Which command is used to add Cortex XSOAR "User1" to an investigation from the War Room command-line interface (CLI)?
What are two ways a customer can configure user authentication access Cortex Xpanse? (Choose two.)
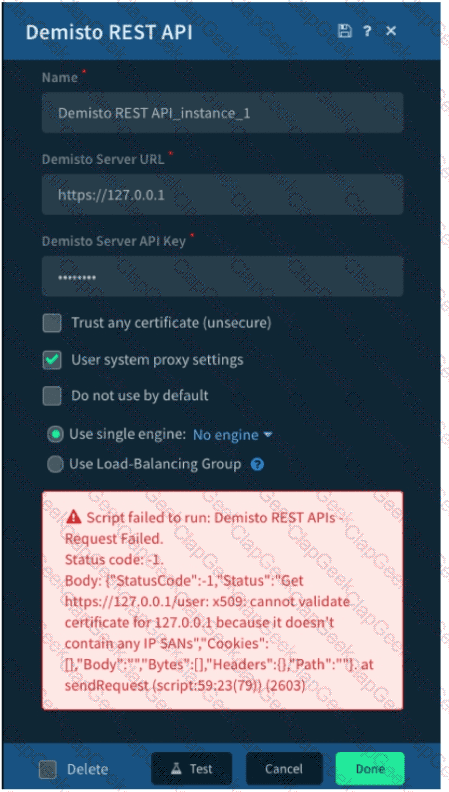
Given the exception thrown in the accompanying image by the Demisto REST API integration, which action would most likely solve the problem?
Which two playbook functionalities allow looping through a group of tasks during playbook execution? (Choose two.)
Cortex XSOAR has extracted a malicious IP address involved in command-and-control traffic.
What is the best method to automatically block this IP from communicating with endpoints without requiring a configuration change on the firewall?
An antivirus refresh project was initiated by the IT operations executive. Who is the best source for discussion about the project's operational considerations'?
What is the difference between the intel feed’s license quotas of Cortex XSOAR Starter Edition and Cortex XSOAR (SOAR + TIM)?
In an Air-Gapped environment where the Docker package was manually installed after the Cortex XSOAR installation which action allows Cortex XSOAR to access Docker?
The prospect is deciding whether to go with a phishing or a ServiceNow use case as part of their POC We have integrations for both but a playbook for phishing only Which use case should be used for the POC?
Which two entities can be created as a behavioral indicator of compromise (BIOC)? (Choose two.)
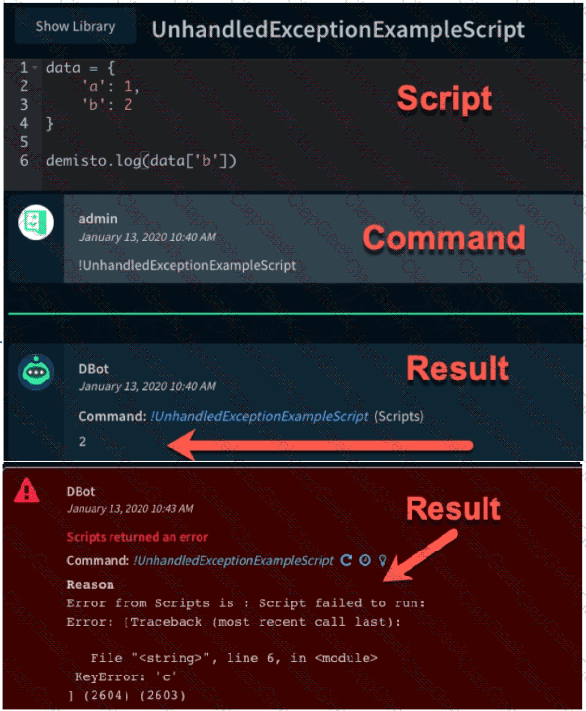
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.)
SUCCESS
A customer has purchased Cortex XSOAR and has a need to rapidly stand up the product in their environment. The customer has stated that their internal staff are currently occupied with other projects.
Which Palo Alto Networks service offering should be recommended to the customer?
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
Which playbook functionality allows grouping of tasks to create functional building blocks?
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
Which three Demisto incident type features can be customized under Settings > Advanced > Incident Types? (Choose three.)
What is the primary mechanism for the attribution of attack surface data in Cortex Xpanse?
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
A Cortex XSOAR customer wants to send a survey to users asking them to input their manager's email for a training use case so the manager can receive status reports on the employee's training. However, the customer is concerned users will provide incorrect information to avoid sending status updates to their manager.
How can Cortex XSOAR most efficiently sanitize user input prior to using the responses in the playbook?
Why is reputation scoring important in the Threat Intelligence Module of Cortex XSOAR?
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
Which two types of lOCs are available for creation in Cortex XDR? (Choose two.)
Which task allows the playbook to follow different paths based on specific conditions?
Which aspect of Cortex Xpanse allows for visibility over remote workforce risks?
The customer has indicated they need EDR data collection capabilities, which Cortex XDR license is required?
Which description applies to the features of the Cortex platform as a holistic ecosystem?
What are two ways Cortex XSIAM monitors for issues with data ingestion? (Choose two.)
Which two actions are required to add indicators to the whitelist? (Choose two.)
Which integration allows searching and displaying Splunk results within Cortex XSOAR?
Which Linux OS command will manually load Docker images onto the Cortex XSOAR server in an air-gapped environment?
Cortex XDR can schedule recurring scans of endpoints for malware. Identify two methods for initiating an on-demand malware scan (Choose two )
Which Cortex XDR capability allows for the immediate termination of a process discovered during investigation of a security event?


