When the Cortex Data Lake is sized for Traps Management Service, which two factors should be considered? (Choose two.)
Which filtering criterion is used to determine users to be included as members of a dynamic user group (DUG)?
A client chooses to not block uncategorized websites.
Which two additions should be made to help provide some protection? (Choose two.)
An administrator wants to justify the expense of a second Panorama appliance for HA of the management layer.
The customer already has multiple M-100s set up as a log collector group. What are two valid reasons for deploying Panorama in High Availability? (Choose two.)
For customers with high bandwidth requirements for Service Connections, what two limitations exist when onboarding multiple Service Connections to the same Prisma Access location servicing a single
Datacenter? (Choose two.)
A customer is concerned about malicious activity occurring directly on their endpoints and will not be visible to their firewalls.
Which three actions does the Traps agent execute during a security event, beyond ensuring the prevention of this activity? (Choose three.)
Which two features are found in a Palo Alto Networks NGFW but are absent in a legacy firewall product? (Choose two.)
When having a customer pre-sales call, which aspects of the NGFW should be covered?
A customer requires an analytics tool with the following attributes:
- Uses the logs on the firewall to detect actionable events on the network
- Automatically processes a series of related threat events that, when combines, indicate a likely comprised host on the network
- Pinpoints the area of risk and allows for assessment of the risk to action can be taken to prevent exploitation of network resources
Which feature of PAN-OS will address these requirements?
Which three items contain information about Command-and-Control (C2) hosts? (Choose three.)
Which three of the following actions must be taken to enable Credential Phishing Prevention? (Choose three.)
Which three methods used to map users to IP addresses are supported in Palo Alto Networks firewalls? (Choose three.)
WildFire can discover zero-day malware in which three types of traffic? (Choose three)
Which three actions should be taken before deploying a firewall evaluation unt in a customer environment? (Choose three.)
Which two tabs in Panorama can be used to identify templates to define a common base configuration? (Choose two.)
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy. Which two features must be enabled to meet the customer's requirements? (Choose two.)
Which four actions can be configured in an Anti-Spyware profile to address command-and-control traffic from compromised hosts? (Choose four.)
How often are the databases for Anti-virus. Application, Threats, and WildFire subscription updated?
What helps avoid split brain in active / passive high availability (HA) pair deployment?
A customer worried about unknown attacks is hesitant to enable SSL decryption due to privacy
and regulatory issues. How does the platform address the customer’s concern?
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
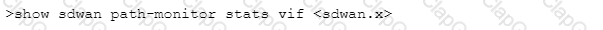
B)

C)
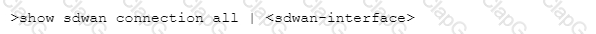
D)

Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
Which Palo Alto Networks pre-sales tool involves approximately 4 hour interview to discuss a customer's current security posture?
A customer with a fully licensed Palo Alto Networks firewall is concerned about threats based on domain generation algorithms (DGAS).
Which Security profile is used to configure Domain Name Security (DNS) to Identity and block
previously unknown DGA-based threats in real time?
Which is the smallest Panorama solution that can be used to manage up to 2500 Palo Alto Networks Next Generation firewalls?
Which two types of security chains are supported by the Decryption Broker? (Choose two.)
Which statement best describes the business value of Palo Alto Networks Zero Touch Provisioning (ZTP)?
The ability to prevent users from resolving internet protocol (IP) addresses to malicious, grayware, or newly registered domains is provided by which Security service?
in which step of the Palo Alto Networks Five-Step Zero Trust Methodology would an organization's critical data, applications, assets, and services (DAAS) be identified?
Which two features can be enabled to support asymmetric routing with redundancy on a Palo
Alto networks next-generation firewall (NGFW)? (Choose two.)
Which statement applies to Palo Alto Networks Single Pass Parallel Processing (SP3)?
Which solution informs a customer concerned about zero-day targeted attacks whether an attack is specifically targeted at its property?


