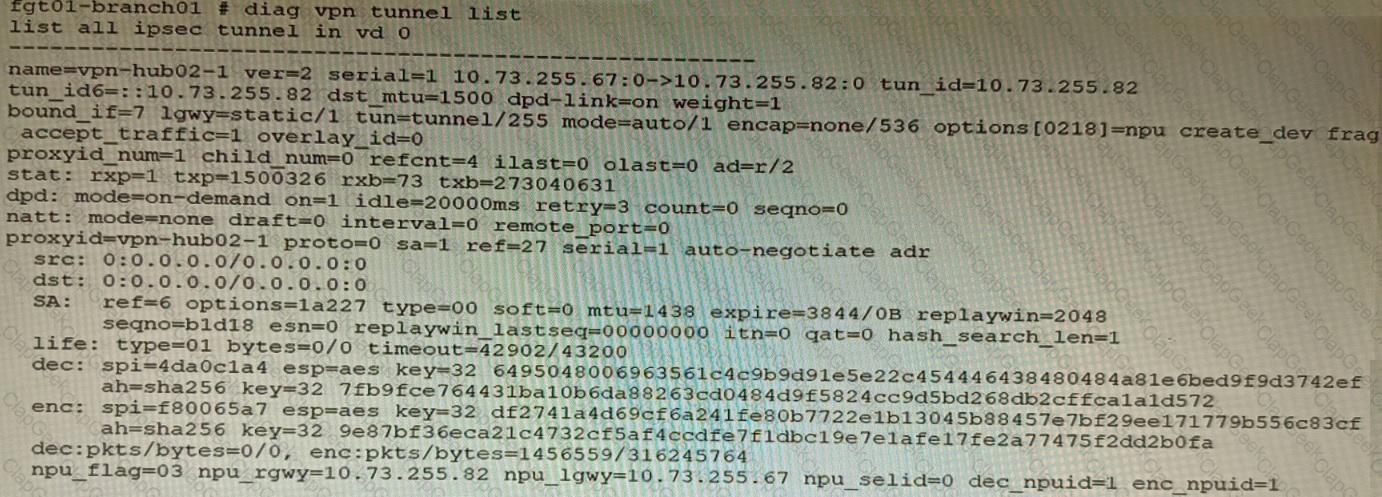
Exhibit C
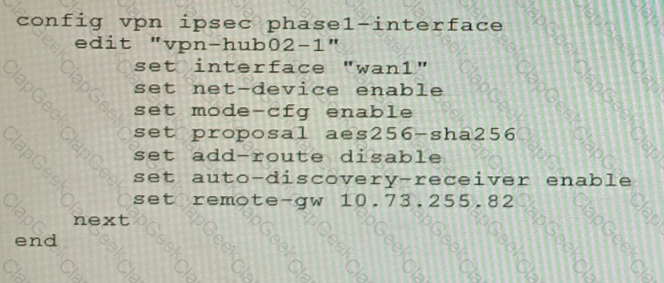
A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
A)
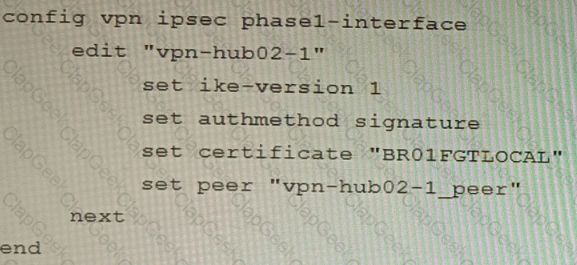
B)
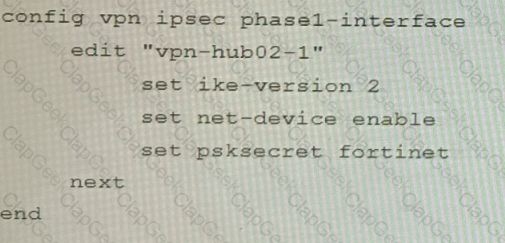
C)
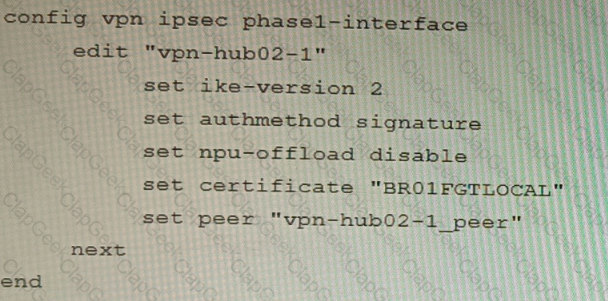
D)
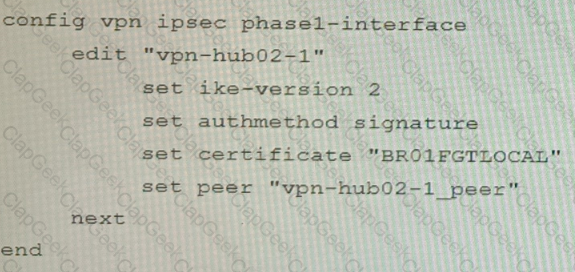
Refer to the exhibit.
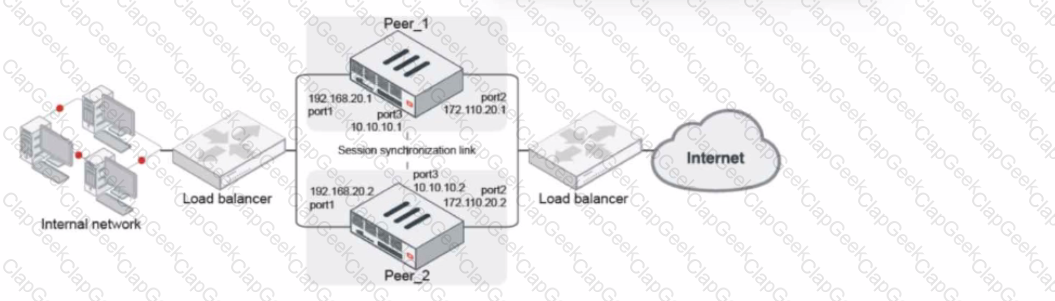
Given the exhibit, which two statements about FortiGate FGSP HA cluster behavior are correct? (Choose two.)
Refer to the exhibit, which shows a Branch1 configuration and routing table.
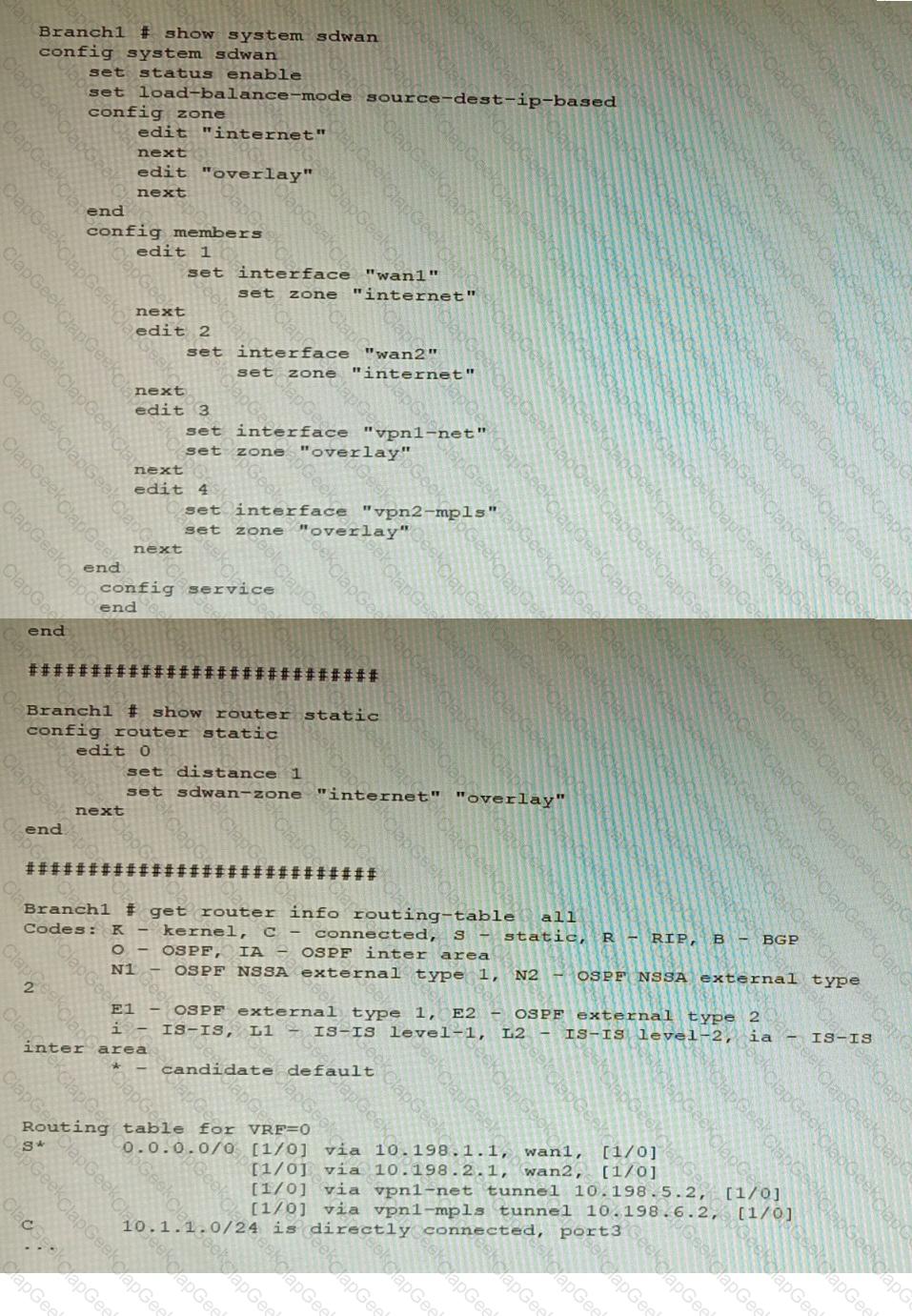
In the SD-WAN implicit rule, you do not want the traffic load balance for the overlay interface when all members are available.
In this scenario, which configuration change will meet this requirement?
Refer to the exhibit, which shows a FortiGate configuration snippet.

A customer in Costa Rica has a FortiGate with SD-WAN configured to use a VPN connection to the United States to browse the internet using a public IP from that country. They would like to enable the SD-WAN rule using a webhook.
Which configuration must be added to the FortiGate, and which type of HTTP request must be used to accomplish this? (Choose two.)
Refer to the exhibit showing an SD-WAN configuration.
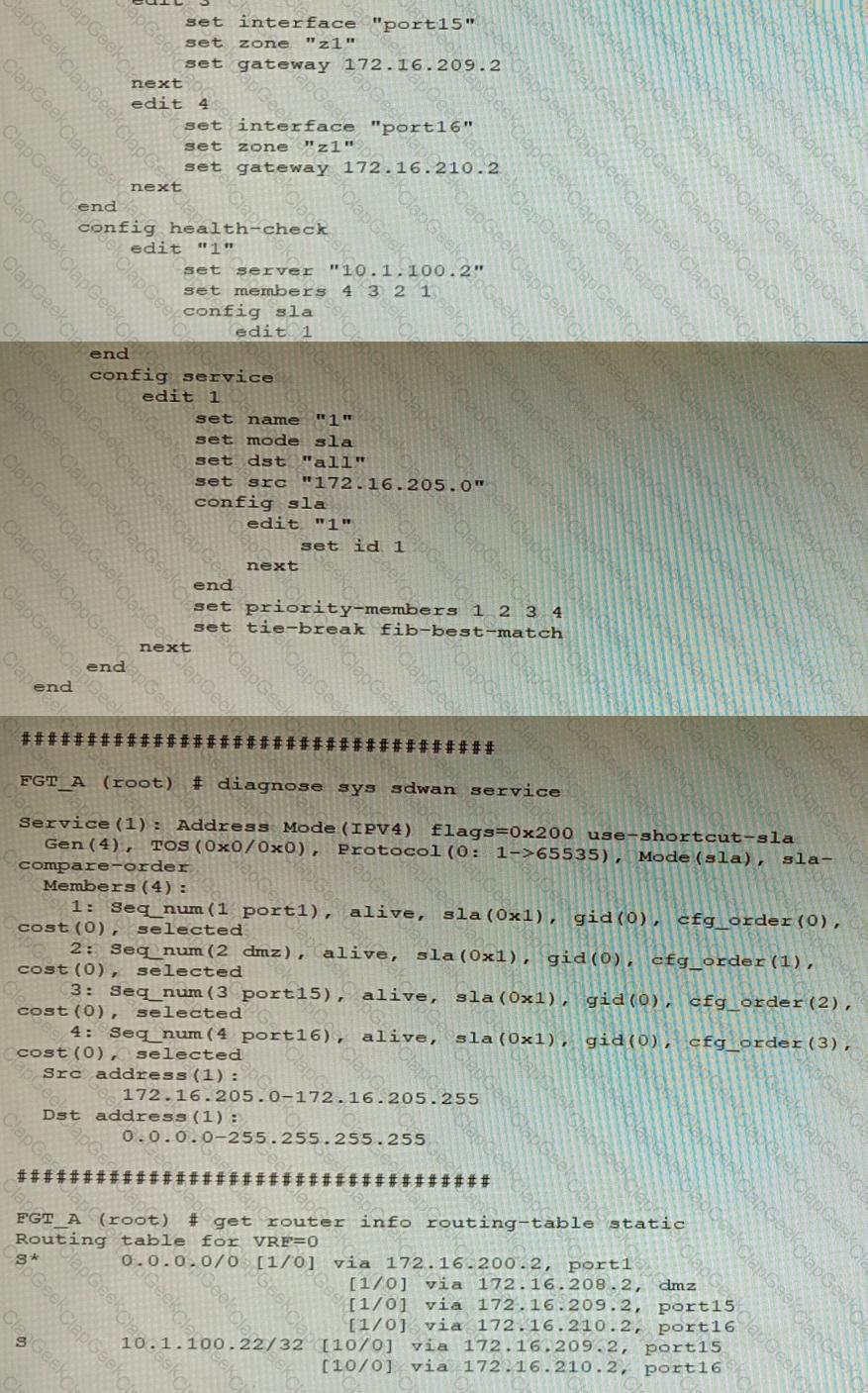
According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
Refer to the exhibit.
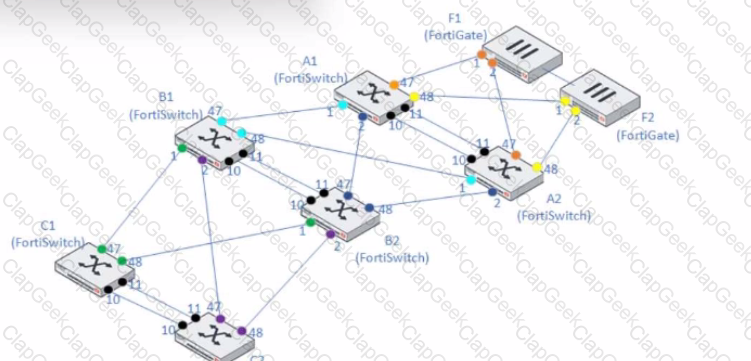
A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?
Refer to the exhibit.
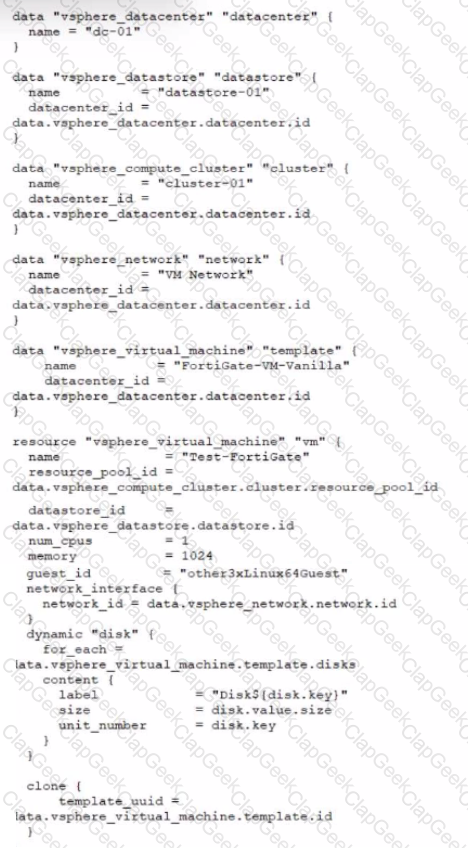
A customer wants to automate the creation and configuration of FortiGate VM instances in a VMware vCenter environment using Terraform. They have the creation part working with the code shown in the exhibit.
Which code snippet will allow Terraform to automatically connect to a newly deployed FortiGate if its IP was dynamically assigned by VMware NSX-T?
Refer to the exhibit.
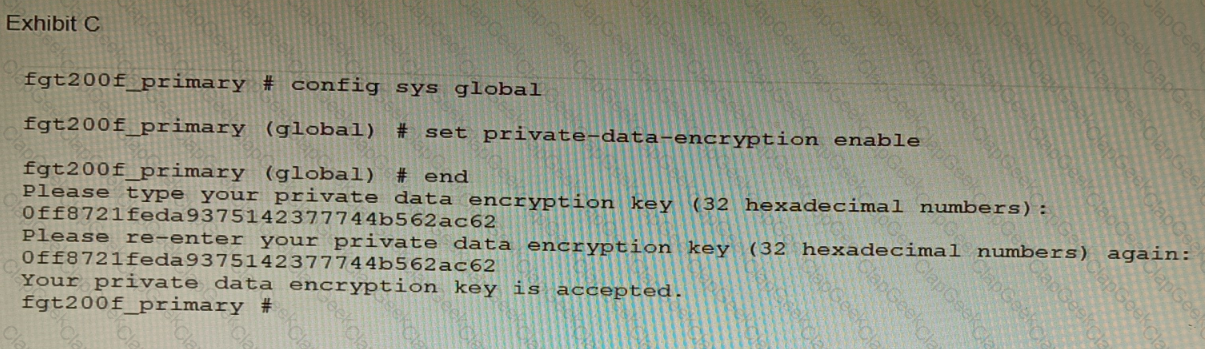
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster. Which statement about this solution is true?
Which two statements about bounce address tagging and verification (BATV) on FortiMail are true? (Choose two.)
On a FortiGate Configured in Transparent mode, which configuration option allows you to control Multicast traffic passing through the?

An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the Online Certificate Status Protocol (OCSP) server.
Part of the FortiGate configuration is shown below:
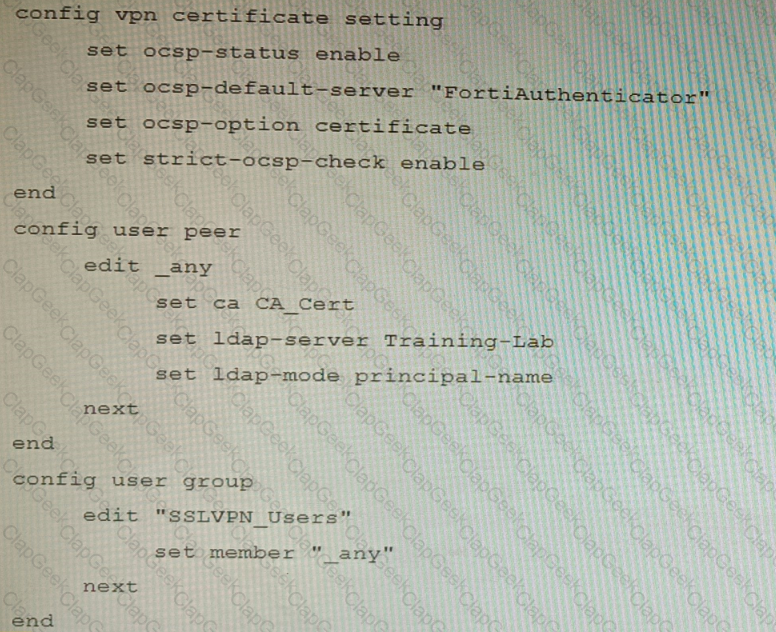
Based on this configuration, which two statements are true? (Choose two.)
Refer to the exhibit, which shows a multi-region SD-WAN architecture.
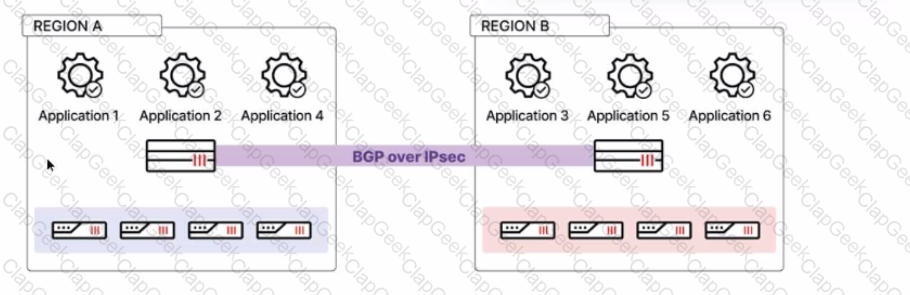
Given this scenario, which two statements are true? (Choose two.)
A customer's cybersecurity department needs to implement security for the traffic between two VPCs in AWS, but these belong to different departments within the company. The company uses a single region for all their VPCs.
Which two actions will achieve this requirement while keeping separate management of each department's VPC? (Choose two.)
Which two types of interface have built-in active bypass in FortiDDoS devices? (Choose two.)
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
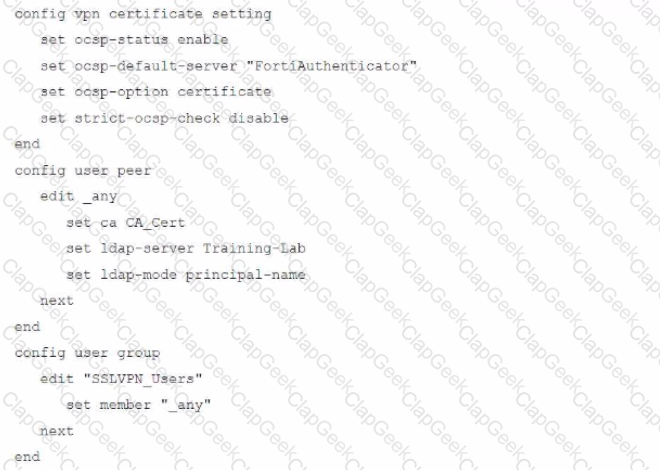
Based on this configuration, which authentication scenario will FortiGate deny?
Refer to the exhibits, which show a topology and diagnostic commands.
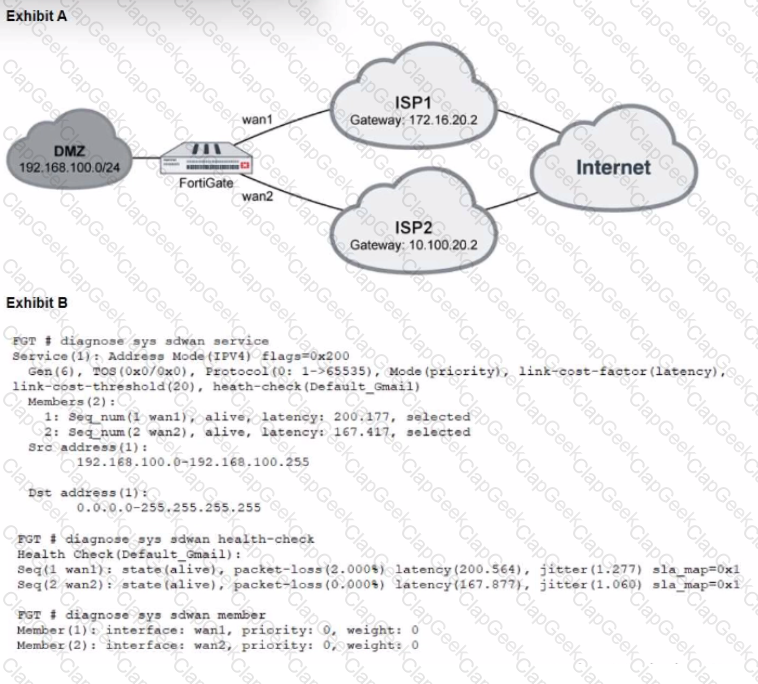
Which two statements about the path resolution are true? (Choose two.)
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG.
Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener.
In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
Refer to the exhibit.
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
Refer to the exhibits.
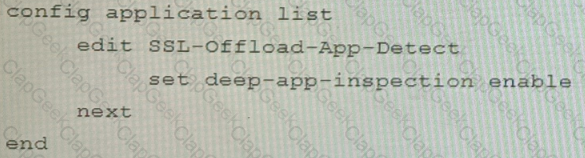
A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)
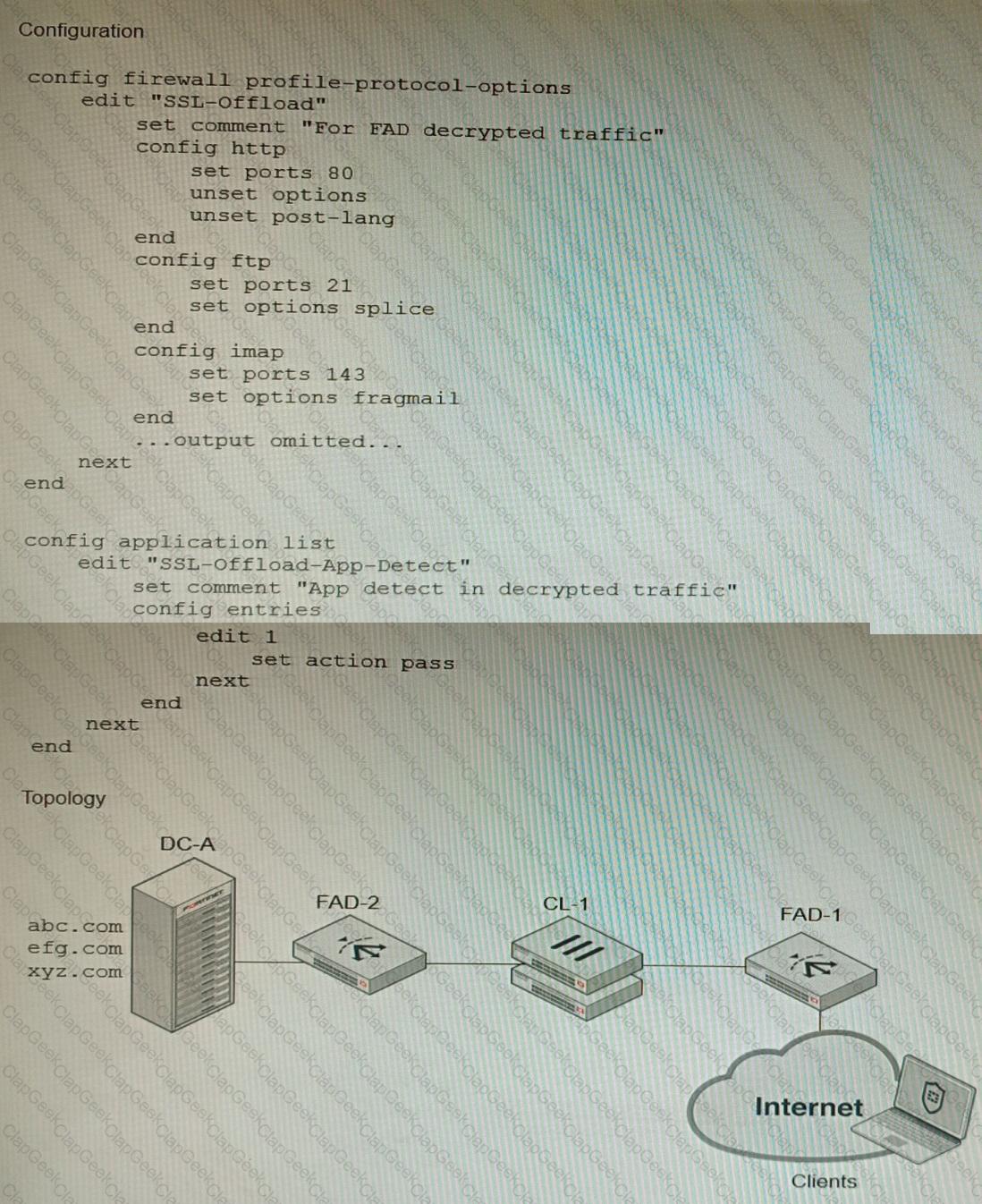
A)
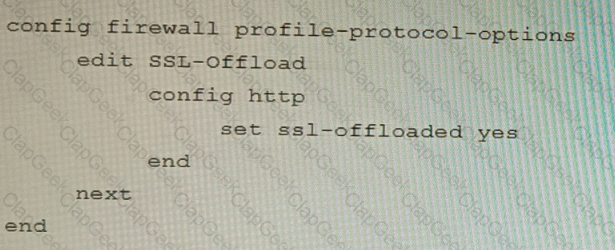
B)
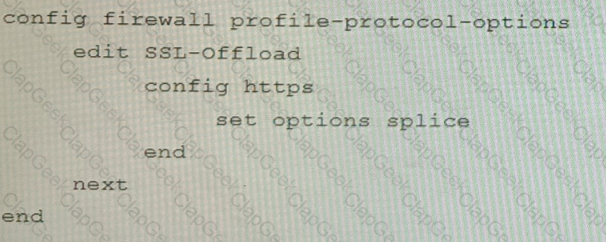
C)
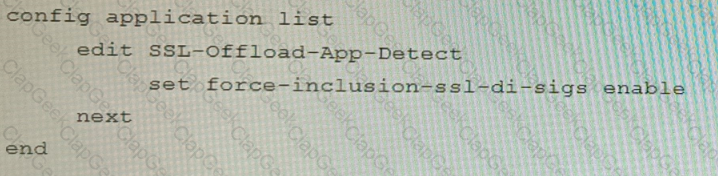
D)
You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:
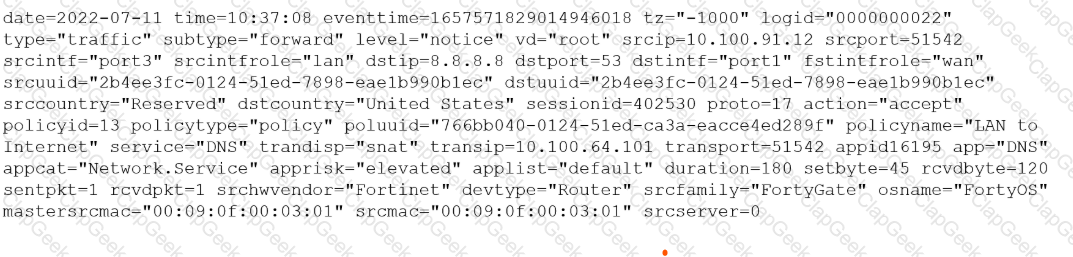
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled
• The FortiGate is at GMT-1000.
• The FortiAnalyzer is at GMT-0800
• Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
Refer to the exhibit showing the history logs from a FortiMail device.
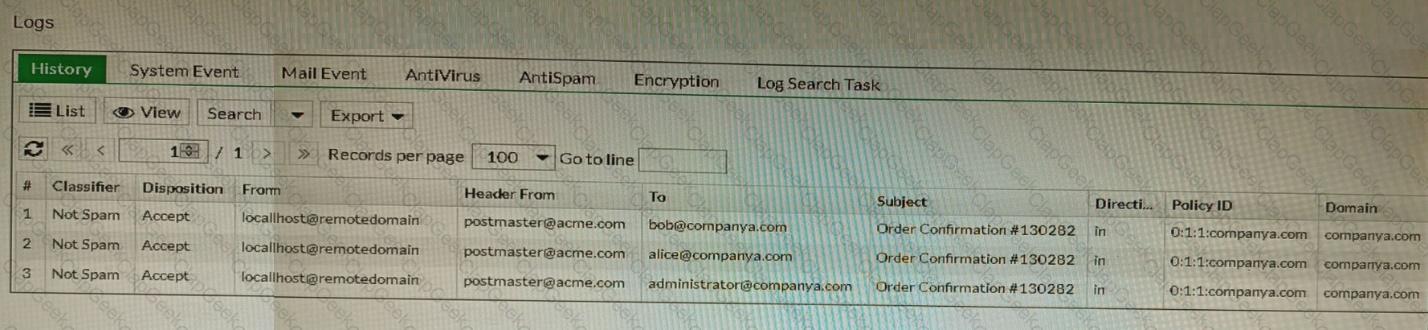
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
You are performing a packet capture on a FortiGate 2600F with the hyperscale licensing installed. You need to display on screen all egress/ingress packets from the port16 interface that have been offloaded to the NP7.
Which three commands need to be run? (Choose three.)


