Review the exhibit.
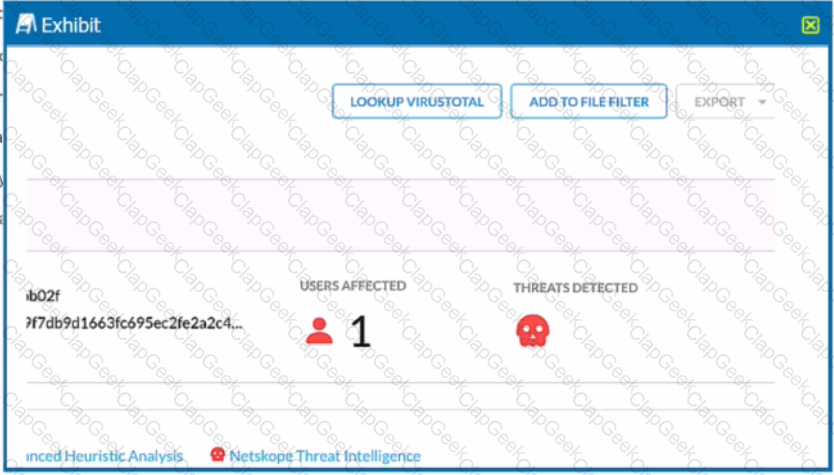
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
You want to prevent a document stored in Google Drive from being shared externally with a public link.
You discover the ongoing use of the native Dropbox client in your organization. Although Dropbox is not a corporate-approved application, you do not want to prevent the use of Dropbox. You do, however, want to ensure visibility into its usage.
You have created a specific Skope IT application events query and want to have the query automatically run and display the results every time you log into your tenant.
Which two statements are correct in this scenario? (Choose two.)
Review the exhibit.
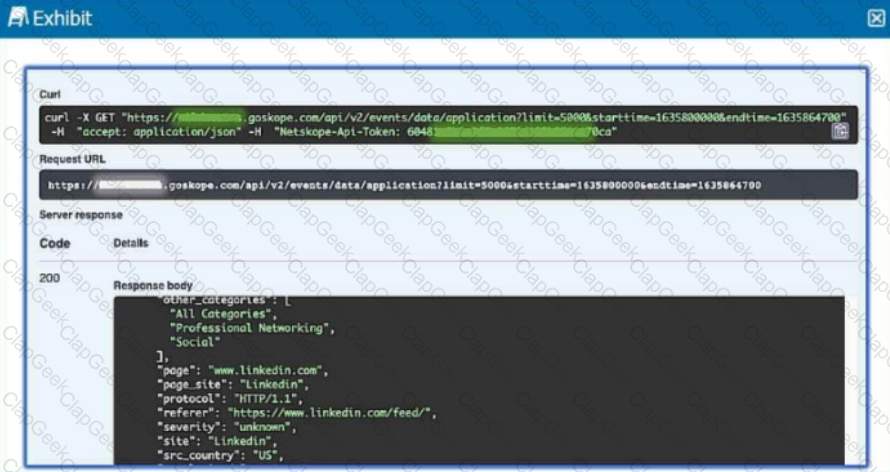
Referring to the exhibit, which three statements are correct? (Choose three.)
An engineering firm is using Netskope DLP to identify and block sensitive documents, including schematics and drawings. Lately, they have identified that when these documents are blocked, certain employees may be taking screenshots and uploading them. They want to block any screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?
You have deployed Netskope Secure Web Gateway (SWG). Users are accessing new URLs that need to be allowed on a daily basis. As an SWG administrator, you are spending a lot of time updating Web policies. You want to automate this process without having to log into the Netskope tenant
Which solution would accomplish this task?
Your IT organization is migrating its user directory services from Microsoft Active Directory to a cloud-based Identity Provider (IdP) solution, Azure AD. You are asked to adapt the Netskope user provisioning process to work with this new cloud-based IdP.
Your organization has three main locations with 30.000 hosts in each location. You are planning to deploy Netskope using iPsec tunnels for security.
What are two considerations to make a successful connection in this scenario? (Choose two.)
You created the Netskope application in your IdP for user provisioning and validated that the API Integration settings are correct and functional. However, you are not able to push the user groups from the IdP into your Netskope tenant.
Your team is asked to investigate ten Netskope DLP incidents. You want to assign these incidents among different team members.
You are an administrator writing Netskope Real-time Protection policies and must determine proper policy ordering.
Which two statements are true in this scenario? (Choose two.)
You want to prevent a document stored in Google Drive from being shared externally with a public link. What would you configure in Netskope to satisfy this requirement?
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated. In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
With Netskope DLP, which feature would be used to detect keywords such as "Confidential" or "Access key"?
Your organization has a homegrown cloud application. You are required to monitor the activities that users perform on this cloud application such as logins, views, and downloaded files. Unfortunately, it seems Netskope is unable to detect these activities by default.
How would you accomplish this goal?
Your customer implements Netskope Secure Web Gateway to secure all Web traffic. While they have created policies to block certain categories, there are many new sites available dally that are not yet categorized. The customer's users need quick access and cannot wait to put in a request to gain access requiring a policy change or have the site's category changed.
To solve this problem, which Netskope feature would provide quick, safe access to these types of sites?
While most Web and SaaS traffic is decrypted for inspection, you are asked to prevent a certain host on the network from SSL decryption for privacy purposes.
You want to allow both the user identities and groups to be imported in the Netskope platform. Which two methods would satisfy this requirement? (Choose two.)
You are implementing tenant access security and governance controls for privileged users. You want to start with controls that are natively available within the Netskope Cloud Security Platform and do not require external or third-party integration.
Which three access controls would you use in this scenario? (Choose three.)
Review the exhibit.
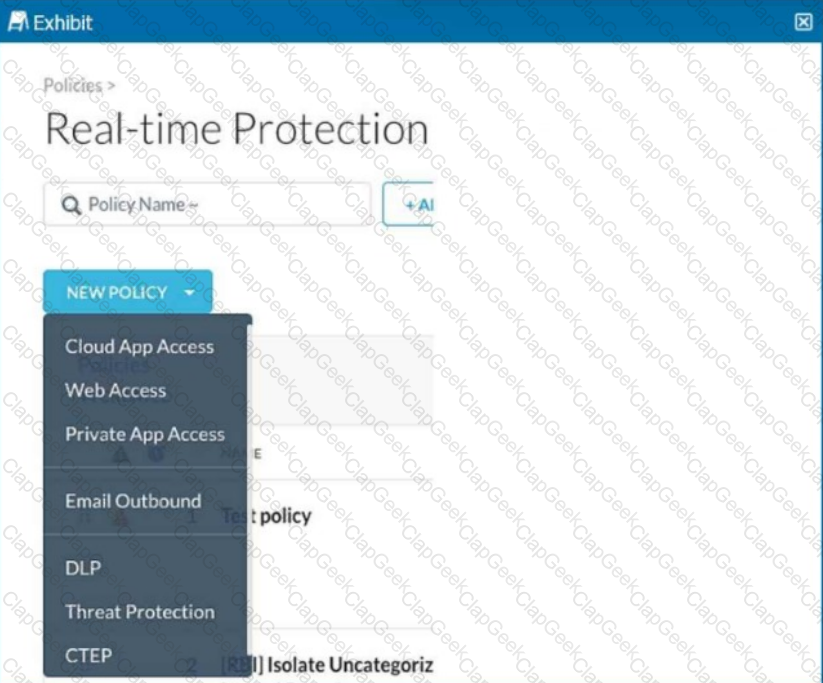
You are asked to create a new Real-time Protection policy to scan SMTP emails using data loss prevention (DLP) for personal health information (PHI). The scope is limited to only emails being sent from Microsoft Exchange Online to outside recipients.
To which three event types does Netskope's REST API v2 provide access? (Choose three.)
A company allows their users to access OneDrive on their managed laptops. It is against corporate policy to upload any documents to their personal OneDrive. The company needs to enforce this policy to protect their customer’s sensitive data.
What are two ways to enforce this policy? (Choose two.)


