Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)
Refer to the exhibit.

Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
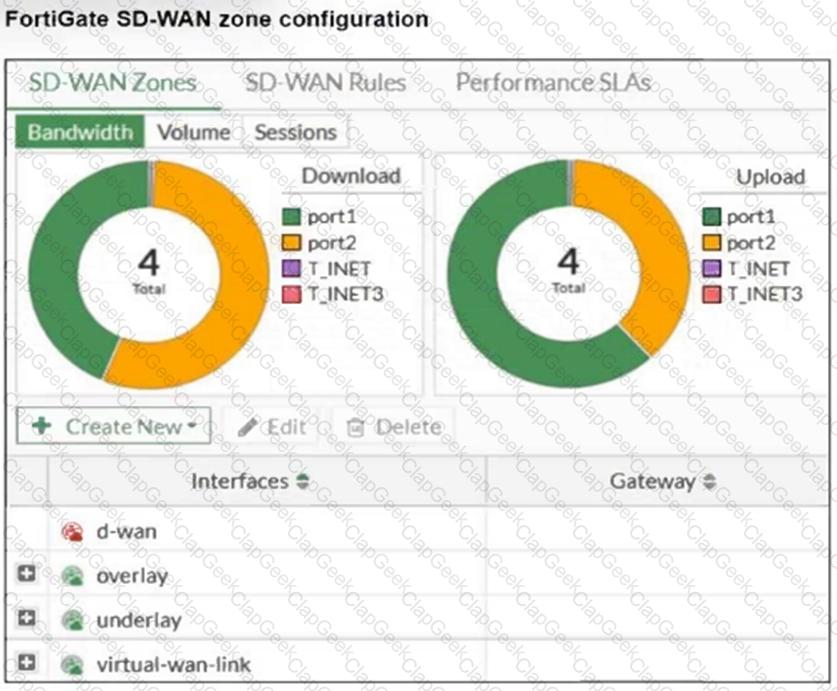
Based on the exhibit, which statement is true?
Refer to the exhibits, which show the firewall policy and an antivirus profile configuration.
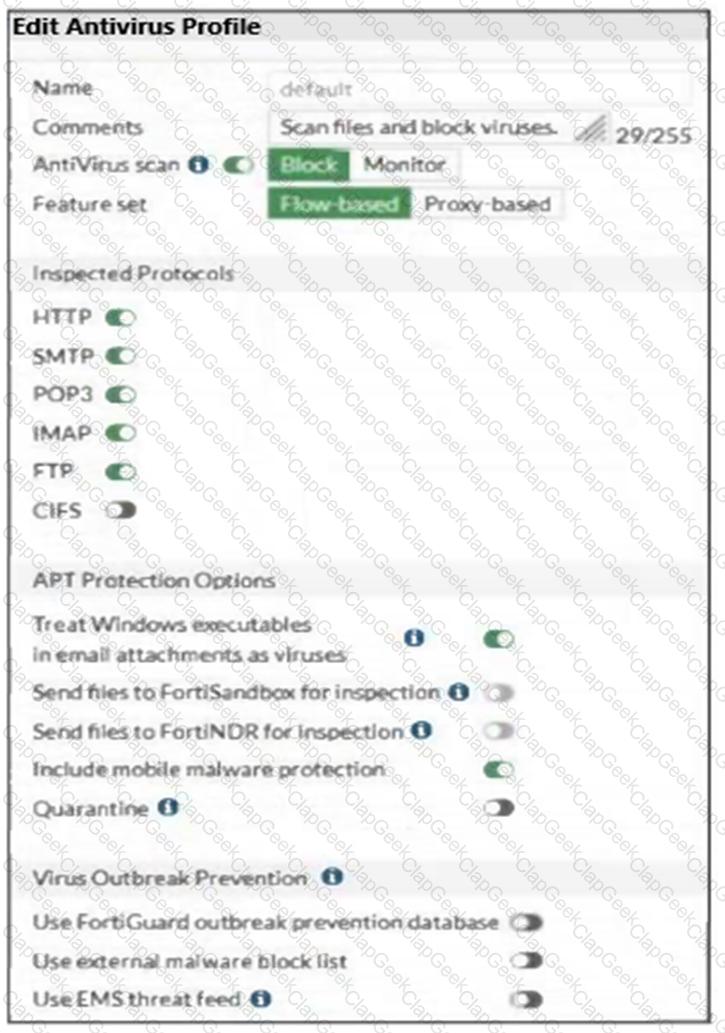
Why is the user unable to receive a block replacement message when downloading an infected file for the first time?
Refer to the exhibit.
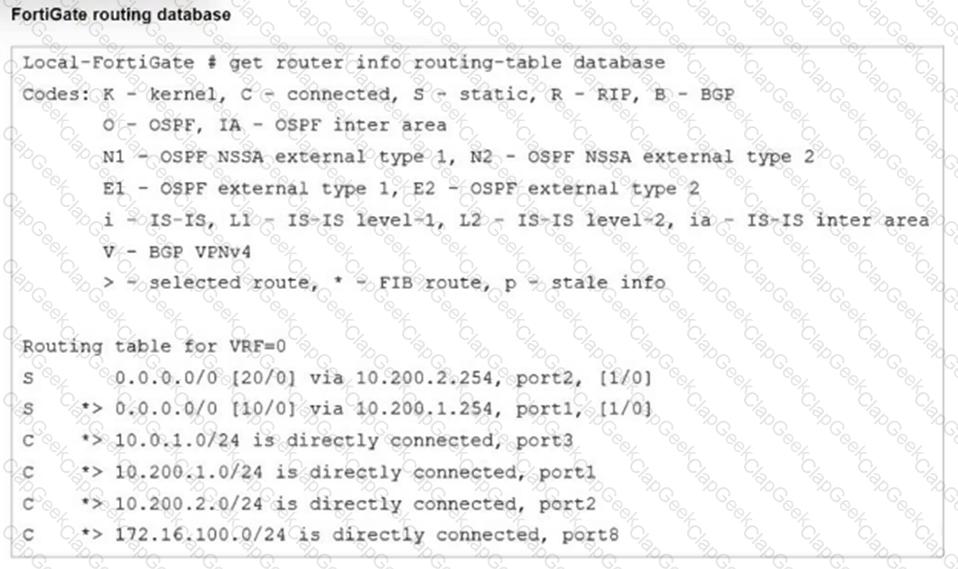
Which two statements are true about the routing entries in this database table? (Choose two.)
Refer to the exhibit showing a debug flow output.
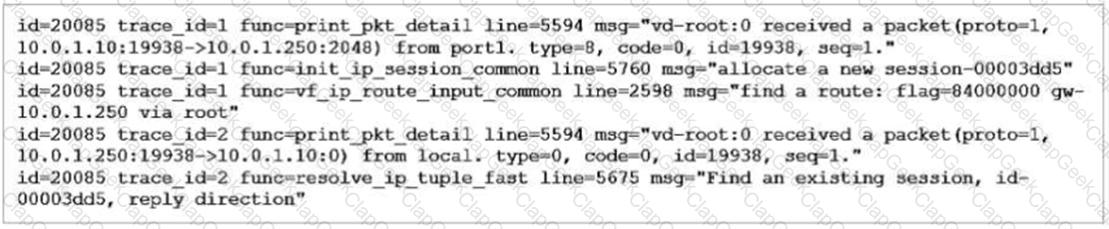
What two conclusions can you make from the debug flow output? (Choose two.)
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Which statement is correct regarding the use of application control for inspecting web applications?
Which two pieces of information are synchronized between FortiGate HA members? (Choose two.)
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
An administrator must enable a DHCP server on one of the directly connected networks on FortiGate. However, the administrator is unable to complete the process on the GUI to enable the service on the interface.
In this scenario, what prevents the administrator from enabling DHCP service?
Refer to the exhibit.
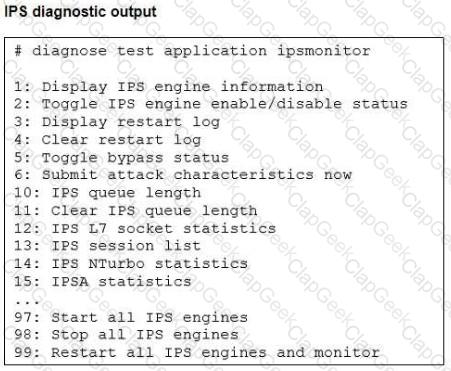
Examine the intrusion prevention system (IPS) diagnostic command shown in the exhibit.
If option 5 is used with the IPS diagnostic command and the outcome is a decrease in the CPU usage, what is the correct conclusion?
An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
Refer to the exhibit.
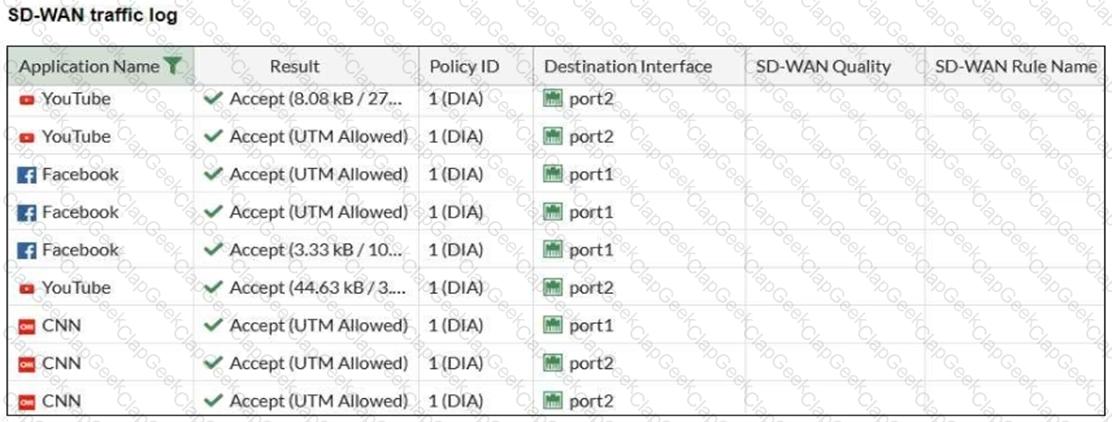
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?
An administrator has configured a strict RPF check on FortiGate.
How does strict RPF check work?
What is the primary FortiGate election process when the HA override setting is disabled?
Refer to the exhibit.
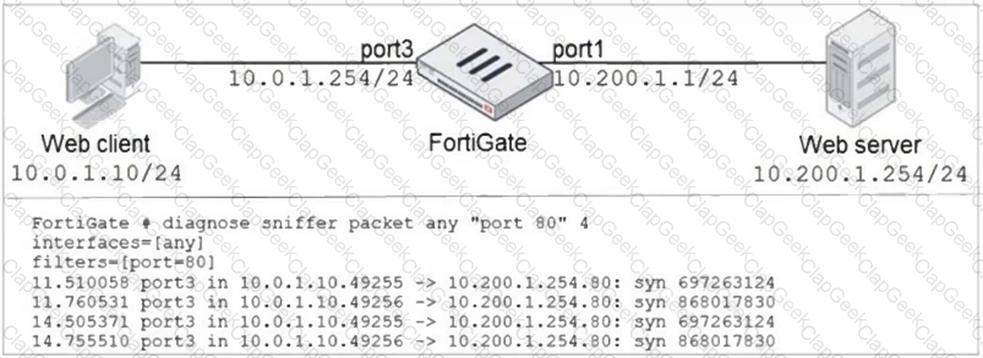
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two.)


